Resources
Find the latest news & updates on AWS

Cloudtech Has Earned AWS Advanced Tier Partner Status
We’re honored to announce that Cloudtech has officially secured AWS Advanced Tier Partner status within the Amazon Web Services (AWS) Partner Network!
We’re honored to announce that Cloudtech has officially secured AWS Advanced Tier Partner status within the Amazon Web Services (AWS) Partner Network! This significant achievement highlights our expertise in AWS cloud modernization and reinforces our commitment to delivering transformative solutions for our clients.
As an AWS Advanced Tier Partner, Cloudtech has been recognized for its exceptional capabilities in cloud data, application, and infrastructure modernization. This milestone underscores our dedication to excellence and our proven ability to leverage AWS technologies for outstanding results.
A Message from Our CEO
“Achieving AWS Advanced Tier Partner status is a pivotal moment for Cloudtech,” said Kamran Adil, CEO. “This recognition not only validates our expertise in delivering advanced cloud solutions but also reflects the hard work and dedication of our team in harnessing the power of AWS services.”
What This Means for Us
To reach Advanced Tier Partner status, Cloudtech demonstrated an in-depth understanding of AWS services and a solid track record of successful, high-quality implementations. This achievement comes with enhanced benefits, including advanced technical support, exclusive training resources, and closer collaboration with AWS sales and marketing teams.
Elevating Our Cloud Offerings
With our new status, Cloudtech is poised to enhance our cloud solutions even further. We provide a range of services, including:
- Data Modernization
- Application Modernization
- Infrastructure and Resiliency Solutions
By utilizing AWS’s cutting-edge tools and services, we equip startups and enterprises with scalable, secure solutions that accelerate digital transformation and optimize operational efficiency.
We're excited to share this news right after the launch of our new website and fresh branding! These updates reflect our commitment to innovation and excellence in the ever-changing cloud landscape. Our new look truly captures our mission: to empower businesses with personalized cloud modernization solutions that drive success. We can't wait for you to explore it all!
Stay tuned as we continue to innovate and drive impactful outcomes for our diverse client portfolio.

What is Amazon S3, and why should it be a part of data strategy for SMBs?
Amazon S3 (Simple Storage Service) has become a cornerstone of modern data strategies, with over 400 trillion objects stored and the capacity to handle 150 million requests per second. It underpins mission-critical workloads across industries, from storage and backup to analytics and application delivery.
For small and mid-sized businesses (SMBs), Amazon S3 offers more than just scalable cloud storage. It enables centralized data access, reduces infrastructure overhead, and supports long-term agility. By integrating Amazon S3 into their data architecture, SMBs can simplify operations, strengthen security, and accelerate digital initiatives without the complexity of managing hardware.
This article explores the core features of Amazon S3, its architectural advantages, and why it plays a critical role in helping SMBs compete in an increasingly data-driven economy.
Key takeaways:
- Amazon S3 scales automatically without performance loss: Built-in request scaling, intelligent partitioning, and unlimited storage capacity allow S3 to handle large workloads with no manual effort.
- Performance can be improved with proven techniques: Strategies like randomized prefixes, multipart uploads, and parallel processing significantly increase throughput and reduce latency.
- Storage classes directly impact performance and cost: Choosing between S3 Standard, Intelligent-Tiering, Glacier, and others helps balance retrieval speed, durability, and storage pricing.
- Integrations turn S3 into a complete data platform: Using services like CloudFront, Athena, Lambda, and Macie expands S3’s role from storage to analytics, automation, and security.
- Cloudtech delivers scalable, resilient S3 implementations: Through data modernization, application integration, and infrastructure design, Cloudtech helps businesses build optimized cloud systems.
What is Amazon S3?
Amazon S3 is a cloud object storage service built to store and retrieve any amount of data from anywhere. It is designed for high durability and availability, supporting a wide range of use cases such as backup, data archiving, content delivery, and analytics.
It uses an object-based storage architecture that offers more flexibility and scalability than traditional file systems, with the following key features:

- Objects: Each file (regardless of type or size) is stored as an object, which includes the data, metadata, and a unique identifier.
- Buckets: Objects are grouped into buckets, which serve as storage containers. Each bucket must have a globally unique name across AWS.
- Keys: Every object is identified by a key, which functions like a file path to locate and retrieve the object within a bucket.
Buckets can store objects up to 5 TB in size, making it ideal for high-volume workloads such as medical imaging, logs, or backups. It allows businesses to scale storage on demand without managing servers or provisioning disk space.
For healthcare SMBs, this architecture is particularly useful when storing large volumes of imaging files, patient records, or regulatory documentation. Data can be encrypted at rest using AWS Key Management Service (AWS KMS), with versioning and access control policies to support compliance with HIPAA or similar standards.
Note: Many SMBs also use Amazon S3 as a foundation for data lakes, web hosting, disaster recovery, and long-term retention strategies. Since it integrates natively with services like Amazon CloudWatch (for monitoring), AWS Backup (for automated backups), and Amazon S3 Glacier (for archival), teams can build a full storage workflow without additional tools or manual effort.

How does Amazon S3 help SMBs improve scalability and performance?
For SMBs, especially those in data-intensive industries like healthcare, scalability and speed are operational necessities. Whether it’s securely storing patient records, streaming diagnostic images, or managing years of compliance logs, Amazon S3 offers the architecture and automation to handle these demands without requiring an enterprise-sized IT team.
The scalable, high-performance storage capabilities of Amazon S3 are backed by proven use cases that show why it needs to be a part of data strategy for SMBs:
1. Scale with growing data—no reconfiguration needed
For example, a mid-sized radiology center generates hundreds of high-resolution DICOM files every day. Instead of provisioning new storage hardware as data volumes increase, the center uses Amazon S3 to automatically scale its storage footprint without downtime or administrative overhead.
- No upfront provisioning is required since storage grows dynamically.
- Upload throughput stays consistent, even as the object count exceeds millions.
- Data is distributed automatically across storage nodes and zones.
2. Fast access to critical data with intelligent partitioning
Speed matters for business efficiency, and this is especially true for SMBs in urgent care settings. Amazon S3 partitions data behind the scenes using object key prefixes, allowing hospitals or clinics to retrieve lab results or imaging files quickly, even during peak operational hours.
- Object keys like /radiology/2025/07/CT-Scan-XYZ.dcm help structure storage and maximize retrieval speed.
- Performance scales independently across partitions, so multiple departments can access their data simultaneously.
3. Resiliency built-in: zero data loss from zone failure
Amazon S3 stores copies of data across multiple Availability Zones (AZs) within a region. For example, a healthcare SMB running in the AWS Asia Pacific (Mumbai) Region can rely on Amazon S3 to automatically duplicate files across AZs, ensuring continuity if one zone experiences an outage.
- Supports 99.999999999% (11 9s) durability.
- Eliminates the need for manual replication scripts or redundant storage appliances.
4. Lifecycle rules keep storage lean and fast
Over time, SMBs accumulate large volumes of infrequently accessed data, such as insurance paperwork or compliance archives. Amazon S3’s lifecycle policies automatically transition such data to archival tiers like Amazon S3 Glacier or S3 Glacier Deep Archive, freeing up performance-optimized storage.
For example, a diagnostic lab sets rules to transition monthly lab reports to Glacier after 90 days, cutting storage costs by up to 70% without losing access.
5. Supporting version control and rollback
In clinical research, file accuracy and traceability are paramount. S3 versioning automatically tracks every change to files, helping SMBs revert accidental changes or retrieve historical snapshots of reports.
- Researchers can compare versions of a study submitted over multiple weeks.
- Deleted objects can be restored instantly without the need for manual backups.
6. Global scalability for multi-location clinics
An expanding healthcare provider with branches across different states uses Cross-Region Replication (CRR) to duplicate key records from one region to another. This supports faster access for backup recovery and complies with future international data residency goals.
- Low-latency access for geographically distributed teams.
- Supports business continuity and audit-readiness.
Why does this matter for SMBs? Unlike legacy NAS or file server systems, Amazon S3’s performance scales automatically with usage. There is no need for manual intervention or costly upgrades. Healthcare SMBs, often constrained by limited IT teams and compliance demands, gain a resilient, self-healing storage layer that responds in real time to changing data patterns and operational growth.

Choosing the right Amazon S3 storage option

Choosing the right Amazon S3 storage classes is a strategic decision for SMBs managing growing volumes of operational, compliance, and analytical data. Each class is designed to balance access speed and cost, allowing businesses to scale storage intelligently based on how often they need to retrieve their data.
Here’s how different storage classes apply to common SMB use cases:
- Amazon S3 Standard
Amazon S3 Standard offers low latency, high throughput, and immediate access to data, ideal for workloads where performance can’t be compromised.
Best for: Active patient records, real-time dashboards, business-critical applications
Example: A healthcare diagnostics provider hosts an internal dashboard that physicians use to pull lab reports during consultations. These reports must load instantly, regardless of traffic spikes or object size. With S3 Standard, the team avoids lag and ensures service consistency, even during peak hours.
Key features:
- Millisecond retrieval time
- Supports unlimited requests per second
- No performance warm-up period
- Higher storage cost, but no retrieval fees
- Amazon S3 Intelligent-Tiering
Amazon S3 Intelligent-Tiering automatically moves data between storage tiers based on usage. It maintains high performance without manual tuning.
Best for: Patient imaging data, vendor contracts, internal documentation with unpredictable access
Example: A mid-sized healthcare SMB stores diagnostic images (X-rays, MRIs) that may be accessed intensively for a few weeks after scanning, then rarely afterwards. Intelligent tiering ensures that these files stay in high-performance storage during peak use and then move to lower-cost archival tiers, eliminating the need for IT teams to manually monitor them.
Key features:
- No retrieval fees or latency impact
- Optimizes cost over time automatically
- Ideal for compliance retention data with unpredictable access patterns
- Amazon S3 Express One Zone
Amazon S3 Express One Zone is designed for high-speed access in latency-sensitive environments and stores data in a single Availability Zone.
Best for: Time-sensitive data processing pipelines in a fixed location
Example: A healthtech company running real-time analytics for wearables or IoT-enabled patient monitors can’t afford multi-zone latency. By colocating its compute workloads with Amazon S3 Express One Zone, it reduces data transfer delays and supports near-instant response times.
Key features:
- Microsecond latency within the same AZ
- Lower cost compared to multi-zone storage
- Suitable for applications where region-level fault tolerance is not required
- Amazon S3 Glacier
Amazon S3 Glacier is built for cost-effective archival. It supports various retrieval speeds depending on business urgency.
Best for: Long-term audit data, old medical records, regulatory logs
Example: A diagnostics company stores seven years of HIPAA-regulated medical reports for compliance. They rarely need to retrieve this data—but when an audit request comes in, they can choose between low-cost bulk recovery or faster expedited retrieval based on deadlines.
- Lowest storage cost among archival options
- Retrieval times: 1 minute to 12 hours
- Best for data you must keep, but rarely access
- Amazon S3 Glacier Instant Retrieval
This storage class offers Amazon S3 Standard-level performance for archives, but at a lower cost.
Best for: Medical archives that may need quick access without full S3 Standard pricing
Example: A healthcare network archives mammogram images that may need to be retrieved within seconds if a patient returns after several months. Glacier Instant Retrieval balances cost and speed, keeping storage efficient while maintaining instant availability.
Key features:
- Millisecond access times
- Supports lifecycle rules for auto-transition from S3 Standard
- Ideal for rarely accessed data with occasional urgent retrieval needs
Before choosing a storage option, here are some factors that SMB decision-makers should consider:
Pro tip: SMBs can also work with AWS partners like Cloudtech to map data types to appropriate storage classes.

How does Amazon S3 integrate with other AWS services?

