This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
Modernize your cloud. Maximize business impact.
Ransomware isn’t slowing down. In 2024 alone, global ransomware incidents surged by 37%, making up 44% of all data breaches, according to the Verizon 2025 Data Breach Investigations Report. These numbers reveal a hard truth: traditional, perimeter-based defenses are no longer enough.
To stay resilient, businesses must adopt security models designed for modern, distributed environments. This is where cloud-native security comes in, an approach that embeds protection directly into applications, workloads, and infrastructure, ensuring threats are contained, compliance is maintained, and sensitive data is safeguarded in real time.
This article explains how cloud-native security provides the agility, automation, and resilience needed to stay ahead of modern cyber threats.
Key takeaways:
- Cloud-native security is critical for SMBs: Containers, serverless, and microservices require adaptive, automated protection beyond traditional perimeter security.
- AWS offers scalable, integrated tools: Amazon GuardDuty, AWS Security Hub, AWS IAM, and AWS Audit Manager enable real-time monitoring, threat detection, and automated response.
- Automation minimizes risk and overhead: Continuous compliance checks, vulnerability scanning, and policy enforcement reduce manual effort.
- Security supports agile development: Cloud-native security integrates with CI/CD pipelines, keeping development fast and safe.
- Cloudtech adds expert value: SMBs gain a managed, scalable, and compliant security framework that protects workloads while enabling growth.
What is cloud-native security? A detailed overview
Cloud-native security is the practice of embedding security directly into applications and infrastructure that are built and operated in cloud environments. It ensures that protection is integrated across every stage of the application lifecycle from development and deployment to runtime operations.
It addresses the dynamic, distributed, and API-driven nature of modern workloads, so that security is scalable, automated, and resilient.
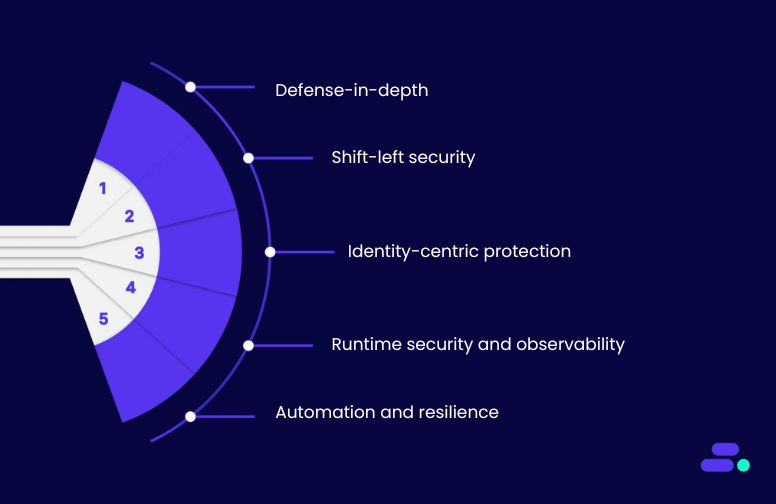
Core principles of cloud-native security:
- Defense-in-depth: Security is layered across compute, storage, networking, data, and APIs. Encryption, workload isolation, and continuous monitoring are standard practices to prevent unauthorized access and data breaches.
- Shift-left security: Security is implemented early in the software development lifecycle. Vulnerability scanning, policy validation, and automated checks are built into CI/CD pipelines to catch risks before deployment.
- Identity-centric protection: Identity and access management (IAM) becomes the new security perimeter. Short-lived credentials, role-based access control, and multi-factor authentication replace static credentials, aligning with Zero Trust.
- Runtime security and observability: Applications are continuously monitored for anomalous behavior, privilege escalation attempts, and suspicious traffic. Service meshes, intrusion detection, and real-time logging enhance visibility at runtime.
- Automation and resilience: Cloud-native environments rely on automation for patching, scaling, and recovery. Security policies are codified and enforced automatically, while integrated backup and disaster recovery solutions ensure resilience.
How cloud-native security differs from legacy models: Traditional security emphasizes fixed perimeters and manual auditing. Cloud-native security, on the other hand, is adaptive and built around distributed workloads such as containers, serverless functions, and microservices.
It prioritizes continuous monitoring, automated policy enforcement, and the ability to respond dynamically to threats in real time.
Why cloud-native security matters for SMBs? It provides scalability, cost efficiency through pay-as-you-go security services, built-in compliance automation for regulated industries, and resilience by tightly integrating with cloud backup and disaster recovery strategies.

How does AWS help SMBs establish cloud-native security for their infrastructure?
