This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
Modernize your cloud. Maximize business impact.
Think of AWS Landing Zone as the “move-in ready house” in the cloud. The “walls, plumbing, and electricity” (security, networking, IAM) are already set up. The users just bring in the “furniture and appliances” (apps, data, workloads). It cut costs for SMBs by eliminating the trial-and-error of building a cloud foundation from scratch.
Instead of spending on custom setups, rework, or security fixes later, SMBs get a pre-configured, best-practice environment that reduces wasted engineering hours, avoids compliance penalties, and scales efficiently. This means SMBs pay only for what they use while accelerating time-to-value.
This article explores why AWS Landing Zones are essential for SMBs looking to establish a cost-efficient cloud foundation.
Key takeaways:
- Secure foundation first: A well-architected AWS Landing Zone ensures multi-account governance, compliance, and identity controls from day one.
- Scalable and resilient: Proper account structure, network segmentation, and automation enable workloads to scale reliably as the business grows.
- Compliance baked in: Continuous monitoring, logging, and guardrails help SMBs meet industry regulations like HIPAA, GDPR, and PCI DSS.
- Operational efficiency: Automation with IaC, CI/CD, and Control Tower reduces manual effort, minimizes errors, and accelerates deployment.
- SMB-first expertise matters: Partnering with Cloudtech helps SMBs adopt AWS Landing Zones quickly, avoid costly mistakes, and focus on innovation and growth.
Should SMBs opt for AWS Landing Zones?
Setting up cloud environments without structure often leads to what AWS calls “cloud sprawl”, with fragmented accounts, inconsistent security controls, and rising costs that are hard to trace. Many SMBs start by spinning up workloads directly, but this DIY approach quickly introduces technical challenges.
For example, managing multiple accounts without a consistent identity and access strategy leads to weak security boundaries, inconsistent tagging makes cost allocation nearly impossible, and lack of centralized logging leaves blind spots for compliance audits. Over time, this increases both operational overhead and risk exposure.
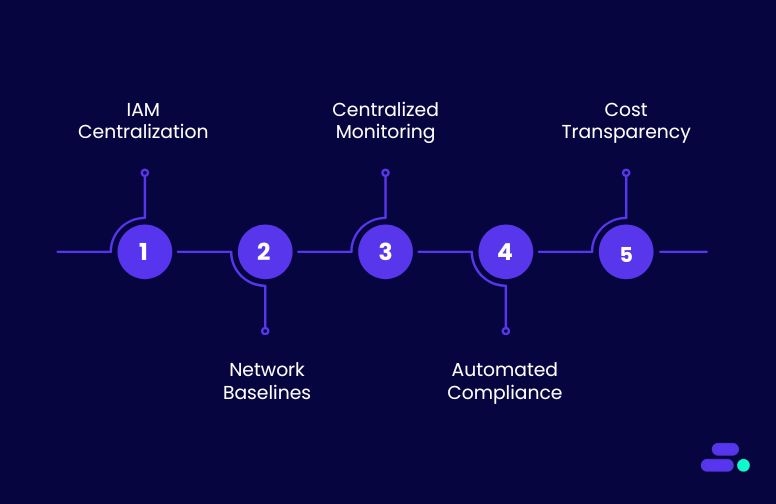
AWS Landing Zones solve these challenges by automating the setup of a multi-account, governed, and secure AWS environment from the start. They embed best practices such as:
- Centralized identity and access management (IAM): Enforces least-privilege policies across accounts and users, avoiding ad-hoc permissions.
- Network baselines: Preconfigured VPCs, subnets, and routing policies prevent common misconfigurations and enable secure communication between workloads.
- Centralized monitoring and logging: AWS CloudTrail and CloudWatch are enabled across all accounts, ensuring every activity is tracked and auditable.
- Automated compliance controls: AWS Config continuously checks for policies like encryption, region restrictions, and resource tagging, keeping environments aligned with regulations.