For SMBs, Amazon S3 becomes far more than a storage solution when combined with other AWS services. These integrations help streamline operations, automate workflows, improve security posture, and unlock deeper business insights.
Below are practical ways SMBs can integrate S3 with other AWS services to improve efficiency and performance:
- Faster content delivery with Amazon CloudFront
SMBs serving content to customers across regions can connect Amazon S3 to Amazon CloudFront, AWS’s content delivery network (CDN).
How it works: Amazon S3 acts as the origin, and Amazon CloudFront caches content in AWS edge locations to reduce latency.
Example: A regional telehealth provider uses Amazon CloudFront to quickly deliver patient onboarding documents stored in Amazon S3 to remote clinics, improving access speed by over 40%.
- On-demand data querying with Amazon Athena
Amazon Athena lets teams run SQL queries directly on Amazon S3 data without moving it into a database.
How it helps: No need to manage servers or build data pipelines. Just point Amazon Athena to Amazon S3 and start querying.
Example: A diagnostics lab uses Athena to run weekly reports on CSV-formatted test results stored in S3, without building custom ETL jobs or infrastructure.
- Event-driven automation using AWS Lambda
AWS Lambda can be triggered by Amazon S3 events, like new file uploads, to automate downstream actions.
Use case: Auto-processing medical images, converting formats, or logging uploads in real-time.
Example: When lab reports are uploaded to a specific Amazon S3 bucket, an AWS Lambda function instantly routes them to the right physician based on metadata.
- Centralized backup and archival with AWS Backup and S3 Glacier
Amazon S3 integrates with AWS Backup to enforce organization-wide backup policies and automate lifecycle transitions.
Benefits: Meets long-term retention requirements, such as HIPAA or regional health regulations, without manual oversight.
Example: A healthcare SMB archives historical patient data from Amazon S3 to Amazon S3 Glacier Deep Archive, retaining compliance while cutting storage costs by 40%.
- Strengthened data security with Amazon Macie and Amazon GuardDuty
Amazon Macie scans S3 for sensitive information like PHI or PII, while Amazon GuardDuty detects unusual access behavior.
How it helps: Flags risks early and reduces the chance of breaches.
Example: A health records company uses Amazon Macie to monitor Amazon S3 buckets for unencrypted PHI uploads. Amazon GuardDuty alerts the team if unauthorized access attempts are made.
These integrations make Amazon S3 a foundational service in any SMB’s modern cloud architecture. When configured correctly, they reduce operational burden, improve security, and unlock value from stored data without adding infrastructure complexity.
Pro tip: AWS Partners like Cloudtech help SMBs set up a well-connected AWS ecosystem that’s aligned with their business goals. They ensure services like Amazon S3, Amazon CloudFront, Amazon Athena, AWS Lambda, and AWS Backup are configured securely and work together efficiently. From identity setup to event-driven workflows and cost-optimized storage, they help SMBs reduce manual overhead and accelerate value, without needing deep in-house cloud expertise.
Best practices SMBs can follow to optimize Amazon S3 benefits
For small and mid-sized businesses, maximizing both time and cost efficiency is critical. Simply using Amazon S3 for storage isn’t enough. Businesses must fine-tune their approach to get the most out of it. Here are several best practices that help unlock the full potential of Amazon S3:
- Use smarter naming to avoid performance bottlenecks: Sequential file names like invoice-001.pdf, invoice-002.pdf can overload a single partition in Amazon S3, leading to request throttling. By adopting randomized prefixes or hash-based naming, businesses can distribute traffic more evenly and avoid slowdowns.
- Split large files using multipart uploads: Uploading large files in a single operation increases the risk of failure due to network instability. With multipart uploads, Amazon S3 breaks files into smaller parts, uploads them in parallel, and retries only the failed parts. This improves speed, reliability, and reduces operational frustration.
- Reduce latency for distributed users: For SMBs with global teams or customer bases, accessing data directly from Amazon S3 can introduce delays. By integrating Amazon CloudFront, data is cached at edge locations worldwide, reducing latency and improving user experience.
- Accelerate long-distance transfers: When remote offices or partners need to send large volumes of data, Amazon S3 Transfer Acceleration uses AWS’s edge infrastructure to speed up uploads. This significantly reduces transfer time, especially from distant geographies.
- Monitor usage with Amazon CloudWatch: Tracking S3 performance is essential. Amazon CloudWatch offers real-time visibility into metrics such as request rates, errors, and transfer speeds. These insights help businesses proactively resolve bottlenecks and fine-tune performance.
By applying these practices, SMBs transform Amazon S3 from a basic storage tool into a powerful enabler of performance, cost-efficiency, and scalability.
How Cloudtech helps businesses implement Amazon S3?
Cloudtech helps businesses turn Amazon S3 into a scalable, resilient, and AI-ready foundation for modern cloud infrastructure. Through its four core service areas, Cloudtech delivers practical, outcome-driven solutions that simplify data operations and support long-term growth.
- Data modernization: Data lake architectures are designed with Amazon S3 as the central storage layer, enabling scalable, analytics-ready platforms. Each engagement begins with an assessment of data volume, access patterns, and growth trends to define the right storage class strategy. Automated pipelines are built using AWS Glue, Athena, and Lambda to move, transform, and analyze data in real time.
- Infrastructure & resiliency services: S3 implementations are architected for resilience and availability. This includes configuring multi-AZ and cross-region replication, applying AWS Backup policies, and conducting chaos engineering exercises to validate system behavior under failure conditions. These measures help maintain business continuity and meet operational recovery objectives.
- Application modernization: Legacy applications are restructured by integrating Amazon S3 with serverless, event-driven workflows. Using AWS Lambda, automated actions are triggered by S3 events, such as object uploads or deletions, enabling real-time data processing without requiring server management. This modern approach improves operational efficiency and scales with demand.
- Generative AI: Data stored in Amazon S3 is prepared for generative AI applications through intelligent document processing using Amazon Textract. Outputs are connected to interfaces powered by Amazon Q Business, allowing teams to extract insights and interact with unstructured data through natural language, without requiring technical expertise.

Conclusion
Amazon S3 delivers scalable, high-performance storage that supports a wide range of cloud use cases. With the right architecture, naming strategies, storage classes, and integrations, teams can achieve consistent performance and long-term cost efficiency.
Amazon CloudFront, Amazon Athena, AWS Lambda, and other AWS services extend Amazon S3 beyond basic storage, enabling real-time processing, analytics, and resilient distribution.
Cloudtech helps businesses implement Amazon S3 as part of secure, scalable, and optimized cloud architectures, backed by AWS-certified expertise and a structured delivery process.
Contact us if you want to build a stronger cloud storage foundation with Amazon S3.
FAQ’s
1. Is AWS S3 a database?
No, AWS S3 is not a database. It is an object storage service designed to store and retrieve unstructured data. Unlike databases, it does not support querying, indexing, or relational data management features.
2. What is S3 best used for?
Amazon S3 is best used for storing large volumes of unstructured data such as backups, media files, static website assets, analytics datasets, and logs. It provides scalable, durable, and low-latency storage with integration across AWS services.
3. What is the difference between S3 and DB?
S3 stores objects, such as files and media, ideal for unstructured data. A database stores structured data with querying, indexing, and transaction support. S3 focuses on storage and retrieval, while databases manage relationships and real-time queries.
4. What does S3 stand for?
S3 stands for “Simple Storage Service.” Amazon’s cloud-based object storage solution offers scalable capacity, high durability, and global access for storing and retrieving any amount of data from anywhere.
5. What is S3 equivalent to?
S3 is equivalent to an object storage system, such as Google Cloud Storage or Azure Blob Storage. It functions as a cloud-based file repository, rather than a traditional file system or database, optimized for scalability and high availability.

A complete guide to Amazon S3 Glacier for long-term data storage
The global datasphere will balloon to 175 zettabytes in 2025, and nearly 80% of that data will go cold within months of creation. That’s not just a technical challenge for businesses. It’s a financial and strategic one.
For small and medium-sized businesses (SMBs), the question is: how to retain vital information like compliance records, backups, and historical logs without bleeding budget on high-cost active storage?
This is where Amazon S3 Glacier comes in. With its ultra-low costs, high durability, and flexible retrieval tiers, the purpose-built archival storage solution lets you take control of long-term data retention without compromising on compliance or accessibility.
This guide breaks down what S3 Glacier is, how it works, when to use it, and how businesses can use it to build scalable, cost-efficient data strategies that won’t buckle under tomorrow’s zettabytes.
Key takeaways:
- Purpose-built for archival storage: Amazon S3 Glacier classes are designed to reduce costs for infrequently accessed data while maintaining durability.
- Three storage class options: Instant retrieval, flexible retrieval, and deep archive support varying recovery speeds and pricing tiers.
- Lifecycle policy automation: Amazon S3 lifecycle rules automate transitions between storage classes, optimizing cost without manual oversight.
- Flexible configuration and integration: Amazon S3 Glacier integrates with existing Amazon S3 buckets, IAM policies, and analytics tools like Amazon Redshift Spectrum and AWS Glue.
- Proven benefits across industries: Use cases from healthcare, media, and research confirm Glacier’s role in long-term data retention strategies.
What is Amazon S3 Glacier storage, and why do SMBs need it?
Amazon Simple Storage Service (Amazon S3) Glacier is an archival storage class offered by AWS, designed for long-term data retention at a low cost. It’s intended for data that isn’t accessed frequently but must be stored securely and durably, such as historical records, backup files, and compliance-related documents.
Unlike Amazon S3 Standard, which is built for real-time data access, Glacier trades off speed for savings. Retrieval times vary depending on the storage class used, allowing businesses to optimize costs based on how soon or how often they need to access that data.
Why it matters for SMBs: For small and mid-sized businesses modernizing with AWS, Amazon S3 Glacier helps manage growing volumes of cold data without escalating costs. Key reasons for implementing the solution include:

- Cost-effective for inactive data: Pay significantly less per GB compared to other Amazon S3 storage classes, ideal for backup or archive data that is rarely retrieved.
- Built-in lifecycle policies: Automatically move data from Amazon S3 Standard or Amazon S3 Intelligent-Tiering to Amazon Glacier or Glacier Deep Archive based on rules with no manual intervention required.
- Seamless integration with AWS tools: Continue using familiar AWS APIs, Identity and Access Management (IAM), and Amazon S3 bucket configurations with no new learning curve.
- Durable and secure: Data is redundantly stored across multiple AWS Availability Zones, with built-in encryption options and compliance certifications.
- Useful for regulated industries like healthcare: Healthcare SMBs can use Amazon Glacier to store medical imaging files, long-term audit logs, and compliance archives without overcommitting to active storage costs.
Amazon S3 Glacier gives SMBs a scalable way to manage historical data while aligning with cost-control and compliance requirements.

How can SMBs choose the right Amazon S3 Glacier class for their data?

The Amazon S3 Glacier storage classes are purpose-built for long-term data retention, but not all archived data has the same access or cost requirements. AWS offers three Glacier classes, each designed for a different balance of retrieval time and storage pricing.
For SMBs, choosing the right Glacier class depends on how often archived data is accessed, how quickly it needs to be retrieved, and the overall storage budget.
1. Amazon S3 Glacier Instant Retrieval
Amazon S3 Glacier Instant Retrieval is designed for rarely accessed data that still needs to be available within milliseconds. It provides low-cost storage with fast retrieval, making it suitable for SMBs that occasionally need immediate access to archived content.
Specifications:
- Retrieval time: Milliseconds
- Storage cost: ~$0.004/GB/month
- Minimum storage duration: 90 days
- Availability SLA: 99.9%
- Durability: 99.999999999%
- Encryption: Supports SSE-S3 and SSE-KMS
- Retrieval model: Immediate access with no additional tiering
When it’s used: This class suits SMBs managing audit logs, patient records, or legal documents that are accessed infrequently but must be available without delay. Healthcare providers, for instance, use this class to store medical imaging (CT, MRI scans) for emergency retrieval during patient consultations.
2. Amazon S3 Glacier Flexible Retrieval
Amazon S3 Glacier Flexible Retrieval is designed for data that is infrequently accessed and can tolerate retrieval times ranging from minutes to hours. It offers multiple retrieval options to help SMBs manage both performance and cost, including a no-cost bulk retrieval option.
Specifications:
- Storage cost: ~$0.0036/GB/month
- Minimum storage duration: 90 days
- Availability SLA: 99.9%
- Durability: 99.999999999%
- Encryption: Supports SSE-S3 and SSE-KMS
- Retrieval tiers:
- Expedited: 1–5 minutes ($0.03/GB)
- Standard: 3–5 hours ($0.01/GB)
- Bulk: 5–12 hours (free per GB)
- Provisioned capacity (optional): $100 per unit/month
When it’s used: SMBs performing planned data restores, like IT service providers handling monthly backups, or financial teams accessing quarterly records, can benefit from this class. It's also suitable for healthcare organizations restoring archived claims data or historical lab results during audits.
3. Amazon S3 Glacier Deep Archive
Amazon S3 Glacier Deep Archive is AWS’s lowest-cost storage class, optimized for data that is accessed very rarely, typically once or twice per year. It’s designed for long-term archival needs where retrieval times of up to 48 hours are acceptable.
Specifications:
- Storage cost: ~$0.00099/GB/month
- Minimum storage duration: 180 days
- Availability SLA: 99.9%
- Durability: 99.999999999%
- Encryption: Supports SSE-S3 and SSE-KMS
- Retrieval model:
- Standard: ~12 hours ($0.0025/GB)
- Bulk: ~48 hours ($0.0025/GB)
When it’s used: This class is ideal for SMBs with strict compliance or regulatory needs but no urgency in data retrieval. Legal firms archiving case files, research clinics storing historical trial data, or any business maintaining long-term tax records can use Deep Archive to minimize ongoing storage costs.
By selecting the right Glacier storage class, SMBs can control storage spending without sacrificing compliance or operational needs.

How to successfully set up and manage Amazon S3 Glacier storage?