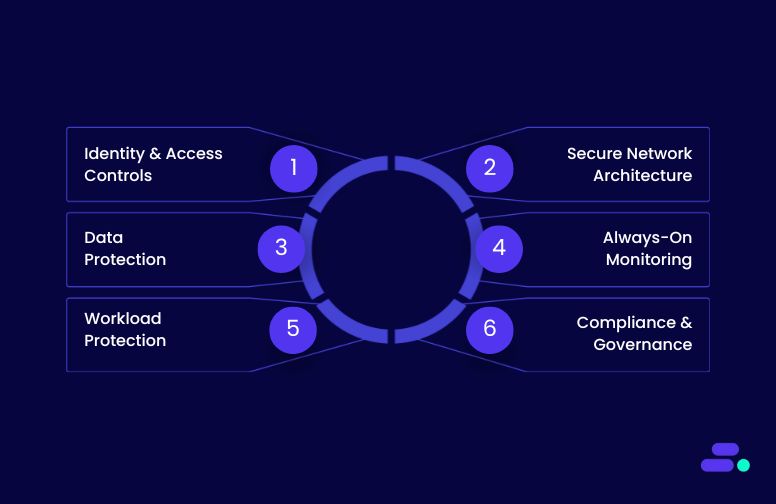
AWS embeds protection at the core of its infrastructure. Security controls span compute, storage, networking, and databases, ensuring every workload inherits a consistent baseline of protection.
With the industry’s clearest Shared Responsibility Model, SMBs know exactly which areas AWS secures (global infrastructure, data centers, and services) and which remain in their control (applications and data). This clarity helps lean teams avoid misconfigurations while focusing on business-critical needs.
But what truly sets AWS apart is the breadth and depth of its cloud-native security services. From identity and access management (IAM) to continuous threat detection (GuardDuty, Detective) to compliance automation (Config, Audit Manager), AWS offers enterprise-grade security without requiring complex third-party integrations.
Combined with automatic scalability, global compliance certifications, and seamless integration with DevOps pipelines, AWS enables SMBs to adopt “security as code” while staying cost-efficient. For growing businesses, this means faster innovation backed by security that evolves as they do.
The key features of AWS’s cloud-native security include:
1. Strong identity and access controls
Identity and access management forms the backbone of cloud-native security. In AWS, services like IAM and IAM Identity Center provide granular, least-privilege access to ensure that users and applications only get the permissions they need, and nothing more.
By combining this with features like multi-factor authentication (MFA), temporary credentials, and federated identity integration, SMBs can eliminate the risks of static credentials while maintaining agility as they scale.
How it secures modern applications:
- Minimizes attack surface by enforcing least-privilege policies across all users and workloads.
- Strengthens authentication through MFA and short-lived credentials, making account compromise far more difficult.
- Supports hybrid and multi-cloud use cases with federated identity, ensuring consistent, secure access across environments.
Use case: A financial services SMB runs a customer-facing loan processing platform on AWS. Instead of using long-term static keys, the development team authenticates via IAM Identity Center with MFA enabled.
Each developer gets time-limited credentials tied to specific roles, meaning they can only access approved resources for the duration of their work session. If an account is ever exposed, the attacker cannot escalate privileges or persist in the system, protecting both customer data and compliance posture.
2. Secure network architecture
A secure network foundation is critical for protecting cloud-native applications. AWS enables SMBs to build Virtual Private Clouds (VPCs) with isolated subnets, controlled routing, and fine-grained security groups, ensuring workloads are segmented and protected from unauthorized access.
Integrated services like AWS WAF and AWS Shield defend against external threats, including DDoS attacks, while allowing the network perimeter to adapt dynamically as workloads scale.
How it secures modern applications:
- Limits exposure by isolating sensitive workloads in private subnets and enforcing strict traffic rules.
- Protects against external threats using WAF for application-layer filtering and Shield for DDoS mitigation.
- Supports scalable, resilient architectures with centralized gateways, NAT, and routing that automatically adapt to changing workloads.
Use case: A healthcare SMB hosts patient records and appointment scheduling applications in AWS. Each application runs in a separate VPC with private subnets for sensitive databases and public subnets for web interfaces.
AWS WAF blocks malicious requests, while Shield automatically mitigates potential DDoS attacks. The team confidently scales their services, knowing sensitive data remains isolated and protected from both internal and external threats.
3. Data protection by default
Protecting data at all times is a cornerstone of cloud-native security. AWS services such as Amazon S3, Amazon RDS, and Amazon DynamoDB provide built-in encryption both at rest and in transit using AWS Key Management Service (KMS).