- Cost transparency: Standardized tagging and account structures make it easier to attribute costs by workload, project, or team, helping SMBs avoid bill shock.
For SMBs, opting for AWS Landing Zones means skipping the painful trial-and-error of building governance manually. Instead, they gain a secure, compliant, and scalable foundation where teams can innovate freely without breaking guardrails.
This balance of freedom with control makes Landing Zones not just a convenience, but a long-term enabler of sustainable cloud growth.

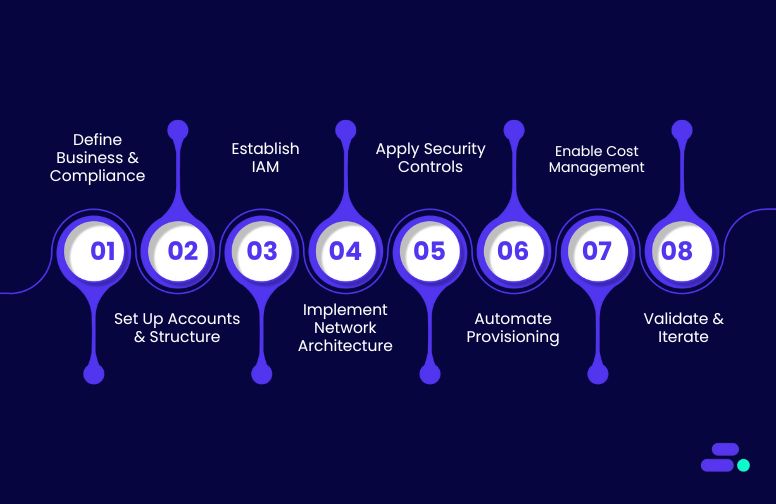
How can SMBs set up an AWS Landing Zone? Simple steps
SMBs usually opt for an AWS Landing Zone to avoid the pitfalls of piecemeal alternatives like building custom governance scripts or relying on ad-hoc account setups that rarely scale. While tools such as AWS Control Tower or manual configurations offer starting points, they often lack the consistency, automation, and multi-account governance needed as workloads grow.
An AWS Landing Zone, on the other hand, provides a pre-engineered blueprint that balances speed of setup with enterprise-grade controls, letting SMBs move faster without sacrificing security or compliance. It’s about choosing a framework that grows with the business, ensures costs and risks are transparent, and avoids costly re-engineering down the line.
SMBs can establish an AWS Landing Zone in several simple steps:
Step 1: Define business & compliance needs
This step is about setting the guardrails before building anything in AWS. It ensures that the landing zone reflects both business goals and compliance obligations such as HIPAA, GDPR, or PCI DSS.
Starting here prevents costly redesigns later, because compliance rules dictate which AWS regions can be used, how data must be encrypted, and what level of monitoring and evidence collection is required. Essentially, this step translates business and regulatory needs into concrete AWS governance policies.
How to perform this step using AWS:
- Define business outcomes such as cost optimization, scalability, or compliance-readiness, and link them to AWS Well-Architected best practices.
- Map industry regulations (HIPAA, GDPR, PCI DSS) to AWS controls using AWS Audit Manager, AWS Security Hub standards, and predefined AWS Conformance Packs.
- Establish data classification and residency rules, applying Amazon S3 encryption, AWS KMS CMKs, and AWS Service Control Policies (SCPs) to restrict unapproved regions.
- Set up identity governance through AWS IAM Identity Center for SSO, enforce MFA, and create break-glass access policies for emergencies.
- Determine resilience, logging, and retention requirements using AWS multi-AZ designs, AWS Backup vaults, and immutable AWS CloudTrail logs with long-term Amazon S3 storage.
Use case: A healthcare SMB migrating its electronic health record system begins by identifying HIPAA as the primary regulatory driver. Business goals include enabling secure telemedicine, reducing on-premise costs by 30%, and ensuring 24/7 availability of patient portals.