Setting up Amazon S3 Glacier storage classes requires careful planning of bucket configurations, lifecycle policies, and access management strategies. Organizations must consider data classification requirements, access patterns, and compliance obligations when designing Amazon S3 Glacier storage implementations.
The management approach differs significantly from standard Amazon S3 storage due to retrieval requirements and cost optimization considerations. Proper configuration ensures optimal performance while minimizing unexpected costs.
Step 1: Creating and configuring Amazon S3 buckets
S3 bucket configuration for Amazon S3 Glacier storage classes requires careful consideration of regional placement, access controls, and lifecycle policy implementation. Critical configuration parameters include:
- Regional selection: Choose regions based on data sovereignty requirements, disaster recovery strategies, and network latency considerations for retrieval operations
- Access control policies: Implement IAM policies that restrict retrieval operations to authorized users and prevent unauthorized cost generation
- Versioning strategy: Configure versioning policies that align with minimum storage duration requirements (90 days for Instant/Flexible, 180 days for Deep Archive)
- Encryption settings: Enable AES-256 or AWS KMS encryption for compliance with data protection requirements
Bucket policy configuration must account for the restricted access patterns associated with Amazon S3 Glacier storage classes. Standard S3 permissions apply, but organizations should implement additional controls for retrieval operations and related costs.
Step 2: Uploading and managing data in Amazon S3 Glacier storage classes

Direct uploads to Amazon S3 Glacier storage classes utilize standard S3 PUT operations with appropriate storage class specifications. Key operational considerations include:
- Object size optimization: AWS applies default behavior, preventing objects smaller than 128 KB from transitioning to avoid cost-ineffective scenarios
- Multipart upload strategy: Large objects benefit from multipart uploads, with each part subject to minimum storage duration requirements
- Metadata management: Implement comprehensive tagging strategies for efficient object identification and retrieval planning
- Aggregation strategies: Consider combining small files to optimize storage costs, where minimum duration charges may exceed data storage costs
Large-scale migrations often benefit from AWS DataSync or AWS Storage Gateway implementations that optimize transfer operations. Organizations should evaluate transfer acceleration options for geographically distributed data sources.
Step 3: Restoring objects and managing retrieval settings
Object restoration from Amazon S3 Glacier storage classes requires explicit restoration requests that specify retrieval tiers and duration parameters. Critical operational parameters include:
- Retrieval tier selection: Choose appropriate tiers based on urgency requirements and cost constraints
- Duration specification: Set restoration duration (1-365 days) to match downstream processing requirements
- Batch coordination: Plan bulk restoration operations to avoid overwhelming downstream systems
- Cost monitoring: Track retrieval costs across different tiers and adjust strategies accordingly
Restored objects remain accessible for the specified duration before returning to the archived state. Organizations should coordinate restoration timing with downstream processing requirements to avoid re-restoration costs.

How to optimize storage with Amazon S3 Glacier lifecycle policies?
Moving beyond basic Amazon S3 Glacier implementation, organizations can achieve significant cost optimization through the strategic configuration of S3 lifecycle policies. These policies automate data transitions across storage classes, eliminating the need for manual intervention while ensuring cost-effective data management throughout object lifecycles.
Lifecycle policies provide teams with precise control over how data is moved across storage classes, helping to reduce costs without sacrificing retention goals. For Amazon S3 Glacier, getting the configuration right is crucial; even minor missteps can result in higher retrieval charges or premature transitions that impact access timelines.
Translating strategy into measurable savings starts with how those lifecycle rules are configured.
1. Lifecycle policy configuration fundamentals

Amazon S3 lifecycle policies automate object transitions through rule-based configurations that specify transition timelines and target storage classes. Organizations can implement multiple rules within a single policy, each targeting specific object prefixes or tags for granular control and management.
Critical configuration parameters include:
- Transition timing: Objects in Standard-IA storage class must remain for a minimum of 30 days before transitioning to Amazon S3 Glacier
- Object size filtering: Amazon S3 applies default behavior, preventing objects smaller than 128 KB from transitioning to avoid cost-ineffective scenarios
- Storage class progression: Design logical progression paths that optimize costs while maintaining operational requirements
- Expiration rules: Configure automatic deletion policies for objects reaching end-of-life criteria
2. Strategic transition timing optimization
Effective lifecycle policies require careful analysis of data access patterns and cost structures across storage classes. Two-step transitioning approaches (Standard → Standard-IA → Amazon S3 Glacier) often provide cost advantages over direct transitions.
Optimal transition strategies typically follow these patterns:
- Day 0-30: Maintain objects in the Standard storage class for frequent access requirements
- Day 30-90: Transition to Standard-IA for reduced storage costs with immediate access capabilities
- Day 90+: Implement Amazon S3 Glacier transitions based on access frequency requirements and cost optimization goals
- Day 365+: Consider Deep Archive transition for long-term archival scenarios
3. Policy monitoring and cost optimization
Billing changes occur immediately when lifecycle configuration rules are satisfied, even before physical transitions complete. Organizations must implement monitoring strategies that track the effectiveness of policies and their associated costs.
Key monitoring metrics include:
- Transition success rates: Monitor successful transitions versus failed attempts
- Cost impact analysis: Track storage cost reductions achieved through lifecycle policies
- Access pattern validation: Verify that transition timing aligns with actual data access requirements
- Policy rule effectiveness: Evaluate individual rule performance and adjust configurations accordingly
What type of businesses benefit the most from Amazon S3 Glacier?
Amazon S3 Glacier storage classes are widely used to support archival workloads where cost efficiency, durability, and compliance are key priorities. Each class caters to distinct access patterns and technical requirements.
The following use cases, drawn from AWS documentation and customer case studies, illustrate practical applications of these classes across different data management scenarios.
1. Media asset archival (Amazon S3 Glacier Instant Retrieval)
Amazon S3 Glacier Instant Retrieval is recommended for archiving image hosting libraries, video content, news footage, and medical imaging datasets that are rarely accessed but must remain available within milliseconds. The class provides the same performance and throughput as Amazon S3 Standard while reducing storage costs.
Snap Inc. serves as a reference example. The company migrated over two exabytes of user photos and videos to Instant Retrieval within a three-month period. Despite the massive scale, the transition had no user-visible impact. In several regions, latency improved by 20-30 percent. This change resulted in annual savings estimated in the tens of millions of dollars, without compromising availability or throughput.
2. Scientific data preservation (Amazon S3 Glacier Deep Archive)
Amazon S3 Glacier Deep Archive is designed for data that must be retained for extended periods but is accessed infrequently, such as research datasets, regulatory archives, and records related to compliance. With storage pricing at $0.00099 per GB per month and durability of eleven nines across multiple Availability Zones, it is the most cost-efficient option among S3 classes. Retrieval options include standard (up to 12 hours) and bulk (up to 48 hours), both priced at approximately $0.0025 per GB.
Pinterest is one example of Deep Archive in practice. The company used Amazon S3 Lifecycle rules and internal analytics pipelines to identify infrequently accessed datasets and transition them to Deep Archive. This transition enabled Pinterest to reduce annual storage costs by several million dollars while meeting long-term retention requirements for internal data governance.
How Cloudtech helps SMBs solve data storage challenges?
SMBs don’t need to figure out Glacier class selection on their own. AWS partners like Cloudtech can help them assess data access patterns, retention requirements, and compliance needs to determine the most cost-effective Glacier class for each workload. From setting up automated Amazon S3 lifecycle rules to integrating archival storage into ongoing cloud modernization efforts, Cloudtech ensures that SMBs get the most value from their AWS investment.
A recent case study around a nonprofit healthcare insurer illustrates this approach. They faced growing limitations with its legacy on-premises data warehouse, built on Oracle Exadata. The setup restricted storage capacity, leading to selective data retention and delays in analytics.
Cloudtech designed and implemented an AWS-native architecture that eliminated these constraints. The new solution centered around a centralized data lake built on Amazon S3, allowing full retention of both raw and processed data in a unified, secure environment.
To support efficient data access and compliance, the architecture included:
- AWS Glue for data cataloging and metadata management
- Amazon Redshift Spectrum for direct querying from Amazon S3 without the need for full data loads
- Automated Redshift backups stored directly in Amazon S3 with custom retention settings
This minimized data movement, enabled near real-time insights, and supported healthcare compliance standards around data availability and continuity.
Outcome: By transitioning to managed AWS services, the client removed storage constraints, improved analytics readiness, and reduced infrastructure overhead. The move also unlocked long-term cost savings by aligning storage with actual access needs through Amazon S3 lifecycle rules and tiered Glacier storage classes.
Similarly, Cloudtech is equipped to support SMBs with varying storage requirements. It can help businesses with:
- Storage assessment: Identifies frequently and infrequently accessed datasets to map optimal Glacier storage classes
- Lifecycle policy design: Automates data transitions from active to archival storage based on access trends
- Retrieval planning: Aligns retrieval time expectations with the appropriate Glacier tier to minimize costs without disrupting operations
- Compliance-focused configurations: Ensures backup retention, encryption, and access controls meet industry-specific standards
- Unified analytics architecture: Combines Amazon S3 with services like AWS Glue and Amazon Redshift Spectrum to improve visibility without increasing storage costs
Whether it’s for healthcare records, financial audits, or customer history logs, Cloudtech helps SMBs build scalable, secure, and cost-aware storage solutions using only AWS services.

Conclusion
Amazon S3 Glacier storage classes, Instant Retrieval, Flexible Retrieval, and Deep Archive, deliver specialized solutions for cost-effective, long-term data retention. Their retrieval frameworks and pricing models support critical compliance, backup, and archival needs across sectors.
Selecting the right class requires alignment with access frequency, retention timelines, and budget constraints. With complex retrieval tiers and storage duration requirements, expert configuration makes a measurable difference. Cloudtech helps organizations architect Amazon S3 Glacier-backed storage strategies that cut costs while maintaining scalability, data security, and regulatory compliance.
Book a call to plan a storage solution that fits your operational and compliance needs, without overspending.
FAQ’s
1. What is the primary benefit of using Amazon S3 Glacier?
Amazon S3 Glacier provides ultra-low-cost storage for infrequently accessed data, offering long-term retention with compliance-grade durability and flexible retrieval options ranging from milliseconds to days.
2. Is the Amazon S3 Glacier free?
No. While Amazon Glacier has the lowest storage costs in AWS, charges apply for storage, early deletion, and data retrieval based on tier and access frequency.
3. How to change Amazon S3 to Amazon Glacier?
Use Amazon S3 lifecycle policies to automatically transition objects from standard classes to Glacier. You can also set the storage class during object upload using the Amazon S3 API or console.
4. Is Amazon S3 no longer global?
Amazon S3 remains a regional service. Data is stored in selected AWS Regions, but can be accessed globally depending on permissions and cross-region replication settings.
5. What is a vault in Amazon S3 Glacier?
Vaults were used in the original Amazon Glacier service. With Amazon S3 Glacier, storage is managed through Amazon S3 buckets and storage classes, rather than separate vault structures.

Getting started with AWS Athena: a comprehensive guide
Small and medium-sized businesses (SMBs) seek to derive value from their data without heavy infrastructure investment, and Amazon Athena offers a simple yet powerful solution. As a serverless query service, Athena allows teams to run SQL queries directly on data stored in Amazon S3, eliminating the need for provisioning servers, setting up databases, or managing ETL pipelines.
Many SMBs use Athena to generate fast insights from CSVs, logs, or JSON files stored in S3. For example, a healthcare provider can use Athena to analyze patient encounter records stored in S3, helping operations teams track appointment volumes, identify care gaps, or monitor billing anomalies in real time.
This guide will go deeper into how Athena works, how it integrates with AWS Glue for automated schema discovery, and how SMBs can get started quickly while keeping costs predictable and usage efficient.
Key takeaways:
- Run interactive SQL queries directly on Amazon S3 without managing any servers or infrastructure.
- Only pay for the data scanned, making it cost-effective for SMBs with varying workloads.
- Works seamlessly with AWS Glue, IAM, QuickSight, and supports multiple data formats like Parquet, JSON, and CSV.
- Ideal for log analysis, ad-hoc queries, BI dashboards, clickstream analysis, and querying archived data.
- Read-only access, no DML support, performance depends on partitioning and query optimization.
What is AWS Athena and why does it matter for SMBs?

Amazon Athena is a serverless, distributed SQL query engine built on Trino (formerly Presto) that lets businesses query data directly in Amazon S3 using standard SQL, without provisioning infrastructure or building ETL pipelines.
It runs queries in parallel across partitions of business data, which drastically reduces response times even for multi-terabyte datasets. Its schema-on-read model means SMB teams can analyze raw files like CSV, JSON, or Parquet without needing to ingest or transform them first.
Key technical benefits for SMBs include:
- Efficient querying with columnar formats: When SMBs store data in Parquet or ORC, Athena scans only the relevant columns, significantly reducing the amount of data processed and cutting query costs.
- Tight AWS integration: Athena connects to the AWS Glue Data Catalog for automatic schema discovery, versioning, and metadata management, allowing SMBs to treat their Amazon S3 data lake like a structured database.
- Federated query support: SMB teams can run SQL queries across other AWS services (e.g., DynamoDB, Redshift) and external sources (e.g., MySQL, BigQuery) using connectors through AWS Lambda, enabling cross-source analytics without centralizing all their data.
- Security and compliance: Access is controlled via IAM, and all data in transit and at rest can be encrypted. Athena logs queries and results to CloudTrail and CloudWatch, helping regulated industries meet audit requirements.
Example: A diagnostics lab stores lab results in Parquet files on Amazon S3. With Amazon Athena + AWS Glue, they create a unified SQL-accessible view without loading data into a database. Analysts query test volume by region, check turnaround time patterns, and even flag anomalies, all with no infrastructure or long reporting delays.
The bottom line? Amazon Athena gives SMBs the power of big data analytics—on-demand, with no overhead—making it ideal for lean teams that need insights fast without building a data warehouse.