SMBs can use AWS-managed keys for simplicity or opt for customer-managed keys to meet strict regulatory requirements, ensuring data remains secure without complicating operations.
How it secures modern applications:
- Prevents unauthorized access by encrypting data automatically, reducing the risk of breaches.
- Supports regulatory compliance through customizable key management and auditing capabilities.
- Protects data in motion and at rest across storage, databases, and backups, ensuring end-to-end security.
Use case: A fintech SMB stores sensitive transaction records in Amazon RDS and customer documents in S3. Using AWS KMS with customer-managed keys, the team encrypts all data at rest, while TLS ensures encryption in transit.
Even when accessing data for reporting or analytics, encryption remains active, giving the SMB confidence that customer information is secure and compliant with PCI-DSS standards.

4. Always-on monitoring and threat detection
Continuous monitoring is essential for cloud-native security. AWS provides services like Amazon GuardDuty, AWS Security Hub, and Amazon Detective that give SMBs real-time visibility into their security posture.
These tools detect unusual behavior, surface actionable insights, and enable rapid response, without the need for large, dedicated security teams.
How it secures modern applications:
- Detects threats proactively by analyzing logs, network activity, and API calls to identify suspicious patterns.
- Provides centralized visibility across accounts and workloads, helping SMBs maintain a holistic security posture.
- Enables rapid response with automated alerts and integration with remediation tools, reducing potential damage from incidents.
Use case: A healthcare SMB runs patient management and telehealth applications on AWS. GuardDuty continuously monitors for anomalous API calls, while Security Hub aggregates alerts and Detective traces potential breaches.
When a suspicious login attempt is detected, the team is immediately notified and can remediate before any sensitive patient data is compromised, maintaining compliance with HIPAA standards.
5. Built-in compliance and governance
Compliance is a continuous process, not a one-time checklist. AWS provides services such as AWS Config, AWS Audit Manager, and AWS Control Tower to help SMBs maintain alignment with industry standards like HIPAA, GDPR, and PCI-DSS.
These tools automate policy enforcement, continuously monitor configurations, and generate audit-ready reports, reducing manual overhead and human error.
How it secures modern applications:
- Ensures ongoing compliance by automatically checking configurations against regulatory frameworks.
- Simplifies audits with pre-built reporting and documentation, saving SMBs time and resources.
- Integrates governance into operations so security and compliance are enforced continuously, not just during periodic reviews.
Use case: A fintech SMB operates multiple AWS accounts across development, testing, and production environments. Using AWS Control Tower, the team enforces consistent policies across all accounts.
Config continuously monitors changes in resource configurations, while Audit Manager produces compliance reports for PCI-DSS and GDPR. This enables the SMB to confidently run applications and handle sensitive customer data without worrying about non-compliance or manual audit burdens.
6. Workload and application protection
Modern applications often use containers, serverless functions, and microservices, which require specialized security approaches. AWS provides tools like Amazon Inspector, AWS Fargate security features, and Amazon EKS integrations to automatically detect vulnerabilities, enforce best practices, and protect workloads without disrupting development workflows.
How it secures modern applications:
- Detects vulnerabilities proactively in containers, serverless functions, and orchestrated workloads.
- Integrates seamlessly with DevOps pipelines, ensuring security checks happen continuously without slowing releases.
- Enforces runtime protection to safeguard applications while they operate, reducing the risk of exploitation.
Use case: An SMB developing a SaaS analytics platform deploys microservices on Amazon EKS and serverless APIs with AWS Lambda. Amazon Inspector scans container images and Lambda functions for known vulnerabilities before deployment. AWS Fargate enforces runtime isolation and security controls.
This allows the development team to iterate rapidly while ensuring that each service remains secure, compliant, and resilient against attacks.
By combining these capabilities, AWS enables SMBs to move beyond perimeter-based models and adopt security as code—automated, adaptive, and deeply integrated into every workload.

Partnering with an AWS expert like Cloudtech can accelerate SMBs’ cloud-native security journey by combining technical know-how with practical experience. An AWS partner helps design robust architectures, implement best-practice controls, and navigate compliance requirements, reducing misconfigurations, operational overhead, and risk.
How does Cloudtech help SMBs implement and maintain cloud-native security?
