This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
Modernize your cloud. Maximize business impact.
Nearly 40% of companies lose critical data in a cyberattack. This is a staggering number when considering what “critical” really means. It’s not just spreadsheets and documents at risk. It could be customer records, financial transactions, intellectual property, or operational systems that keep the business running day to day. For an SMB, such a loss can stall operations, erode customer trust, invite regulatory penalties, and in many cases, threaten the very survival of the business.
This is where AWS Cloud Backup becomes essential. By securely storing data in the cloud with built-in redundancy, encryption, and automated recovery options, SMBs can ensure that even if their systems are compromised, their data isn’t gone forever.
This article explores why SMBs, particularly in sensitive sectors like healthcare and financial services, can’t afford the risks of on-premises backups, and how AWS Cloud Backup delivers the efficiency, security, and resilience needed to safeguard growth.
Key takeaways:
- AWS Backup simplifies protection by centralizing policies across workloads, eliminating the complexity of managing multiple backup tools.
- SMBs gain enterprise-grade resilience with features like automated scheduling, lifecycle management, and multi-AZ redundancy.
- Costs stay optimized through intelligent tiering, ensuring businesses don’t overpay for long-term backup storage.
- Compliance is built-in with encryption, audit reports, and retention controls that align with industry standards.
- Cloudtech adds the SMB edge by tailoring AWS Backup setups to lean budgets, automating management, and providing ongoing support for growth.
Business data is in danger: The case for AWS Backup
Cybercriminals don’t just chase big enterprises anymore. They are increasingly targeting smaller businesses precisely because they assume they’re “too small to be noticed.” But attackers think that SMBs often lack dedicated security teams, rely on outdated backup methods, and can’t afford prolonged downtime. That makes their data a soft target.
Ransomware gangs, for example, don’t need to break into a global bank when an unpatched SMB server can yield thousands of sensitive records, and a quick payout. Add in the risk of accidental deletions, hardware failures, or natural disasters, and it’s clear. Every SMB, no matter how secure they believe themselves to be, sits on fragile ground.
Without modern cloud-based backup and recovery, a single breach or failure can mean lost customer trust, regulatory fines, or even closure.
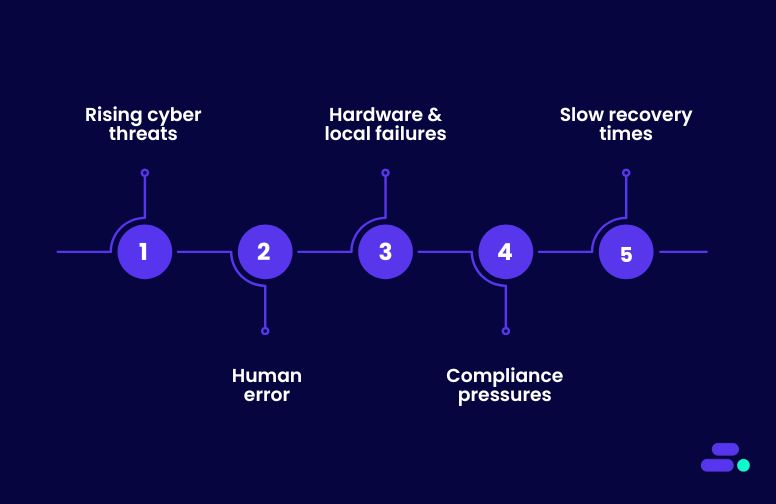
The challenges of protecting business data include:
- Rising cyber threats: Nearly 40% of companies lose critical data in a cyberattack, and SMBs are prime targets due to smaller security budgets.
- Human error: Simple mistakes like misconfigured systems or accidental deletions can wipe out essential files, often with no easy rollback.
- Hardware & local failures: On-premises servers, disks, and tape backups remain single points of failure vulnerable to wear, outages, or disasters.
- Compliance pressures: Regulations in healthcare, finance, and other industries demand strict data retention and auditability.
- Slow recovery times: Traditional backup methods can take hours or even days to restore operations, leading to costly downtime and lost productivity.
In short, relying on outdated backup strategies exposes SMBs to unacceptable risks. AWS Backup provides a modern, cloud-native alternative that is automated, scalable, and secure, so businesses can safeguard their most valuable asset: their data.

How can SMBs set up AWS Backup to protect their data?