How to get started with AWS Athena? step-by-step
To get started, businesses need to organize their data in Amazon S3, define schemas using AWS Glue Data Catalog, and run queries using standard SQL. With native integration into AWS services, fine-grained IAM access controls, and a pay-per-query model, Athena makes it easy to unlock insights from raw data with minimal setup. It's ideal for teams needing quick, cost-effective analytics on logs, reports, or structured datasets.
Setting up AWS Athena is relatively straightforward, even for businesses with limited technical expertise:
1. Set up an AWS account

To begin using Amazon Athena, an active AWS account is required. The user must ensure that Identity and Access Management (IAM) permissions are correctly configured. Specifically, the IAM role or user should have the necessary policies to access Athena, Amazon S3 (for data storage and query results), and AWS Glue (for managing metadata).
It's recommended to attach managed policies like AmazonAthenaFullAccess, AmazonS3ReadOnlyAccess, and AWSGlueConsoleFullAccess or create custom policies with least-privilege principles tailored to the organization’s security needs. These permissions allow users to create databases, define tables, and execute queries securely within Athena.
2. Create an S3 bucket for data storage

Before running queries with Athena, data must reside in Amazon S3, as Athena is designed to analyze objects stored there directly. This setup step includes bucket creation, data upload, and optimization for query performance.
Navigate to the Amazon S3 console and click “Create bucket.”
- Assign a globally unique name.
- Choose a region close to the workloads or users for latency optimization.
- Enable settings like versioning, encryption (e.g., SSE-S3 or SSE-KMS), and block public access if required.
Upload datasets in supported formats: Athena supports multiple formats, including CSV, JSON, Parquet, ORC, and Avro.
- For better performance and lower cost, use columnar formats like Parquet or ORC.
- Store large datasets in compressed form to reduce data scanned per query.
Organize data into partitions: Structuring data into logical partitioned folders (e.g., s3://company-data/patient-records/year=2025/month=07/) enables Athena to prune unnecessary partitions during query execution.
This improves performance and significantly reduces query costs, as Athena only scans relevant subsets of data.
Set appropriate permissions: Ensure IAM roles or users have the necessary S3 permissions to list, read, and write objects in the bucket. Fine-grained access control improves security and limits access to authorized workloads only.
3. Set up AWS Glue Data catalog (optional)

AWS Glue helps SMBs manage metadata and automate schema discovery for datasets stored in Amazon S3, making Athena queries more efficient and scalable.
- The team creates a Glue database to store metadata about the S3 datasets.
- A crawler is configured to scan the S3 bucket and automatically register tables with defined schemas.
- Once cataloged, these tables appear in Athena, enabling immediate, structured SQL queries without manual schema setup.
4. Access AWS Athena console

Once the data is in Amazon S3 and cataloged (if applicable), the team navigates to the Amazon Athena console via the AWS Management Console.
- They configure a query result location, specifying an S3 bucket where Athena will store the output of all executed queries.
- This is a mandatory setup step, as Athena requires an S3 destination for query results before any SQL can be run.
5. Run the first query

With the environment configured, the team can begin querying data:
- In the Athena console, they select the relevant database and table, automatically available if defined in AWS Glue.
- They write a query using standard SQL to analyze data directly from Amazon S3.
- On executing the query via “Run Query,” Athena scans the underlying data and returns the results in the console and the designated S3 output location.
6. Review and optimize queries

As the team begins using Athena, it’s important to ensure queries remain efficient and cost-effective:
- Implement partitioning on commonly filtered columns (e.g., date or region) to reduce the amount of data scanned.
- Limit query scope by selecting only necessary columns and applying precise WHERE clauses to minimize data retrieval.
- Use the Athena console to monitor query execution time, data scanned, and associated costs, enabling optimization and proactive cost control.
7. Explore advanced features (optional)
Once the foundational setup is complete, SMBs can begin using Amazon Athena’s more advanced capabilities:
- Optimize with efficient data formats: Use columnar formats like Parquet or ORC to reduce scan size and improve query performance for large datasets.
- Visualize with Amazon QuickSight: Connect Athena to Amazon QuickSight for interactive dashboards and business intelligence without moving data.
- Run federated queries: Extend Athena’s reach by querying external data sources, such as MySQL, PostgreSQL, or on-prem databases—via federated connectors and AWS Lambda.
These features allow teams to scale their analytics capabilities while keeping operational overhead low.

Practical use cases for Amazon Athena in business operations

Amazon Athena is more than a business tool. It is a practical engine for answering real business questions directly from raw data in S3, without the delays of setting up infrastructure or ETL pipelines.
For SMBs, it offers a fast path from storage to insight, whether you’re analyzing patient records in healthcare, transaction logs in retail, or system logs in SaaS platforms. Because it speaks standard SQL and integrates natively with AWS Glue and QuickSight, teams can start querying within minutes, with no heavyweight setup, and no data wrangling bottlenecks.
1. Log analysis and monitoring
Amazon Athena is ideal for analyzing server logs and application logs stored in Amazon S3. It allows businesses to perform real-time analysis of logs without needing to set up complex infrastructure.
Example: A retail SMB collects logs from its web servers, tracking user activity and transaction details. Using Athena, the business can query logs to identify trends such as peak shopping hours or common search queries. This data helps the company optimize its website for better user engagement and targeted promotions.
2. Data warehousing and business intelligence
Amazon Athena can be used as a lightweight data warehousing solution, particularly for SMBs that do not require the heavy infrastructure of a full-scale data warehouse. It integrates easily with Amazon QuickSight to deliver business intelligence (BI) dashboards and reports.
Example: A small e-commerce business uses Athena to run SQL queries on sales data stored in Amazon S3. The results are then visualized in Amazon QuickSight to track key performance indicators (KPIs), such as daily sales, revenue per product, and customer acquisition rates, allowing the business to make data-driven decisions.
3. Ad-hoc data queries
For businesses that need to quickly analyze large datasets without the overhead of setting up and maintaining a dedicated analytics system, Athena provides an efficient and cost-effective solution.
Example: A small marketing firm has large datasets containing customer demographics and campaign performance metrics. With Athena, the firm can run ad-hoc queries to analyze customer behavior and assess the effectiveness of different marketing campaigns in real-time, without needing a permanent infrastructure.
4. Clickstream analysis
Athena is a popular tool for analyzing clickstream data, which helps businesses understand user behavior on websites or apps. By querying clickstream data in real-time, companies can optimize user experiences and improve conversion rates.
Example: A media company collects clickstream data that tracks how users interact with its online content. Using Athena, the company can quickly query this data to identify which articles or videos are most popular, what content leads to longer engagement, and where users drop off. This allows the company to tailor content strategies to improve user retention.
5. Data archiving and backup analysis
Businesses often archive large amounts of historical data that may not be frequently accessed but still need to be searchable. Athena makes it easy to query these archives to retrieve specific data when needed.
Example: A healthcare provider stores patient records and historical treatment data in S3. Though this data is rarely accessed, it still needs to be searchable in case of audits or legal requests. Athena allows the provider to run quick queries on archived data, retrieving necessary records without the need for time-consuming data retrieval processes.
Amazon Athena’s versatility makes it an excellent tool for a wide range of use cases, from log analysis to financial reporting. Its serverless nature and cost-effective pricing model ensure that even SMBs with limited technical resources can harness the power of data analytics without the need for complex infrastructure.

How does Cloudtech help SMBs benefit from Amazon Athena?
Deploying Amazon Athena effectively requires the right data architecture, schema management, and cost governance to ensure long-term value. That’s where Cloudtech comes in. As an AWS Advanced Tier Partner focused exclusively on SMBs, Cloudtech helps them harness Athena with a strategic, scalable approach tailored to real business needs.
Here’s how Cloudtech supports the Amazon Athena project:
- Smart data lake setup: Cloudtech builds secure, well-partitioned data lakes on Amazon S3 and integrates AWS Glue for schema discovery, enabling faster, cost-efficient queries with minimal manual setup.
- Query performance optimization: By implementing best practices like columnar formats (Parquet/ORC), partitioning, and bucket strategies, Cloudtech ensures that every Athena query is fast and budget-aware.
- Secure, unified data access: Cloudtech configures federated queries across Amazon S3, on-prem, and third-party sources while enforcing fine-grained IAM policies, so teams can query broadly without compromising security.
- Insights without the overhead: Cloudtech connects Athena to Amazon QuickSight or other BI tools, enabling business teams to explore data visually, without needing SQL or data engineering support.
Whether it is a healthcare provider analyzing claims data or a fintech firm building on-demand dashboards, Cloudtech ensures that Amazon Athena is implemented not just as a tool, but as a foundation for faster, smarter, and more secure decision-making.
Conclusion
Amazon Athena offers SMBs a powerful, serverless solution to analyze data directly from Amazon S3 using standard SQL, eliminating infrastructure complexities and reducing costs. Its fast performance and seamless integration with AWS services enable businesses to gain timely insights and make data-driven decisions efficiently. By following simple setup steps, SMBs can leverage Athena for diverse use cases, from log analysis to business intelligence, enhancing operational agility and scalability.
Cloudtech’s expertise in AWS infrastructure optimization and cloud modernization complements this approach by helping businesses streamline operations and maximize cloud investments.
Talk to our cloud experts or reach us on (332) 222 7090).
FAQs
1. How can AWS Athena help small and midsize businesses reduce their data analytics costs?
AWS Athena’s serverless, pay-per-query pricing model means SMBs only pay for the data they actually scan, eliminating upfront infrastructure costs and allowing flexible, cost-efficient analytics that scale with business needs.
2. What are the key steps for SMBs to start using Athena without a large IT team?
SMBs can quickly begin by setting up an AWS account, creating an S3 bucket for data storage, configuring IAM permissions, and using the Athena console or AWS Glue Data Catalog to define schemas and run SQL queries, all without managing servers.
3. What types of data formats does AWS Athena support for querying?
Athena supports a wide range of data formats including CSV, JSON, Apache Parquet, ORC, and Avro, enabling flexible querying of structured, semi-structured, and unstructured data directly in Amazon S3.
4. Can Athena be integrated with other AWS services for enhanced analytics?
Yes, Athena integrates seamlessly with AWS Glue for metadata management, Amazon QuickSight for data visualization, and supports federated queries to access data across multiple sources, enhancing overall analytics capabilities.
5. How does Cloudtech assist SMBs in maximizing their AWS Athena deployment?
Cloudtech offers cloud modernization services including AWS infrastructure optimization, data management, and application modernization, helping businesses streamline Athena usage, improve scalability, enhance security, and control costs effectively.