To meet these needs, the SMB mandates end-to-end encryption using AWS KMS, limits PHI storage to U.S. regions through SCPs, and enforces MFA for all staff handling patient data. Logging is centralized with AWS CloudTrail and retained for seven years, while resilience is ensured through multi-AZ deployments and automated backups.
These decisions produce a compliance blueprint that directly guides account setup, IAM design, and network architecture in later steps.
Step 2: Set up core accounts and organization structure
Once business and compliance requirements are clear, the next step is to establish the AWS foundation using a multi-account strategy. Instead of running everything in a single account, AWS recommends separating workloads and responsibilities across accounts for stronger security, cost visibility, and compliance alignment.
This is managed through AWS Organizations for account hierarchy and policies, and AWS Control Tower to automate account creation with guardrails. A well-designed account structure ensures that governance, security, and operational needs are consistently enforced from day one.
How to perform this step using AWS:
- Use AWS Organizations to create a multi-account hierarchy, grouping accounts by workload or environment (e.g., production, non-production, sandbox).
- Deploy AWS Control Tower to automate account provisioning and apply preventive and detective guardrails.
- Establish core accounts such as AWS Management (payer), AWS Security, AWS Log Archive, and AWS Shared Services following AWS best practices.
- Apply AWS Service Control Policies (SCPs) at the AWS Organizational Unit (OU) level to restrict unapproved regions, enforce MFA, or limit high-risk actions.
- Configure AWS Consolidated Billing and AWS tagging standards to enable accurate cost allocation across accounts and business units.
Use case: A healthcare SMB moving to AWS uses Control Tower to establish a secure multi-account structure. It creates dedicated accounts for Security (running centralized logging and GuardDuty), Log Archive (storing immutable CloudTrail logs), Shared Services (for networking and monitoring tools), and separate accounts for development and production workloads.
SCPs are applied to block the use of regions outside the U.S., and budgets are set up at the OU level for cost tracking. This structure not only enforces HIPAA compliance but also provides clear operational separation, making audits and incident response much easier.
Step 3: Establish IAM
With the account structure in place, the next step is to standardize how users and applications authenticate and gain access to AWS resources. AWS emphasizes centralized identity and access management to reduce risk, prevent privilege sprawl, and simplify audits.
Using IAM Identity Center (AWS SSO) with an external identity provider ensures a single source of truth for users, while fine-grained roles and policies enforce least privilege. This step also includes defining break-glass access procedures, MFA enforcement, and a strategy for managing service accounts and workloads.
A strong IAM foundation is critical because nearly every compliance framework requires strict identity governance.
How to perform this step using AWS:
- Integrate AWS IAM Identity Center with the corporate identity provider (e.g., Okta, Microsoft Entra ID, Ping Identity) for centralized authentication.
- Create AWS IAM permission sets aligned to roles (e.g., Developer, Auditor, Security Admin) and enforce least privilege.
- Enforce AWS multi-factor authentication (MFA) for all human access, and define break-glass root account procedures with AWS hardware MFA.
- Use AWS IAM roles for applications and cross-account access, avoiding long-lived static credentials.
- Enable AWS IAM Access Analyzer to continuously detect and remediate overly permissive policies.
Use case: A healthcare SMB implements IAM Identity Center to give staff single sign-on access to AWS accounts. Doctors and nurses are assigned read-only roles for dashboards, developers get scoped access to non-production environments, and security admins have elevated privileges with MFA enforced.
Root accounts are locked with hardware MFA and monitored through CloudWatch alarms. Service applications such as the patient portal use IAM Roles with temporary credentials instead of static keys. IAM Access Analyzer runs continuously to flag any overly broad permissions.
This ensures HIPAA compliance by controlling who can access PHI systems and providing clear evidence during audits.
Step 4: Implement network architecture
After accounts and IAM are in place, the next step is to design a secure and scalable network foundation. AWS recommends using a hub-and-spoke model with a centralized networking account, built on VPCs, Transit Gateway, and VPC peering.