Traditional, on-premises backup systems weigh SMBs down with costly hardware, manual upkeep, and limited scalability. They require constant patching, monitoring, and recovery testing. These are efforts that strain lean IT teams while still leaving gaps in resilience. When disaster strikes, recovery is often slow, complex, and unreliable.
AWS Backup eliminates these barriers by delivering a fully managed, cloud-native solution. Backups are automated, centrally managed, and seamlessly integrated across AWS services like EC2, RDS, DynamoDB, and EFS. With built-in encryption, isolated backup vaults, and lifecycle policies that tier data to cost-efficient storage, SMBs gain enterprise-grade protection without the burden of infrastructure management.
Most importantly, AWS Backup makes recovery fast, predictable, and scalable. Restores can be launched directly from the console, minimizing downtime and disruption. Instead of wrestling with hardware limits or complex restores, SMBs can focus on growth, knowing their data is secure, compliant, and always recoverable.
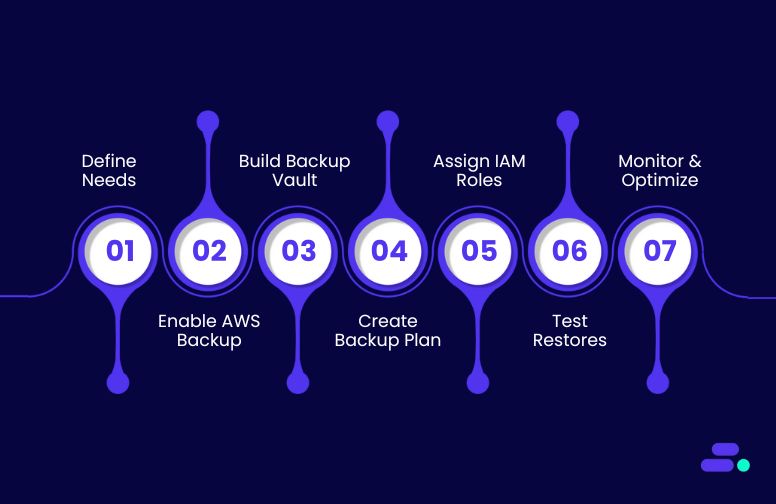
Here’s a step-by-step guide for SMBs to set up AWS Backup in a way that’s practical:
Step 1: Define business & compliance needs
Before setting up backups, SMBs need to clarify exactly what they are protecting and why. Backup strategies are only effective when aligned with business goals, customer expectations, and compliance mandates. Skipping this step often results in overpaying for storage, gaps in protection, or backups that fail when disaster strikes.
Why this step matters:
- Prevents blind spots: By identifying all critical workloads (databases, applications, file systems, VMs), businesses ensure nothing essential slips through the cracks.
- Aligns with risk tolerance: Defining RPO and RTO helps avoid both over-engineering (wasting money) and under-protecting (risking downtime).
- Meets compliance upfront: Regulations like HIPAA, GDPR, and FINRA often require specific data retention, encryption, or recovery policies.
Key AWS tools that help with this step:
- AWS Backup: Centralizes backups for EC2, RDS, DynamoDB, EFS, and even on-premises servers via Backup Gateway.
- AWS Backup Plans: Enables SMBs to set schedules, retention rules, and lifecycle policies that map directly to recovery point (RPO) and recovery time (RTO) objectives.
- AWS Backup Audit Manager: Continuously checks backups against compliance standards such as HIPAA, GDPR, or FINRA.
- AWS Organizations & Control Tower: Extend governance across multiple accounts, ensuring consistent enforcement of backup policies.
Together, these tools ensure the backup strategy is not just technical, but also aligned with regulatory requirements and long-term business goals.
Step 2: Enable AWS Backup in the console
Once the backup requirements are defined, the next step is to activate the backup so businesses can begin protecting workloads across their environment. This step essentially “switches on” the service, giving them access to centralized policies, automation, and visibility into backups.
Why this step matters:
- Centralized control: AWS Backup unifies backup management across services like EC2, RDS, DynamoDB, EFS, and even on-prem workloads.
- Multi-region flexibility: Enabling it in all operating regions ensures business continuity, even if one region experiences disruptions.
- Foundation for automation: Without enabling the service, SMBs can’t create backup plans, enforce retention rules, or automate policies.
Steps in the AWS Management Console:
- Log in → Open the AWS Management Console and search for AWS Backup.