An AWS cybersecurity guide for SMBs in 2025
Cyberattacks are getting more frequent and more expensive. IBM’s most recent cloud security study reports that the average cost of a data breach has reached USD 4.35 million. In response, over half of global organizations are planning to boost investments in threat detection, incident response, and cloud security tools throughout 2025.
For small and mid-sized businesses (SMBs) in sectors like healthcare and fintech, the stakes are even higher. All it takes is one misconfigured access policy or exposed resource to trigger a costly security incident or regulatory fallout.
The good news is that AWS provides a flexible foundation for implementing strong, scalable defenses if the right controls are in place. That’s why more growth-focused SMBs are working with AWS partners like Cloudtech to build secure, compliant environments from the ground up.
This article walks through the most important AWS cloud security practices for 2025, and how to implement them in a way that aligns with the risk profile, industry standards, and long-term goals.
Key takeaways:
- Security is not a one-time setup; it’s a continuous discipline: AWS provides the tools, but SMBs must define clear strategies and enforce controls as environments evolve.
- Misconfigurations are the biggest threat, and the easiest to prevent: With IAM policies, automated monitoring, and least privilege access, most breaches can be avoided before they happen.
- Smart automation is force multiplication for small teams: Tools like AWS Config, Amazon GuardDuty, and AWS Systems Manager help SMBs scale security efforts without scaling headcount.
- Cloud-native security doesn’t mean complexity; it means control: When implemented correctly, AWS makes it easier for SMBs to enforce governance, meet compliance, and respond quickly to threats.
Why do SMBs need a security-first AWS strategy?
AWS operates on a shared responsibility model, meaning Amazon secures the infrastructure, while customers are accountable for securing their data, configurations, and access policies.
Without a clear, well-documented strategy, SMBs often face preventable risks like open Amazon S3 buckets, over-permissive IAM roles, or outdated security groups. These gaps aren’t just technical oversights. They’re business liabilities that can lead to data breaches, compliance violations, and lost customer trust.
For industries like healthcare and fintech, the pressure is even greater. Regulations such as HIPAA and PCI-DSS require strict controls over data access, encryption, and audit trails. Falling short, even unintentionally, can result in heavy fines and reputational damage.
Establishing cloud security best practices from the start helps SMBs:
- Stay compliant with evolving industry regulations
- Reduce the risk of misconfiguration and unauthorized access
- Gain visibility into their cloud environment through monitoring and alerting
- Build a strong foundation that scales with business growth
For SMBs having limited IT teams or expertise, AWS partners like Cloudtech can help them implement the necessary AWS cybersecurity strategies in a way that fits their team size, risk profile, and industry requirements.
How can SMBs implement a security-first AWS strategy?
Unlike large enterprises, most SMBs don’t have the luxury of dedicated security teams or redundant systems. They move fast, manage lean teams, and prioritize innovation, especially in sectors like healthcare and fintech where demand is high and competition is fierce. Cloud platforms like AWS help level the playing field, but only if security keeps pace with growth.
In the early stages, it’s natural to focus on performance and delivery. But as environments expand with new workloads, more users, and tighter compliance expectations, security gaps can quietly emerge. Maybe a former contractor still has admin access. Maybe a key data store isn’t encrypted. They’re common side effects of scaling without a structured security plan. And when audits or incidents do arise, they tend to hit smaller businesses harder.
A security-first strategy helps SMBs get ahead of these risks. It brings clarity to what needs protecting, who needs access, and how to automate guardrails that support rather than slow down the business.
The following step-by-step strategy outlines how SMBs can achieve this using AWS-native tools, without overextending their teams or budgets.
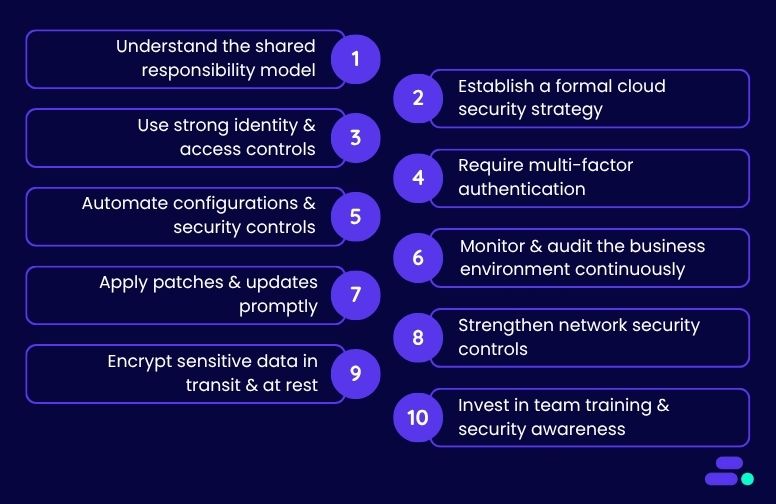
1. Understand the shared responsibility model
Security in the cloud is a shared model. AWS secures the infrastructure of the cloud, while businesses are responsible for what they put in it. That includes user access, data classification, encryption settings, compliance configurations, and software-level protections. For SMBs in fintech and healthcare, this model directly impacts how they approach risk management, incident response, and audit readiness.
Real-world scenario: A healthcare startup launches a patient portal on Amazon EC2, assuming AWS manages encryption and access controls by default. However, without explicitly configuring IAM policies, enabling encryption at rest for EBS volumes, or setting up Amazon CloudTrail for audit logs, the environment remains exposed. This violates HIPAA and risks reputational damage in the event of a breach.
To operationalize the shared responsibility model:
- Map responsibilities by service: Use the AWS Shared Responsibility Model and align it with business architecture. For example, AWS manages Amazon RDS’s physical infrastructure. The SMB must enable encryption, rotate keys, and configure IAM policies for database access.
- Assign internal ownership: Create a responsibility matrix that maps each AWS service (e.g., Amazon S3, Amazon EC2, Amazon RDS, AWS Lambda) to a specific team or role, such as DevOps, compliance, or security engineering. This prevents accountability gaps.
- Standardize configuration baselines: Use AWS Config rules and AWS CloudFormation templates to enforce consistent security controls across environments (e.g., block public Amazon S3 buckets, enforce MFA for IAM users).
- Review regularly: As the stack evolves, review ownership and configuration at least quarterly to ensure no drift has occurred, especially after team changes, rapid scaling, or vendor integrations.
Understanding this model ensures that no one assumes AWS “has it covered” when, in reality, critical responsibilities like encryption, access control, and compliance reporting rest squarely on the business side of the fence.
2. Establish a formal cloud security strategy
Once the lines of responsibility are clear, the next priority is developing a formal cloud security strategy. Many SMBs, especially in regulated sectors like healthcare and fintech, spin up AWS environments quickly to meet demand, but without a guiding framework, risk and compliance gaps grow unnoticed.
A security strategy ensures consistency and accountability across teams, especially as infrastructure scales or regulatory pressure increases.
2. Establish a formal cloud security strategy
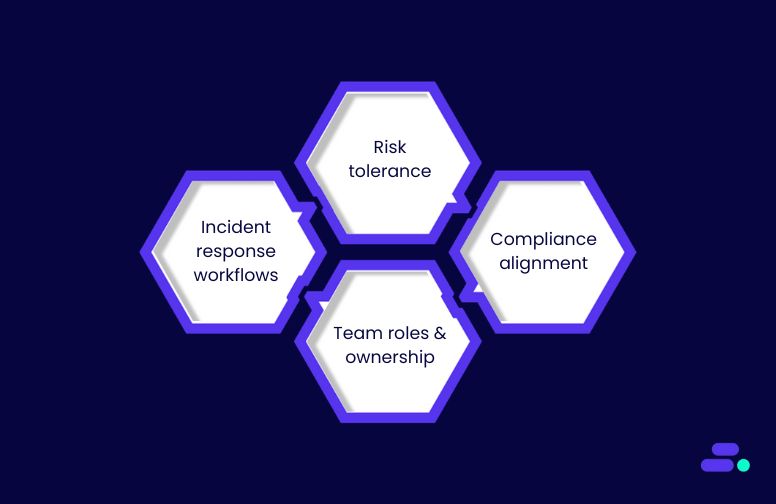
- Risk tolerance: Clarify how much risk the business can accept when choosing between speed, cost, and control. This informs architecture and vendor decisions.
- Compliance alignment: Map applicable standards like HIPAA, PCI-DSS, or SOC 2 to AWS configurations. For example, enable Amazon S3 encryption, enforce logging, and use private subnets for sensitive workloads.
- Team roles and ownership: Assign responsibility for identity, monitoring, key management, and remediation to avoid gaps during day-to-day ops or audits.
- Incident response workflows: Document how the team will detect and respond to threats, using AWS-native tools like Amazon GuardDuty, AWS CloudTrail, and AWS Systems Manager.
This document doesn’t need to be perfect from day one, but it does need to exist and evolve over time. Treat it as the team’s north star for scaling securely and making decisions that stand up to audits, not just deadlines.
3. Use strong identity and access controls
With a strategy in place, the next layer is precise access control. Identity and access missteps, especially overly broad permissions, are among the top causes of cloud breaches in SMB environments.
Using AWS Identity and Access Management (IAM), teams can enforce least-privilege access by:
- Defining role-based policies that grant only what’s needed per function. For example, a billing user shouldn’t have access to EC2 instances, and dev teams shouldn’t see production secrets.
- Disabling root account use for anything beyond initial setup. Instead, use federated identities or IAM roles with MFA.
- Eliminating long-lived credentials by rotating access keys. Use AWS IAM Identity Center (formerly AWS SSO) for session-based logins tied to the identity provider (e.g., Okta, Azure AD).
A healthcare SMB using shared admin credentials across AWS services may be compliant on paper but vulnerable in practice. Granular IAM policies, tied to monitored roles, help contain blast radius and support incident forensics if something goes wrong.
4. Require multi-factor authentication (MFA)
Even with tight IAM controls, stolen or reused credentials remain a top threat, especially in environments where small teams juggle multiple roles. That’s where multi-factor authentication (MFA) becomes critical.
MFA ensures that access requires something more than just a password. It should be non-negotiable for:
- Root users
- Admin and DevOps roles
- Any user interacting with production data or infrastructure
AWS makes implementation straightforward through virtual MFA apps (like Google Authenticator or Authy), hardware tokens, or integration with SSO platforms that support MFA enforcement.
For an SMB handling patient records or financial data, a single compromised credential without MFA could expose the entire AWS account. Enforcing MFA minimizes this risk and adds resilience against phishing, social engineering, or credential stuffing attempts.

5. Automate configurations and security controls
Once identity and access layers are secured, the next priority is eliminating manual configuration drift.
For SMBs, especially those with lean IT teams, automation isn’t just a time-saver. It’s a security multiplier. By using AWS-native tools, teams can standardize deployments, enforce guardrails, and respond to threats without delay.
Key tools and approaches include:
- AWS Config for real-time compliance checks against custom or managed security baselines, flagging issues like open ports or unencrypted volumes as they happen.
- AWS CloudFormation or Terraform to provision infrastructure in a secure, repeatable way, so dev teams don’t accidentally deploy with misconfigured security groups or public access.
- AWS Systems Manager and Lambda to automate patching, log reviews, and even auto-remediation for policy violations or failed audits.
In healthcare, for example, automation can help enforce HIPAA-aligned encryption and retention policies across resources. For fintech, it supports audit-readiness and reduces reliance on ad hoc scripts or manual checklists.
6. Monitor and audit the business environment continuously
Even well-automated environments need constant visibility. Threats evolve, workloads shift, and misconfigurations can creep in. For SMBs in sectors like healthcare and fintech, where downtime or data exposure can have legal and reputational consequences, real-time monitoring and auditing aren’t optional.
Fortunately, AWS offers integrated tools that make continuous oversight both achievable and scalable:
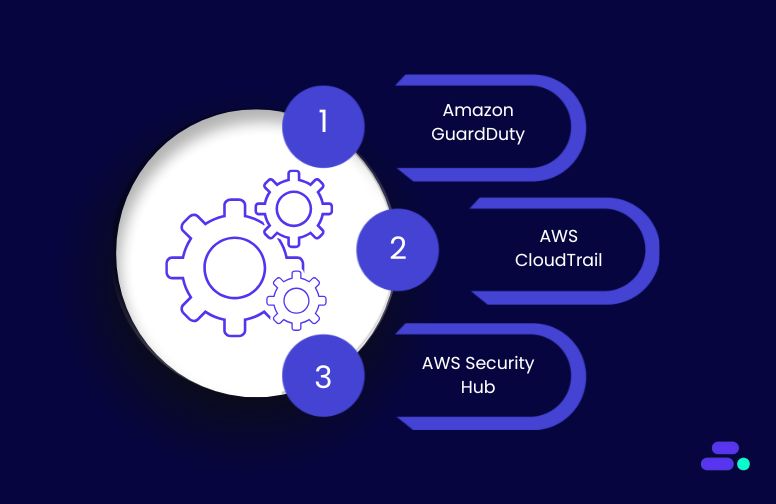
- Amazon GuardDuty delivers intelligent threat detection using machine learning to identify unusual patterns like port scanning, credential compromise, or data exfiltration attempts.
- AWS CloudTrail provides a detailed audit log of every API call, giving the team traceability for changes, critical for root cause analysis or compliance investigations.
- AWS Security Hub aggregates findings across AWS services, offering a unified dashboard to check alignment with frameworks like CIS Benchmarks, HIPAA, or PCI-DSS.
To stay effective, alerts must go beyond dashboards. Set up automated notifications for critical anomalies and establish ownership for reviewing, escalating, and responding to alerts. Small teams can also use third-party SIEM integrations or managed detection and response (MDR) services to extend coverage.
7. Apply patches and updates promptly
Security monitoring is only useful if it’s followed by action, and patching is one of the most critical. Unpatched systems remain one of the top causes of cloud breaches, especially when vulnerabilities are publicly known and easily exploitable.
For SMBs, falling behind on updates is often a bandwidth issue. But AWS provides tools to automate and streamline the process without disrupting operations:
- AWS Systems Manager Patch Manager allows teams to automate patching schedules for Amazon EC2 instances and on-premises hybrid environments.
- Compliance dashboards on AWS Systems Manager help track which systems are up to date and which require immediate attention.
- Maintenance windows on AWS Systems Manager can help apply patches during off-peak hours, minimizing service interruptions.
Make patching a priority for public-facing services, applications handling sensitive data, and any system tied to regulatory compliance. In healthcare and fintech, a missed patch could trigger an audit failure or data breach liability.
8. Strengthen network security controls
Once the workloads are patched and up to date, the next layer of defense is the network itself. Poorly configured network settings, like open ports or flat VPC architectures, can expose sensitive data to the internet or allow lateral movement if compromised.
To reduce the attack surface and enforce segmentation:
- Use Security Groups and Network ACLs to control inbound/outbound traffic at both the instance and subnet levels
- Replace public IPs with VPC endpoints to keep service traffic inside the AWS environment
- Deploy AWS WAF (Web Application Firewall) to block injection attacks, cross-site scripting (XSS), and other Layer 7 exploits
- Avoid open ports like 0.0.0.0/0 for SSH or RDP and use bastion hosts or Session Manager instead
For SMBs in healthcare or fintech, these network controls aren’t just good practice. They’re often required for regulatory compliance. Proactively auditing firewall rules, restricting access by IP or geography, and isolating workloads by function can significantly reduce the blast radius of any incident.
9. Encrypt sensitive data in transit and at rest
Encryption is a baseline requirement, not a bonus, especially for SMBs in healthcare or fintech where data privacy laws like HIPAA, PCI-DSS, or GLBA are non-negotiable. AWS makes encryption accessible, but it’s up to the team to configure and manage it correctly.
For data at rest, enable:
- SSE-S3 for server-side encryption in Amazon S3
- EBS encryption for volumes attached to EC2 instances
- RDS encryption for managed databases, ideally using Customer-Managed Keys (CMKs) via AWS Key Management Service (KMS)
For data in transit, always:
- Use TLS 1.2 or higher
- Manage certificates through AWS Certificate Manager (ACM) for secure HTTPS connections
- Avoid sending sensitive data over unencrypted channels, even between internal systems
Don’t stop at enabling encryption, also:
- Define key rotation schedules
- Enforce least-privilege policies for key access
- Monitor access logs for unusual activity around encryption resources
For SMBs, this ensures that even if other defenses fail, the most sensitive data remains unreadable and auditable, helping businesses stay compliant and protected at scale.