The design should enforce security boundaries, support hybrid connectivity, and provide controlled internet access. Networking decisions here directly affect scalability, performance, and compliance, from how workloads connect internally to how external users access applications.
A well-structured network ensures that future workloads can be added without rework, while meeting compliance standards like encryption in transit and data residency.
How to perform this step using AWS:
- Set up a central AWS networking account to host shared resources such as AWS Transit Gateway, AWS Direct Connect, or AWS Site-to-Site VPN connections.
- Design Amazon VPCs per workload or environment, using subnets split across AWS Availability Zones for resilience.
- Implement segmentation by separating public, private, and restricted subnets, applying AWS Network ACLs (NACLs) and Amazon VPC security groups.
- Use private connectivity with AWS PrivateLink, Amazon VPC endpoints, or AWS Transit Gateway to limit exposure of sensitive workloads to the public internet.
- Centralize outbound internet traffic through shared egress points with AWS Network Firewall, AWS WAF, and Amazon GuardDuty for inspection.
Use case: A healthcare SMB hosting a patient portal and EHR system designs its AWS network with strict compliance needs. A dedicated networking account manages Transit Gateway, which connects separate VPCs for production, development, and shared services.
PHI workloads are placed in private subnets with no direct internet access, while doctors access dashboards through a secure VPN. VPC endpoints and PrivateLink are used for connecting to S3 and DynamoDB without traversing the public internet. Outbound traffic flows through a centralized egress VPC with AWS Network Firewall for inspection.
This architecture ensures HIPAA-compliant segmentation, encrypted traffic flows, and secure hybrid connectivity to the SMB’s on-prem clinic systems.

Step 5: Apply baseline security controls
Once the foundation of accounts, IAM, and networking is in place, the next step is to enforce security baselines across the environment. AWS emphasizes a security-first approach, embedding controls that protect workloads before scaling.
Baseline security ensures that all accounts consistently meet governance, compliance, and audit requirements without relying on ad hoc measures. This involves enabling detective controls, securing access, monitoring activity, and enforcing guardrails.
Establishing these controls early reduces risk, prevents misconfigurations, and simplifies audits for standards such as HIPAA, PCI-DSS, or SOC 2.
How to perform this step using AWS:
- Enable AWS Security Hub to continuously assess accounts against security frameworks (e.g., CIS AWS Foundations Benchmark).
- Activate Amazon GuardDuty, Amazon Inspector, and Amazon Macie for threat detection, vulnerability scanning, and sensitive data monitoring.
- Centralize logs with AWS CloudTrail, AWS Config, and Amazon CloudWatch, applying retention policies to meet compliance requirements.
- Use Service Control Policies (SCPs) in AWS Organizations to restrict unauthorized or high-risk actions across accounts.
- Apply encryption defaults with AWS Key Management Service (AWS KMS) keys and TLS, and enforce multi-factor authentication (MFA) for identity protection.
Use case: A financial SMB moving its loan processing workloads to AWS applies security baselines from day one. AWS Security Hub continuously checks for noncompliant resources, while GuardDuty alerts on unusual login activity. AWS CloudTrail logs are centralized into a dedicated logging account with immutable Amazon S3 storage and Glacier for long-term retention.
SCPs prevent developers from launching unapproved instance types or disabling encryption. Macie scans S3 buckets to ensure no sensitive customer data is exposed. With these controls, the SMB demonstrates compliance with financial regulations while ensuring proactive detection and rapid response to security events.
Step 6: Automate provisioning
After security baselines are established, the next priority is to ensure that all future resources are created consistently and securely. Manual provisioning often leads to drift, misconfigurations, and higher operational overhead.
AWS recommends Infrastructure-as-Code (IaC) and Control Tower to automate account setup, guardrails, and resource deployment. Automation not only accelerates onboarding but also guarantees compliance, cost control, and security are baked into every workload from day one.
This step shifts organizations from ad hoc provisioning to a repeatable, scalable operating model.