- Select regions → Choose the regions where critical workloads (e.g., EC2, RDS, DynamoDB, EFS) are hosted.
- Enable the service → Turn on AWS Backup in those regions to allow local policy creation and backup management.
Once enabled, AWS Backup is ready to connect with workloads and apply the backup policies that will be defined in the following steps.
Step 3: Build a backup vault
With backup enabled, the next step is to set up a backup vault, a secure container where all backup copies will be stored. Think of it as the digital equivalent of a locked safe: every backup a business creates will be organized, encrypted, and isolated here, ensuring data integrity and security.
Why this step matters:
- Secure storage: Backup vaults are always encrypted, protecting sensitive business data against unauthorized access.
- Logical separation: Different vaults can be created for production, testing, or compliance workloads, reducing the risk of accidental mix-ups.
- Compliance-ready: Vault encryption keys can be AWS-managed or customer-managed (KMS), giving SMBs flexibility to meet industry regulations like HIPAA or GDPR.
Steps in the AWS Backup Console:
- Navigate to Backup Vaults → From the AWS Backup console, select Create Backup Vault.
- Name the vault → Enter a clear, descriptive name (e.g., smb-prod-backups) for easy identification.
- Set encryption → Use the AWS-managed KMS key for simplicity, or opt for a customer-managed key if compliance frameworks (HIPAA, FINRA, GDPR, etc.) require stricter control.
- Create vault → Once finalized, this vault becomes the secure destination where all backup data will be stored.
With the vault in place, SMBs can confidently move to defining backup plans that connect workloads to this secure repository.

Step 4: Create a backup plan
Once the vault is ready, the next step is to build a backup plan. A backup plan defines the rules for when, how often, and how long the data is backed up, removing manual work and ensuring consistency. This step turns backup from a one-off task into a repeatable, automated process.
Why this step matters:
- Automation reduces risk: Eliminates human error by ensuring backups always run on schedule.
- Cost optimization: Lifecycle rules automatically move older backups to low-cost storage or expire them.
- Business continuity: Critical workloads (databases, applications, file systems) are always protected without daily manual effort.
Steps in the AWS Backup Console:
- Navigate to Backup Plans → Select Create Backup Plan.
- Choose a starting point → Use a pre-built AWS template for common workloads, or build a custom plan for specific business needs.
- Set schedules & windows → Define backup frequency (e.g., daily at midnight) and choose backup windows during off-peak hours.
- Apply lifecycle policies → Example: transition to cold storage after 30 days, delete after 1 year.
- Assign resources → Attach workloads such as EC2, RDS, DynamoDB, EFS, or S3.
Once created, AWS Backup executes the plan automatically, helping SMBs reduce manual IT tasks, maintain compliance, and ensure reliable data protection.
Step 5: Assign IAM roles & policies
Even the best backup plan is only as strong as the access controls protecting it. By configuring IAM roles and policies, SMBs ensure AWS Backup has the right permissions to perform its job while minimizing risks of misuse or unauthorized access.
Why this step matters:
- Security first: Backups often contain sensitive customer and business data, making them a prime target.
- Controlled access: Only authorized users and services should be able to view, modify, or restore backups.
- Risk reduction: Enforcing least-privilege access reduces insider threats and accidental mishandling of data.
Steps in the AWS Console:
- Create a service role → Go to IAM → Roles and add a role with the managed policy AWSBackupServiceRolePolicyForBackup so AWS Backup can perform backups and restores.
- Define user policies → Decide which team members can initiate restores, view vaults, or modify backup plans.
- Apply least privilege → Grant only the specific permissions needed for each role to reduce security risks.
- Enable logging for compliance → Use AWS CloudTrail to record every action taken on backups for auditing and regulatory reporting.
With IAM roles and CloudTrail logging in place, SMBs can maintain strong access control while ensuring backup activities remain auditable and compliant.
Step 6: Test restores (don’t skip this!)
Too many SMBs assume backups will “just work” when disaster strikes, but that assumption can be costly. The real measure of a backup strategy isn’t storing data, it’s how quickly and reliably SMBs can restore it when needed. Testing restores ensures their safety net is strong and ready.
Why this step matters:
- Backups only matter if they can be restored. Regular test restores confirm that data is intact, recovery processes work as expected, and the backup system can be trusted during a real incident.
- Successful restores ensure that critical applications and datasets can come back online within defined Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs). This reduces downtime risk and keeps day-to-day operations running with minimal disruption.