10. Invest in team training and security awareness
Technology alone doesn’t secure the cloud; people do. For SMBs, especially in high-stakes industries like healthcare and fintech, the weakest link is often user behavior, not tooling. A well-configured AWS environment can still be compromised if employees fall for phishing attempts or misconfigure permissions.
To build a security-first culture:
- Train every team member, from IT admins to frontline staff, on AWS security basics, password hygiene, MFA usage, and phishing recognition
- Utilize AWS Skill Builder learning paths or bring in certified AWS training partners like Cloudtech for hands-on workshops
- Run regular tabletop exercises and simulated incidents to test the team’s response readiness
Security awareness should be part of onboarding, reinforced during team meetings, and revisited as the environment evolves. Organizations that embed security into their day-to-day culture are not only better prepared to defend against attacks, but they also recover faster and maintain customer trust when incidents occur.
By following these practices, SMBs can build a compliant and scalable AWS environment.
How does Cloudtech help SMBs secure their cloud?
For small and mid-sized businesses, especially those in regulated sectors like healthcare and fintech, moving to AWS is just the first step. Security, uptime, and compliance must be intentionally designed. Cloudtech, an AWS Advanced Tier Services Partner, helps SMBs modernize their AWS environments with resilient, secure architectures that support long-term scalability without adding operational burden.
1. Building a secure and resilient cloud foundation
Cloudtech designs AWS-native environments that are fault-tolerant, cost-optimized, and compliance-ready. From AWS Control Tower governance and multi-AZ architectures to serverless infrastructure and automated monitoring with AWS CloudWatch, every layer is tailored to reduce risk and scale with the business.
2. Reducing downtime and strengthening disaster readiness
Using best practices in backup, disaster recovery, and chaos engineering, Cloudtech enables SMBs to maintain uptime even during outages or attacks. Solutions like active-active replication and automated failover ensure that systems stay online, while workshops and stress testing uncover vulnerabilities before they cause disruption.
3. Migrating intelligently and modernizing securely
Cloudtech handles end-to-end workload migration with minimal disruption, while ensuring each workload is re-architected for security, cost efficiency, and future growth. Post-migration, the environments are optimized for AI-readiness and regulatory compliance, positioning SMBs to use advanced AWS capabilities without added complexity.
Each engagement follows a structured five-phase approach—Engage, Discover, Align, Deliver, and Enable—ensuring every step aligns with the SMB’s goals, compliance needs, and internal capabilities.
Modernize with confidence, backed by AWS expertise
Migrating to AWS gives SMBs the tools to improve resilience, optimize costs, and scale faster. But true cloud success isn’t just about moving workloads. It’s about transforming how teams operate, innovate, and engage customers.
Cloudtech helps SMBs move beyond lift-and-shift with an AWS-native strategy designed around business outcomes. From automating operations and unlocking real-time insights to enabling AI-driven workflows, Cloudtech aligns cloud capabilities with goals, securely and efficiently.
For SMBs ready to break free from legacy limitations, Cloudtech delivers a proven path to modernization with deep AWS expertise, practical strategy, and long-term support.
Connect with Cloudtech to start the conversation.
FAQs
1. How can SMBs determine if their AWS environment is adequately secured?
Security maturity evolves with the business. Cloudtech helps SMBs assess their environment using AWS Security Hub benchmarks and custom KPIs such as identity sprawl, encryption coverage, and patch compliance. This allows organizations to continuously measure posture and prioritize remediation based on actual risk exposure.
2. What are the next steps after implementing MFA and IAM best practices?
Once foundational access controls are in place, the focus should shift to proactive threat detection and automated response. Cloudtech enables SMBs to deploy services like GuardDuty and Systems Manager Automation to detect anomalies and respond in real time, helping teams move from reactive to proactive security operations.
3. How can SMBs prevent security configurations from drifting over time?
Configuration drift often occurs as environments grow and change. Cloudtech mitigates this by implementing AWS Config and conformance packs that enforce predefined policies. Combined with Infrastructure as Code tools like CloudFormation, this ensures environments remain consistent, auditable, and secure at scale.
4. What should an SMB do immediately following a security incident in AWS?
The first priority is containment, isolating affected resources using IAM and VPC controls. Cloudtech helps SMBs build incident response playbooks that include forensic analysis with CloudTrail, root cause tracing, and automated remediation via Lambda. This shortens recovery time and helps teams close security gaps quickly.
5. Is advanced cloud security necessary if an SMB isn’t in a regulated industry?
Absolutely. Even without HIPAA or PCI obligations, SMBs are frequent targets due to limited defenses. Cloudtech aligns security controls to business value, not just compliance. This ensures customer data, core applications, and uptime are protected without overwhelming internal teams or over-investing in tools that don’t fit their scale.

Common security pitfalls during cloud migration, and how to avoid them
For small and mid-sized businesses (SMBs), cloud migration is an opportunity to modernize operations. However, it can also expose security blind spots if not planned carefully. Misconfigured access, exposed data, or missing compliance controls can turn a technical win into a reputational risk.
Take the case of a mid-sized healthcare provider migrating patient records to Amazon S3. The migration itself goes well, but they might overlook S3 Block Public Access by default. A week later, a routine security scan reveals that some storage buckets are publicly accessible. This puts the company at risk of violating HIPAA rules. It’s caught in time, but the instance triggers a full audit and weeks of remediation.
Incidents like this usually happen because the migration overlooks essential safeguards. This article breaks down the most common security pitfalls SMBs face during cloud migration, and shows how to avoid them with practical, preventive steps.
Key takeaways:
- Treat security as a migration stream: Security should be integrated from the planning phase through execution, not bolted on after workloads move.
- Don’t carry over legacy risks: Lift-and-shift approaches often transfer outdated controls. Always reassess configurations and patch known vulnerabilities before migration.
- IAM missteps cause the most damage: Overly permissive roles or missing MFA setups remain leading causes of breaches. Tighten access controls early.
- Compliance doesn’t auto-transfer: Moving to the cloud doesn’t automatically preserve HIPAA, PCI, or GDPR compliance. Logging, data handling, and access reviews must be revalidated.
- Small teams can win with the right tools: Cloud-native security services and automation help SMBs build strong defenses, especially when paired with expert guidance.
Key cloud migration security challenges for SMBs, and how to solve them?

Cloud migration introduces a shift in how IT environments are secured. For SMBs, this shift often happens under resource constraints, without specialized security teams or mature DevSecOps practices in place. As a result, critical vulnerabilities frequently emerge.
According to IBM’s cost of a data breach report, 40% of data breaches involved data stored across multiple environments. Breached data stored in public clouds incurred the highest average breach cost at USD 5.17 million.
Common issues like open Amazon S3 buckets, broad IAM access, insecure APIs, and unpatched workloads often stem from rushed migrations. SMBs can reduce risk by treating security as a parallel track, encrypting data, enforcing least-privilege access, automating compliance, and baking security into CI/CD pipelines.
SMBs will face many security challenges during transition, but each of them has a fix that can be implemented early to reduce cost and downtime:
Challenge 1: Data exposure during transfer or storage
When moving data to the cloud, it’s easy to assume AWS will handle encryption by default. But during migration, especially when using tools like AWS DMS or moving large datasets to Amazon S3, data can pass through unsecured channels or land in buckets without encryption turned on. That’s when it gets risky. A misstep here could expose sensitive info like customer records, financials, or health data.
The fix: To keep data protected, encryption needs to be covered in two places: when it's moving and when it’s sitting in AWS.
For data in transit, enforce TLS 1.2 or higher.
- When using AWS DMS, turn on SSL for every connection point.
- Set bucket policies in Amazon S3 to reject unencrypted uploads.
For data at rest, turn on encryption by default.
- Use AWS KMS (Key Management Service), either AWS-managed or customer-managed keys.
- Enable encryption on Amazon S3, RDS, and EBS volumes from the start.
- Use AWS Config to alert if anything’s left unencrypted.
- Keep an eye on key usage and access patterns with AWS CloudTrail.
How one SMB handled it: A growing dental clinic group migrating its patient database to Amazon RDS ran into a pitfall. Backups weren’t encrypted, and neither were the Amazon S3 uploads coming from old file exports. However, with the help of their AWS partner, they enabled SSL connections to the Amazon RDS instance, switched on encryption using a customer-managed KMS key, and applied Amazon S3 policies to block any unencrypted objects. They also routed DMS traffic through a VPN tunnel using IPSec with AES-256.
The migration wrapped without a hitch, and passed a HIPAA audit two months later.
Challenge 2: Weak or overly permissive IAM policies
Many SMBs start out with all-hands admin access just to “get things working” during early cloud stages. But that kind of shortcut doesn’t scale. Broad IAM roles, like giving full AdministratorAccess to multiple users or using wildcard permissions (*), leave the door wide open for accidents or attacks. A single compromised user account could mean access to everything from Amazon S3 buckets to billing dashboards.
The fix: Secure IAM starts with discipline, not complexity. AWS gives the tools. SMBs just need a plan.
- Least privilege first: Define roles around job functions. For example, DevOps engineers might get full access to Amazon EC2 and AWS CloudFormation, but only read access to Amazon S3.
- Use IAM policies with explicit, scoped permissions instead of wildcards.
- Enforce MFA (Multi-Factor Authentication) for all users, especially those with console access.
- Centralize identity using AWS IAM Identity Center (formerly AWS SSO), and connect it to the existing directory (like Microsoft AD or Okta).
- Set up regular reviews using IAM Access Analyzer to catch unused permissions or over-provisioned roles.
How one SMB handled it: A fintech startup had six developers sharing a root account during testing. Fast, but dangerous. On the suggestion of their AWS partner, they split out individual IAM roles, restricted access based on team functions, and required MFA for each user. They implemented IAM Identity Center and linked it with Google Workspace for strong login control. Within a week, they went from full-access chaos to tight, auditable roles that passed their first investor security review.
Challenge 3: Misconfigured cloud environments
Default settings in AWS are designed for flexibility, not security. That’s fine when spinning up test environments, but it’s risky in production. It is easy to overlook things like open Amazon S3 buckets, 0.0.0.0/0 rules in security groups, or disabled encryption on Amazon RDS or EBS volumes. These misconfigurations leave systems exposed to the internet or unencrypted by default.
The fix: Security misconfigurations are preventable with the right guardrails in place.
- Use AWS Config to continuously scan for misaligned settings across services (e.g., unencrypted volumes, non-compliant IAM roles).
- Enable AWS Security Hub to consolidate security alerts and automatically check the environment against AWS best practices.
- Trusted Advisor provides real-time recommendations across security, performance, and cost, flagging things like publicly accessible storage or overly broad access rules.
- Establish service control policies (SCPs) in AWS Organizations to prevent high-risk configurations before they happen.
- Automate remediation with tools like AWS Systems Manager Automation or integrations with third-party platforms like Palo Alto Prisma Cloud or Datadog.
How one SMB solved it: A healthcare tech company found that one of its Amazon S3 buckets used for diagnostic image uploads was accidentally made public during testing. However, with guidance from their AWS partner, they activated Security Hub and AWS Config, which flagged the exposure. They locked down the bucket, enforced encryption at rest, and added guardrails to prevent similar issues in future environments. That quick action helped them avoid a serious HIPAA compliance violation.