How to perform this step using AWS:
- Use AWS Control Tower Account Factory to automatically provision accounts with governance guardrails.
- Define standardized infrastructure templates with AWS CloudFormation or HashiCorp Terraform for networks, IAM roles, and workloads.
- Implement AWS Service Catalog to enable self-service provisioning of approved architectures.
- Apply CI/CD pipelines with AWS CodePipeline and AWS CodeBuild to automate infrastructure deployments and updates.
- Integrate Infrastructure as Code (IaC) templates with AWS Config and AWS Security Hub to continuously validate compliance post-deployment.
Use case: A retail SMB expanding into new regions needs to provision multiple AWS accounts for local teams. Instead of manually creating accounts, they use Control Tower’s Account Factory with pre-approved guardrails.
CloudFormation templates automatically deploy VPCs, IAM roles, and encryption policies in every account. Developers request resources via Service Catalog, ensuring they only launch compliant architectures. CI/CD pipelines deploy updates without downtime, while Config validates every new resource against security policies.
With automation in place, the retail SMB scales confidently, saving time and reducing human error.
Step 7: Enable cost management tools
Even the most secure and scalable landing zone can fail business expectations if costs spiral out of control. AWS recommends embedding cost visibility and accountability early in the foundation.
By enabling cost management tools, organizations ensure resources are tagged, budgets are enforced, and spending is continuously tracked. This step aligns cloud operations with financial governance, giving SMBs predictability and avoiding unexpected overruns.
It transforms cloud adoption from a technical exercise into a financially sustainable operating model.
How to perform this step using AWS:
- Define cost allocation tags and enforce tagging policies through AWS Organizations.
- Enable AWS Budgets to set alerts for overspending or threshold breaches.
- Use AWS Cost Explorer for trend analysis, forecasting, and identifying optimization opportunities.
- Leverage AWS CUR (Cost and Usage Reports) for granular billing insights, integrated with BI tools.
- Apply Service Quotas and SCPs to prevent uncontrolled scaling or resource misuse.
Use case: A healthcare SMB migrating its patient portal to AWS worries about unpredictable billing. They set up tagging policies to separate costs by project (portal, analytics, backup). AWS Budgets sends alerts when monthly spend nears limits, while Cost Explorer highlights underutilized EC2 instances.
By integrating Cost and Usage Reports into QuickSight, finance teams gain detailed dashboards of cloud spend. Service Quotas cap resource growth, ensuring runaway costs never occur. With these controls, the SMB balances compliance-driven workloads with predictable financial outcomes.
Step 8: Validate and iterate
Building a landing zone is not a one-time activity. It is a living framework that must evolve as business priorities, compliance requirements, and AWS services change. AWS emphasizes a cycle of validation and iteration to ensure the foundation remains secure, cost-optimized, and aligned with governance.
Continuous feedback from audits, operations, and business stakeholders helps refine the setup, ensuring the landing zone matures in tandem with the organization’s growth. This step embeds agility and resilience into the cloud journey.
How to perform this step using AWS:
- Use AWS Config and Security Hub to continuously validate security and compliance baselines.
- Run Well-Architected Reviews to identify gaps and apply AWS best practices.
- Enable CloudWatch and CloudTrail for ongoing monitoring and operational validation.
- Integrate Change Management via IaC (CloudFormation/Terraform) for safe, iterative updates.
- Conduct periodic operational and financial reviews to adjust policies, budgets, and resilience targets.
Use Case: A healthcare SMB initially designs its landing zone for HIPAA compliance and patient data management. Over time, new services like AI-driven diagnostics are added, requiring tighter identity controls and updated data retention rules.
AWS Config flags non-compliant S3 buckets, while Security Hub highlights gaps in encryption policies. Quarterly Well-Architected Reviews guide incremental improvements, and Terraform enables consistent updates without manual drift.
By iterating continuously, the SMB ensures its landing zone evolves securely, cost-effectively, and in compliance with healthcare regulations.