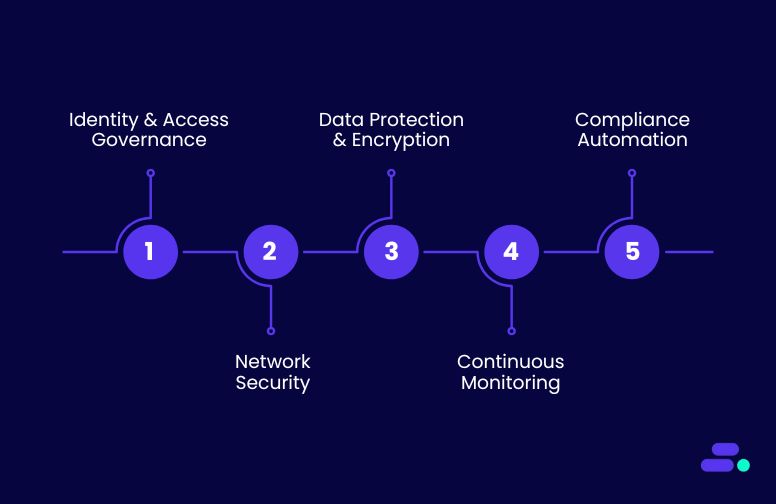
Securing modern applications in the cloud isn’t just about enabling individual controls. It’s about building a resilient, automated, and compliant security posture across all workloads. Cloudtech, as an AWS Advanced Tier Partner, helps SMBs implement cloud-native security using AWS best practices, tools, and automation, ensuring applications remain protected while supporting business growth.
Key Cloudtech services for cloud-native security:
- Identity and access governance: Cloudtech configures AWS IAM, IAM Identity Center, and federated identities to enforce least-privilege access, MFA, and break-glass procedures, minimizing internal and external risks.
- Secure network architecture: Using VPC design, security groups, AWS WAF, and AWS Shield, Cloudtech segments workloads, protects against threats, and ensures secure connectivity across environments.
- Data protection and encryption: Cloudtech applies AWS KMS, encrypted storage in S3, RDS, and DynamoDB, and automated key rotation, ensuring sensitive data is encrypted at rest and in transit.
- Continuous monitoring and threat detection: With Amazon GuardDuty, AWS Security Hub, and Amazon Detective, Cloudtech implements real-time monitoring, alerting, and automated remediation to keep SMB applications safe.
- Compliance automation and governance: Using AWS Config, Audit Manager, and Control Tower, Cloudtech continuously monitors resources, enforces policies, and generates audit-ready reports aligned with HIPAA, GDPR, PCI-DSS, or industry-specific standards.
Through these services, SMBs receive a holistic, continuously managed cloud-native security strategy that scales with their business, ensures regulatory compliance, and protects applications without slowing innovation.
See how other SMBs have modernized, scaled, and thrived with Cloudtech’s support →

Wrapping up
SMBs can no longer rely on reactive security measures. They need real-time protection, automated compliance, and scalable defenses across their applications and workloads. AWS’ suite of integrated services ensures SMBs can safeguard data, prevent breaches, and maintain regulatory alignment without heavy operational overhead.
Partnering with Cloudtech brings this strategy to life. It designs and implements comprehensive cloud-native security frameworks, enforces best-practice access controls, monitors workloads continuously, and automates compliance, giving SMBs a managed, proactive, and scalable security posture. Businesses can focus on growth while knowing their applications and data remain protected against evolving threats.
Connect with Cloudtech today to build a security strategy that adapts to business requirements.
FAQs
1. How can SMBs prioritize which workloads to secure first?
SMBs should focus on business-critical applications, sensitive customer data, and workloads exposed to the internet. Cloudtech helps identify high-risk areas and applies protections accordingly.
2. Can cloud-native security scale as my business grows?
Yes. AWS services like GuardDuty, Security Hub, and IAM automatically scale with workloads. Cloudtech ensures policies and monitoring adapt as new accounts, applications, or regions are added.
3. What role does automation play in cloud-native security?
Automation reduces human error, enforces policies consistently, and accelerates incident response. From vulnerability scanning to compliance checks, AWS services automate routine security tasks for SMBs.
4. How does cloud-native security integrate with existing DevOps workflows?
Security tools like Amazon Inspector and Fargate security features integrate seamlessly into CI/CD pipelines, enabling developers to build and deploy safely without slowing down releases.
5. Is cloud-native security cost-effective for SMBs?
Yes. By leveraging AWS’ pay-as-you-go model and Cloudtech’s optimization strategies, SMBs get enterprise-grade security without large upfront investments or excessive operational overhead.

Get started on your cloud modernization journey today!
Let Cloudtech build a modern AWS infrastructure that’s right for your business.