Challenge 4: Unsecured APIs and integration points
During migration, existing APIs used for mobile apps, third-party integrations, or internal tools are often reused without being reassessed for cloud exposure. What was once protected behind a corporate firewall might now be reachable over the public internet. Without safeguards like authentication, rate limiting, or request validation, these endpoints become easy targets for abuse, injection attacks, or data exfiltration.
The fix: AWS offers purpose-built tools to lock down APIs without complicating development:
- Use Amazon API Gateway to serve APIs through a managed layer that supports throttling, access control, and monitoring out of the box.
- Protect public endpoints with AWS WAF (Web Application Firewall) to block common attack patterns like SQL injection or cross-site scripting.
- Enforce authentication and authorization using Amazon Cognito, custom tokens, or IAM roles for internal services.
- Log and monitor API activity with CloudWatch Logs and AWS X-Ray to detect anomalies in usage or performance.
- Use resource policies and VPC links to limit API access to only trusted networks when needed.
How one SMB solved it: A fintech startup that migrated its customer dashboard to AWS was exposing internal APIs for billing and account updates without authentication. After noticing unusual traffic patterns, their AWS partner helped deploy API Gateway in front of the services, integrated AWS WAF to filter malicious traffic, and implemented OAuth2 authentication through Cognito. These changes shut down the vulnerability and gave the team better visibility into API usage going forward.
Challenge 5: Rehosting without revisiting security posture
Many SMBs choose a lift-and-shift approach for speed, migrating workloads “as-is” to the cloud. But this often means legacy vulnerabilities make the jump too. These can include hardcoded credentials in config files, outdated OS versions, unpatched libraries, or services running with admin-level access. Once in the cloud, these overlooked issues become more dangerous due to increased exposure and scale.
The fix:
A successful rehost still needs a security checkpoint before workloads go live in AWS:
- Run pre-migration assessments to flag risky dependencies or OS-level vulnerabilities.
- Use AWS Systems Manager Patch Manager to automate patching for Amazon EC2 instances across both Linux and Windows.
- Store and rotate credentials securely using AWS Secrets Manager instead of hardcoding them in applications.
- Use Amazon Inspector to scan for known CVEs and misconfigurations as soon as the workload is in AWS.
- Apply IAM roles instead of access keys to give services temporary, scoped permissions.
How one SMB handled it: A regional HR software company rehosted its on-prem application servers to Amazon EC2 with minimal changes. Post-migration, they found hardcoded database credentials in application configs and several unpatched packages. With guidance from their AWS partner, they used AWS Inspector to identify vulnerable packages, automated OS patching via AWS Systems Manager, and moved credentials to AWS Secrets Manager. This not only improved their security posture but also passed a third-party audit required for a new enterprise client.
Challenge 6: Gaps in compliance visibility
When SMBs migrate workloads to the cloud, especially in regulated industries like healthcare or finance, compliance requirements can slip through the cracks. Teams often lose visibility into how HIPAA, PCI-DSS, or GDPR controls are being enforced in the new environment. Manual tracking gets harder across multiple accounts or regions, and missteps, like missing encryption, improper access logging, or insecure storage, can result in violations and penalties.
The fix: Maintaining compliance in AWS requires continuous monitoring, not just upfront configuration:
- Enable AWS CloudTrail to log all account activity and API calls. This creates a detailed audit trail for compliance audits.
- Use AWS Config and managed Config Rules to automatically track whether resources like Amazon S3, RDS, and IAM follow the compliance baseline (e.g., encryption enabled, public access blocked).
- Set up conformance packs for specific frameworks like HIPAA or PCI-DSS to apply a consistent set of controls across accounts.
- Use the AWS Well-Architected Tool, specifically the Security Pillar, to review workloads before and after migration for policy alignment and security gaps.
How one SMB handled it: A mid-sized healthtech company moved its appointment scheduling system to AWS. They assumed compliance would carry over, but a review showed their Amazon S3 backups lacked encryption and IAM roles had excessive permissions. Working with an AWS partner, they enabled Config Rules to enforce encryption and AWS CloudTrail for tracking changes. They also ran an Amazon Well-Architected review to close remaining gaps, helping them meet HIPAA standards before relaunch.
Challenge 7: Lack of cloud security expertise
For many SMBs, in-house IT teams are strong on traditional infrastructure but haven’t had the time or budget to go deep on cloud security. This creates blind spots during migration, especially around the shared responsibility model, IAM configuration, and native tools like CloudTrail or Security Hub. Without that context, it’s easy to miss critical setup steps or misconfigure access and logging.
The fix: Bridging the knowledge gap early helps avoid security missteps:
- Start with AWS’s free training modules on cloud security fundamentals to ground the team in core concepts.
- Use the AWS Shared Responsibility Model as a guide to define exactly what the team is responsible for versus what AWS secures.
- Involve a certified AWS Partner like Cloudtech during the planning phase. They can help design secure landing zones, set guardrails, and handle configurations that may be unfamiliar to internal teams.
- Establish a security review checkpoint for each migration phase, including planning, testing, and cutover.
How one SMB handled it: A regional payroll service moving off legacy servers wasn’t familiar with IAM best practices or how to use AWS CloudTrail. They worked with an AWS partner to define scoped roles, implement least privilege policies, and enable centralized logging across accounts. As a result, they avoided costly misconfigurations, and their internal team gained confidence by learning alongside the migration.
Challenge 8: Inconsistent security across hybrid environments
Many SMBs don’t move everything to the cloud at once. For months, or even years, they run in a hybrid model, with some systems still on-premises while others operate in AWS. The problem? Security policies often evolve separately. SMBs might have strong IAM rules and logging in AWS, but loose firewall rules or missing audit trails on-prem. That gap creates room for lateral attacks, especially if identity and access aren’t unified.
The fix: To secure hybrid environments, SMBs need to standardize their security posture across both legacy and cloud systems:
- Use AWS Organizations with Service Control Policies (SCPs) to enforce guardrails across all AWS accounts from day one.
- Deploy AWS GuardDuty for real-time threat detection and anomaly alerts across cloud workloads.
- Integrate CloudTrail logs with on-prem SIEM tools or set up AWS Security Hub to centralize findings across environments.
- For identity, consider extending Active Directory to AWS using AWS Directory Service to maintain consistent user access policies.
How one SMB handled it: A mid-sized manufacturing firm moved its CRM and analytics stack to AWS but kept its ERP on local servers. Initially, access to cloud apps required MFA, but ERP access was unchanged. After a minor breach via a compromised ERP credential, they worked with an AWS partner to align IAM, deploy GuardDuty, and use Security Hub to monitor both sides. That consistency helped shut down potential gaps, and passed their next audit without issues.
Challenge 9: DevOps speed outpacing security
For SMBs adopting DevOps, the shift to rapid releases and automated deployments is a big win. But that speed can outpace security. Developers may push code that includes hardcoded secrets, misconfigured IAM roles, or unvetted open-source libraries, often without security teams catching it until after deployment. In small teams, security reviews are sometimes skipped entirely to meet deadlines.
The fix: Security needs to be embedded early in the software delivery pipeline, not bolted on after deployment:
- Integrate static application security testing (SAST) tools like SonarQube or Amazon CodeGuru Reviewer into the CI/CD process.
- Use AWS Secrets Manager to eliminate hardcoded secrets in source code.
- Add IAM policy linting with tools like CloudFormation Guard or IAM Access Analyzer to validate roles before they're deployed.
- Apply pre-deployment scanning using Amazon Inspector for EC2 or container images.
How one SMB handled it: A SaaS startup was deploying updates twice a week, but after an incident involving an exposed API key in Git, they realized speed was coming at a cost. By embedding CodeGuru, Secrets Manager, and policy validation into their CI/CD pipelines, they caught risky changes early without slowing down releases.
Challenge 10: Cloud-to-cloud migrations without revalidation
When SMBs migrate workloads between cloud providers, or even between AWS accounts, they often assume existing security settings will carry over. But policies, encryption keys, and IAM roles don’t always translate as one might expect. This can result in missing resource-level permissions, broken encryption, or inadvertently exposed services. Something as simple as forgetting to reapply an Amazon S3 bucket policy in a new account can make private data public.
The fix: Treat every cloud-to-cloud migration as a clean slate for security. That means:
- Re-auditing all IAM roles, bucket policies, and VPC settings post-migration.
- Rotating credentials and API keys to invalidate old access paths.
- Using AWS IAM Access Analyzer and AWS Config to validate resource sharing and compliance in the new environment.
- Running automated validation scripts to confirm encryption settings (via KMS), security groups, and ACLs are correctly enforced.
- Conducting a post-migration security audit, ideally with help from a partner or AWS Well-Architected Framework review.
How one SMB handled it: A fintech SMB moved their analytics pipeline from one AWS account to another to separate environments by function. After the migration, data from an Amazon S3 bucket became accessible publicly due to a missing policy reattachment. They avoided a breach thanks to an automated Config rule that flagged the misconfiguration within minutes, but it was a close call. Post-migration auditing is now part of every internal change request.
Pro tip: Working with an AWS Partner gives SMBs access to specialized cloud security expertise that internal teams may not have. Partners can spot hidden risks early, before they lead to misconfigurations, compliance gaps, or downtime. Their experience across similar migrations helps implement preventive controls from day one, not after issues arise.

How does Cloudtech help SMBs migrate securely without the guesswork?

Security missteps during cloud migration don’t just lead to technical debt, they can expose sensitive data, disrupt operations, or trigger compliance violations. For SMBs without deep in-house cloud security expertise, the risks are real and costly. That’s where Cloudtech steps in.
As an AWS Advanced Tier Services Partner, Cloudtech brings proven, security-first cloud migration strategies tailored for SMBs. Instead of leaving security as an afterthought, Cloudtech helps businesses proactively identify risks, harden environments, and ensure secure transitions without slowing down progress.
What Cloudtech Delivers:
- Secure-by-design landing zones: Before migrating anything, Cloudtech builds secure AWS foundations using AWS Control Tower, IAM baselines, KMS encryption defaults, and centralized logging. This avoids costly rework and ensures regulatory alignment from the start.
- Guided, risk-aware migration execution: Every step, whether rehosting, replatforming, or refactoring, is reviewed through a security lens. Cloudtech uses AWS CloudTrail, AWS Config, and Amazon GuardDuty to maintain visibility, while applying access controls, encryption, and API protection tailored to each workload.
- Post-migration security assurance: Once systems are live, Cloudtech doesn’t walk away. The team helps SMBs validate settings with AWS Security Hub and AWS Trusted Advisor, set up ongoing compliance tracking, and educate internal teams on cloud-native security responsibilities.
With Cloudtech, SMBs don’t have to gamble with security or figure it out as they go. They get a partner who understands what’s at stake, and how to secure it.

Wrapping up
For SMBs, secure cloud migration is about building long-term resilience. Security gaps don’t always show up right away, but when they do, they can disrupt operations, break customer trust, or result in regulatory fines. The difference lies in how early and how thoroughly risks are addressed.
Cloudtech helps SMBs take a proactive, structured approach. From security assessments and IAM hardening to landing zone design and compliance mapping, every phase is built to reduce exposure without slowing down the project. With Cloudtech, businesses don’t just move to the cloud, they move securely, with confidence and control.
Ready to migrate without the security guesswork? Connect with Cloudtech.
FAQs
1. What typically causes security incidents during a cloud migration?
Security issues often arise from configuration oversights, such as open storage buckets, overly broad IAM permissions, or unencrypted data transfers. These risks usually stem from reusing legacy setups or skipping validation steps during a rushed migration.
2. Is lift-and-shift riskier from a security standpoint?
It can be. When SMBs lift legacy systems into the cloud without adjusting their security posture, they risk carrying over hardcoded credentials, unpatched software, or outdated controls. Without remediation, these gaps become entry points for attackers in the new environment.
3. Which compliance areas tend to slip during cloud transitions?
During migration, SMBs can lose visibility into where data resides, who can access it, and whether logging is in place. This creates gaps in compliance with standards like HIPAA, PCI-DSS, or GDPR. Without deliberate configuration of services like AWS CloudTrail or AWS Config, audits may flag issues post-migration.
4. How can a business validate its cloud environment is secure after migration?
A post-migration audit should cover IAM roles, encryption status, exposed ports, and API access controls. AWS tools such as Security Hub, Trusted Advisor, and Inspector provide automated checks to help teams catch and resolve vulnerabilities early.
5. Can smaller teams realistically manage cloud security without full-time specialists?
Yes, especially when supported by structured tools and expert guidance. By leveraging AWS security frameworks, managed services, and automation, small teams can maintain strong security postures. Many SMBs benefit from partnering with cloud specialists who guide the process and upskill internal staff along the way.
Key benefits of cloud migration for SMBs
According to G2, 60% of organizations say the cloud has directly contributed to more consistent and sustainable revenue growth over the past year. Over 40% have fully realized key benefits like stronger service delivery, greater business agility, and improved continuity.
Before migrating, many SMBs struggled with high infrastructure costs, rigid legacy systems, limited IT bandwidth, and slow, unreliable performance. Scaling was hard. Switching tools or vendors was even harder.
Migrating to the cloud like AWS changed that. Businesses launched faster, scaled on demand, and reduced operational overhead. Services like Amazon EC2, Amazon RDS, AWS Fargate, Amazon CloudWatch, and AWS Backup gave SMBs the tools to build efficiently and stay resilient.
Many of today’s high-growth SMBs are partnering with AWS experts like Cloudtech to move their core systems to the cloud. This blog breaks down the benefits of AWS cloud migration, and how working with AWS partners can maximize each of these benefits.
Key takeaways:
- AWS isn’t just scalable, it enables growth: SMBs gain the flexibility to scale up or down based on demand, without overcommitting on infrastructure.
- Operational overhead shrinks, so teams can focus on building: Automation, monitoring, and managed services free up bandwidth across IT and engineering.
- Modern architecture unlocks innovation: From data lakes to containerized workloads, AWS allows SMBs to tap into AI, machine learning, and serverless without rebuilding from scratch.
- Security and compliance are built in, not bolted on: With AWS’s native services and Cloudtech’s secure-by-design approach, businesses can meet industry standards without slowing innovation.
- Cost control becomes a reality, not a spreadsheet myth: Cloud-native optimization strategies help SMBs pay only for what they use, while Cloudtech ensures every dollar spent drives impact.
Why is cloud migration a smart move for SMBs? Key benefits explained