Building a secure, compliant, and scalable AWS landing zone is simpler with guidance from an AWS partner like Cloudtech. Beyond technical expertise, a partner ensures governance and compliance are embedded from day one, architectures scale efficiently with business demand, and operational costs remain predictable and optimized.
How does Cloudtech help SMBs build and scale on AWS Landing Zone?
Building in the cloud can feel complex, but starting with a well-architected AWS Landing Zone changes the game. It provides a secure, compliant, and scalable foundation where workloads can grow without surprises. Applications deploy faster, run reliably, and team spends less time firefighting infrastructure issues.
With Cloudtech guiding the way, SMBs can take full advantage of the landing zone: enforcing governance and compliance from day one, automating routine operations, and embedding resilience and monitoring directly into the environment.
This approach lets leaders focus on innovation and growth instead of managing scattered infrastructure, giving small teams the power to compete with much larger organizations confidently and cost-effectively.
Key Cloudtech services for SMBs to scale on AWS Landing Zones:
- Landing zone assessment & strategy: Review existing cloud or on-prem environments and design a multi-account AWS landing zone aligned with governance, compliance, and business objectives.
- Account provisioning & organization design: Automate account creation and organizational units using AWS Control Tower and AWS Organizations for secure, scalable foundations.
- Identity & access management: Centralize authentication with AWS IAM Identity Center, enforce MFA, and define roles and permission sets aligned with landing zone best practices.
- Network architecture & segmentation: Build secure VPCs, subnets, and connectivity patterns with Transit Gateway, VPC endpoints, and private networking to enforce compliance and reduce exposure.
- Baseline security & compliance automation: Integrate AWS Security Hub, GuardDuty, Config, and Service Control Policies to continuously enforce guardrails and audit-ready configurations.
Through this approach, SMBs can launch features faster, scale confidently, maintain compliance, and ensure high-performing, secure applications while optimizing costs.
See how other SMBs have modernized, scaled, and thrived with Cloudtech’s support →

Wrapping up
With a well-architected AWS Landing Zone, the cloud environment becomes more than infrastructure. It becomes a foundation for growth, resilience, and operational efficiency.
Partnering with an AWS expert like Cloudtech helps SMBs navigate the complexities of multi-account design, governance, and compliance, avoiding costly missteps while accelerating their journey from setup to production-ready workloads.
By combining AWS best practices with an SMB-first approach, Cloudtech ensures that the landing zone is secure, scalable, and ready to support evolving business needs.
Now is the time to lay a strong cloud foundation that future-proofs your operations—Cloudtech can help you get there.
FAQs
1. What makes an AWS Landing Zone different from a standard AWS account?
An AWS Landing Zone provides a pre-configured, multi-account environment with built-in governance, security guardrails, and automation. Unlike a single AWS account, it separates workloads, applies consistent policies, and scales securely as the business grows.
2. How quickly can SMBs deploy an AWS Landing Zone?
With tools like AWS Control Tower and guidance from an AWS partner, SMBs can deploy a secure landing zone in weeks rather than months, depending on complexity, compliance requirements, and account structure.
3. Can an AWS Landing Zone adapt as business priorities change?
Yes. Landing zones are designed to be flexible. Organizations can add accounts, adjust guardrails, and update policies without disrupting existing workloads, ensuring the environment evolves with business needs.
4. How does a landing zone support regulatory compliance?
AWS Landing Zones integrate native tools like Security Hub, GuardDuty, and Config to enforce compliance continuously. Policies and automated audits ensure workloads meet industry regulations such as HIPAA, GDPR, or PCI DSS.
5. Is prior AWS expertise required to implement a landing zone?
While knowledge helps, SMBs can rely on AWS partners like Cloudtech to design, deploy, and manage landing zones. This reduces risk, accelerates setup, and ensures best practices are followed from day one.

Get started on your cloud modernization journey today!
Let Cloudtech build a modern AWS infrastructure that’s right for your business.