When small and mid-sized businesses shift from legacy IT systems to a cloud-native setup, they gain measurable reductions in operating costs and increase overall efficiency. Cloud migration eliminates the need for heavy upfront investments in hardware and maintenance, allowing organizations to align expenses with actual usage and direct resources toward growth initiatives.
A modern cloud environment also strengthens security, improves business continuity, and accelerates innovation. With the flexibility to scale on demand and enable real-time collaboration, SMBs are better equipped to adapt to changing market conditions, launch new services quickly, and support long-term business growth.
Here’s how each benefit contributes to helping SMBs operate more efficiently and scale with confidence:
1. Reducing costs and simplifying IT operations
Migrating to the cloud shifts SMBs away from costly, inflexible on-premises systems toward a usage-based operational model that directly aligns expenses with evolving business needs. Rather than investing heavily in hardware that may go underutilized or rapidly depreciate, organizations pay only for the resources they consume, making IT budgets more predictable and freeing up capital for growth initiatives.
How it helps businesses:
- Reduces CapEx and shifts to OpEx: Migrating to AWS allows businesses to replace physical servers and networking equipment with on-demand compute and storage services like Amazon EC2, Amazon S3, and AWS Lambda. This eliminates large upfront purchases and aligns expenses with usage patterns.
- Automates infrastructure management: AWS services like AWS Systems Manager, AWS OpsWorks, and AWS CloudFormation help automate patching, provisioning, configuration, and monitoring. It reduces the need for large IT teams managing infrastructure manually.
- Improves resource efficiency through right-sizing and scheduling: With tools like AWS Cost Explorer, AWS Compute Optimizer, and AWS Trusted Advisor, businesses can right-size Amazon EC2 instances, identify underused resources, and schedule workloads to run during off-peak hours, driving down costs further.
Example: Imagine a regional logistics company migrating its legacy data center to AWS. Instead of purchasing new physical servers before peak season, the company configures Amazon EC2 Auto Scaling. If demand spikes during the holidays, Auto Scaling automatically adds more compute resources, ensuring deliveries run smoothly—without paying for excess capacity during slower months.
By using AWS Cost Explorer, the team identifies underused storage and right-sizes instances, further lowering operational expenses. Automated backups with AWS Backup ensure that if a system issue occurs, critical data is quickly restored, supporting regulatory compliance and business continuity.
Expert insight: AWS partners like Cloudtech help businesses transition their workloads to efficient event-driven, and serverless architectures, improving scalability, minimizing idle compute, and optimizing ROI. It's how SMBs achieve more with less, without compromising on performance.
2. Adaptable and future-ready IT infrastructure
Cloud platforms give SMBs the ability to adapt fast, whether it’s to support sudden growth, test new ideas, or adjust to changing market dynamics. Instead of being locked into fixed infrastructure, businesses can scale services in or out on demand and move with agility in how they build and deploy applications.
How it helps businesses:

- Manages unpredictable demand with elasticity: Services like AWS Auto Scaling, AWS Elastic Load Balancing, and Amazon CloudFront allow businesses to automatically respond to traffic surges or drops, ensuring performance without waste.
- Accelerates delivery cycles: With AWS Lambda, AWS Fargate, and Amazon EKS, businesses can build and release new features faster using microservices and serverless architectures, cutting down deployment times and enabling experimentation.
- Supports business pivots without friction: Whether entering new markets or updating offerings, cloud-native tools adapt easily to evolving goals, enabling rapid changes without lengthy infrastructure projects.
Example: Suppose an e-commerce company faces a surge in online traffic during a major sales event. With AWS Auto Scaling, their application servers automatically spin up new Amazon EC2 instances in response, ensuring website performance remains steady for every customer, even as demand rapidly triples. At the same time, Amazon CloudFront caches product images and pages at edge locations, reducing latency and workload on origin servers for shoppers nationwide. After the sale, the infrastructure scales back down, so costs stay in line with actual usage, all without manual intervention.
Pro tip: Cloudtech’s application modernization service can help SMBs design modular, event-driven applications that scale automatically and deploy fast. With serverless and container-based architectures, businesses can move nimbly, capitalize on new opportunities, and keep infrastructure spending efficient as needs evolve.
3. Built-in security and operational continuity
Downtime, data breaches, and compliance lapses don’t just hurt SMBs, they can derail growth entirely. Cloud-native architectures provide built-in resilience, strong security measures, and recovery mechanisms that keep the business protected and operational, even when things go wrong.
How it helps businesses:
- Minimizes disruptions through redundancy: Multi-AZ (Availability Zone) and cross-region deployments ensure the data and workloads are always accessible, even if one zone experiences failure.
- Enables rapid recovery with automation: Services like AWS Backup, AWS CloudWatch, and AWS CloudTrail offer automated backup, monitoring, and alerting. This allows businesses to detect anomalies in real-time and recover faster from outages or incidents.
- Secures data end-to-end: Native tools like AWS Key Management Service (KMS), AWS Identity and Access Management (IAM), and Amazon GuardDuty help encrypt data, control access, and continuously monitor for threats or unusual behavior, ensuring regulatory compliance and peace of mind.
Example: Consider a healthcare provider moving operations to AWS in order to comply with HIPAA regulations. By activating versioning in Amazon S3 and scheduling automated backups through AWS Backup, the organization secures patient data with less manual oversight. If a local IT issue disrupts onsite files, staff can restore critical records from AWS in minutes, avoiding data loss and maintaining compliance. Continuous monitoring with AWS CloudWatch also helps identify any misconfigured permissions early, allowing the team to resolve vulnerabilities before they become a security threat.
Pro tip: Cloudtech can help SMBs design AWS environments that are not just secure, but audit-ready. From implementing automated backup strategies to setting up proactive monitoring and threat detection, Cloudtech ensures businesses stay resilient without sacrificing speed or scalability.
4. Future-ready technology for growing businesses
One of the most powerful benefits of cloud platforms for SMBs is on-demand access to cutting-edge technology, without the overhead of managing or building it from scratch. From AI and machine learning to real-time analytics and serverless computing, cloud-native services help businesses modernize operations, personalize customer experiences, and innovate faster than ever before.
How it helps businesses:

- Accelerates innovation cycles: Services like AWS Amplify and Amazon Bedrock enable rapid prototyping and deployment using low-code/no-code frameworks, meaning SMBs can build applications quickly with minimal coding by using visual tools and pre-built components, accelerating time to market.
- Enables experimentation without risk: Tools like Amazon SageMaker for ML modeling and Amazon QuickSight for business intelligence let teams test ideas, analyze trends, and build data-driven products, without setting up infrastructure or managing data pipelines.
- Lowers the barrier to entry for emerging tech: Cloud-native services abstract away the complexity of managing compute, storage, and networking, allowing SMBs to use AI, NLP, and automation tools without a dedicated R&D team.
Example: Suppose a digital marketing agency wants to improve how it delivers value to its clients. By using Amazon Comprehend, the agency can instantly analyze thousands of customer reviews and campaign interactions, extracting real-time sentiment insights without building a complex NLP system. These analytics are integrated into campaign strategies, cutting optimization timelines in half and increasing both engagement and client retention, all without hiring in-house data scientists.
Pro tip: Need to streamline forms or invoices? AWS partners like Cloudtech can help SMBs integrate AI-powered OCR and smart extraction with seamless DMS/ERP integration. For insights, Amazon Q delivers conversational dashboards and executive-ready reports. From strategy to data prep, Cloudtech ensures businesses adopt GenAI with speed, clarity, and real outcomes.
5. Anywhere access with smarter teamwork
Today’s teams work across cities, time zones, and devices. Cloud platforms make that possible by centralizing data, standardizing access, and enabling real-time communication. This allows SMBs to stay connected, aligned, and productive, no matter where people log in from. Whether it’s co-editing documents, sharing updates, or accessing systems remotely, the cloud removes friction from everyday teamwork.
How it helps businesses:
- Supports hybrid and remote work environments: With tools like AWS WorkSpaces and Amazon AppStream 2.0, employees can securely access their desktops and applications from any device, keeping operations moving even outside the office.
- Increases transparency and accountability: Built-in sharing controls and audit trails improve visibility into who’s working on what, helping managers coordinate faster and reduce errors from duplicate work.
- Ensures business continuity during disruptions: Natural disasters, hardware failures, or health crises won’t paralyze progress. Cloud-based access ensures teams stay online and productive from anywhere.
Use Case: Consider a boutique consulting firm implementing a hybrid work model. By adopting Amazon WorkDocs and AWS WorkSpaces, consultants and staff can co-edit presentations and reports in real time, whether working remotely or in person. Instead of waiting on email attachments or dealing with version conflicts, teams deliver documents 30% faster, with higher accuracy. Live feedback from colleagues and clients helps boost agility and results, without increasing IT complexity or staffing.
Pro tip: Collaboration works best when data and apps are exactly where teams need them, secure, centralized, and always accessible. AWS partners like Cloudtech can help SMBs build this foundation with cloud-native workspaces, real-time document management, and GenAI-ready data prep services.
6. Sustainable growth and profitability
Cloud platforms are about building leaner, smarter operations. For SMBs, that means using tools like autoscaling, serverless functions, and intelligent storage tiers to eliminate waste, control costs, and act on data in real time. Architecting with efficiency in mind, using containerization, infrastructure as code, and usage-based pricing models. This helps reduce both environmental impact and cloud spend, all without sacrificing speed or flexibility.
How it helps businesses:

- Drives lean, cost-effective operations: Cloud services remove the need for idle hardware and oversized capacity. With pay-as-you-go pricing and auto-scaling, businesses use only what they need, and scale up when growth demands it.
- Enables smarter planning and execution: With advanced analytics tools like Amazon Redshift and AWS Glue, businesses can predict trends, forecast demand, and respond in near real time.
- Promotes greener choices by design: Migrating to energy-efficient infrastructure in the cloud reduces emissions, especially when compared to maintaining traditional on-premises servers.
Example: Imagine a sustainable apparel company seeking to improve margins while reducing waste. By consolidating inventory and customer insights in Amazon Redshift, the company quickly identifies which products sell fastest and which lag behind. If slow-moving items are promptly discontinued, inventory waste drops significantly. Instead of overstocking, the business maintains leaner shelves, resulting in a 25% reduction in waste and an increase in profitability per product line, all while supporting its long-term sustainability goals.
Pro tip: Growth shouldn’t come at the cost of efficiency, or the environment. Cloudtech helps SMBs architect lean, future-ready systems by combining serverless infrastructure, automated analytics, and GenAI-ready data prep. With sustainability baked into the build, businesses can scale profitably and responsibly, on their terms.
How Cloudtech helps SMBs realize the full value of the cloud?

For small and mid-sized businesses, cloud adoption is only the initial phase. The measurable impact emerges when AWS services are architected to align with workload-specific needs. As an AWS Advanced Tier Services Partner, Cloudtech supports SMBs in transitioning from basic cloud setups to fully modernized, AWS-native environments designed for efficiency, performance, and long-term scalability.
Cloudtech helps turn cloud potential into measurable outcomes:
- Build a modern foundation that supports long-term growth: Cloudtech sets up cloud environments with the future in mind, from secure AWS Control Tower governance to serverless compute, auto-scaling storage, and built-in monitoring with AWS CloudWatch. This creates a resilient, right-sized backbone that supports experimentation and growth, without the sprawl or spend of legacy infrastructure.
- Make data useful, accessible, and AI-ready: SMBs often sit on valuable data they can’t use. Cloudtech transforms this into a business asset by modernizing data lakes, setting up ETL pipelines, and ensuring clean, unified access across teams. It also prepares data for advanced tools like Amazon Q and Amazon Bedrock, allowing businesses to build analytics dashboards or AI apps, without starting from scratch.
- Automate smarter with GenAI and intelligent workflows: Cloudtech helps SMBs apply AI where it matters. Whether that’s using Amazon Textract to extract key fields from forms, or applying Amazon Comprehend for document analysis, the result is faster decisions and fewer manual tasks. Through its 4-week GenAI Proof of Concept program, Cloudtech delivers working prototypes fast, minimizing risk and showing clear ROI.
- Improve collaboration and agility across teams: From AWS WorkSpaces to AppStream 2.0 and WorkDocs, Cloudtech equips distributed teams with secure access to systems and documents. That means no more versioning chaos, siloed workflows, or downtime during disruptions. Collaboration happens in real time, no matter where people work.
Cloudtech doesn’t just help SMBs “move to the cloud.” It helps them modernize how they work, with AI-ready data platforms, cloud-native security, and automation tools that support sustainable, profitable growth. From day one, the goal is to reduce complexity and maximize impact, without stretching internal teams or budgets.
Conclusion
Migrating to AWS puts SMBs on a path toward greater resilience, cost efficiency, and scalability. Embracing the cloud is more than just moving workloads. It’s about achieving agility, speed, and new opportunities for innovation and customer engagement.
Cloudtech helps SMBs go beyond basic migration with a strategy-focused approach grounded in AWS-native best practices. By combining deep technical expertise with a practical understanding of business needs, Cloudtech enables companies to automate day-to-day operations, extract actionable insights from their data, and adopt AI-driven solutions. It ensures every step delivers measurable business value.
For organizations ready to move past the constraints of legacy systems, Cloudtech offers a proven path to cloud modernization. It brings deep AWS expertise, practical strategy, and long-term support to help SMBs get more from the cloud, faster. Connect with Cloudtech to start the conversation.
FAQs
1. What types of workloads should SMBs migrate first?
Most SMBs begin with workloads that are expensive to maintain or no longer scale well. Think legacy databases, aging file servers, or ERP systems. Cloudtech helps prioritize these based on business impact, risk, and cost efficiency.
2. How long does an AWS migration project typically take?
Timelines vary, but most small and mid-sized migrations are completed in phases over 6 to 12 weeks. Cloudtech’s phased approach minimizes disruption by aligning the migration with business operations and team readiness.
3. What AWS tools does Cloudtech use during migration?
Cloudtech uses AWS-native tools like Migration Evaluator, AWS Application Migration Service (MGN), Database Migration Service (DMS), and the AWS Well-Architected Framework to ensure secure, seamless transitions with minimal downtime.
4. How does Cloudtech address compliance during and after migration?
Cloudtech designs AWS environments that align with standards such as HIPAA, SOC 2, and PCI-DSS. While not a certified auditor, Cloudtech builds infrastructure and automation that are audit-ready and security-forward.
5. What post-migration support does Cloudtech provide?
Once migration is complete, Cloudtech stays engaged, offering performance tuning, cost optimization, and long-term enablement. This includes DevOps readiness, AI adoption, and expansion into services like serverless and containerized architectures.
Get started on your cloud modernization journey today!
Let Cloudtech build a modern AWS infrastructure that’s right for your business.