- Documented restore tests provide concrete evidence for compliance audits, regulatory reviews, and internal governance. This not only satisfies industry mandates (HIPAA, FINRA, GDPR, etc.) but also demonstrates proactive risk management to stakeholders.
Steps in the AWS Backup console:
- Select a backup job → Open the Backup console, navigate to the backup job, and choose Restore.
- Restore to a new resource → Always direct restores to a new resource (e.g., a fresh EC2 volume or test RDS instance) instead of overwriting production.
- Validate the recovery → Confirm that data integrity holds and applications dependent on the restored resource run smoothly.
- Document the process → Record steps, outcomes, and any issues. This helps train teams and provides evidence for compliance audits.
By practicing restores regularly, SMBs not only build confidence in recovery but also strengthen both resilience and compliance posture.
Step 7: Monitor & optimize
A backup strategy is never “set it and forget it.” For SMBs, ongoing monitoring and optimization ensure that backups remain compliant, cost-effective, and reliable as business needs evolve. Treat this step as continuous maintenance. Small adjustments now can prevent major headaches later.
Why this step matters:
- Compliance assurance: Proves to regulators and auditors that data retention rules are being followed.
- Cost efficiency: Prevents overspending by optimizing storage classes and retention schedules.
- Operational resilience: Catches failures early, reducing downtime risk.
Key steps in AWS:
- Enable AWS Backup Audit Manager → Continuously track adherence to defined backup policies (e.g., frequency, retention) and generate audit-ready reports for regulators or stakeholders.
- Monitor costs with AWS Cost Explorer → Analyze spending patterns to identify optimization opportunities, such as moving older backups to cold storage (S3 Glacier or Deep Archive) or adjusting retention periods.
- Set real-time alerts with Amazon CloudWatch → Receive notifications for failed, delayed, or missed backup jobs, allowing quick remediation before data exposure risks arise.
- Review lifecycle rules regularly → Revisit backup frequency, retention, and storage class transitions to maintain the right balance between availability, compliance, and cost control.
Combining compliance automation, proactive monitoring, and smart cost management allows SMBs to ensure backups remain secure, efficient, and audit-proof over time.
Final Outcome: SMBs gain a centralized, automated, and compliant backup system on AWS that cuts down on manual IT work, reduces downtime risk, and protects against data loss.
Data backup isn’t enough. SMBs also need resilience, compliance, and cost control. As an AWS Advanced Tier Partner, Cloudtech helps SMBs unlock the full potential of AWS Backup, combining certified expertise with SMB-focused strategies to ensure workloads stay protected, recoverable, and audit-ready.
How does Cloudtech help SMBs set up and maintain AWS Backup?
Protecting business-critical data in the cloud isn’t just about turning on backups, it’s about designing a resilient, compliant, and cost-efficient protection strategy. Cloudtech, as an AWS Advanced Tier Partner, helps SMBs implement AWS Backup with proven blueprints, automated policies, and ongoing monitoring that align with business goals. This ensures backups don’t just exist, but actually safeguard operations while meeting budget and compliance needs.
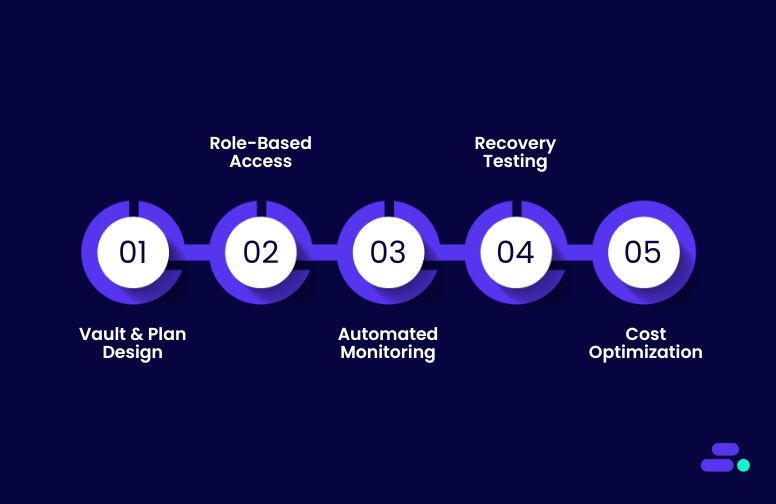
Key Cloudtech services for AWS Backup setup and management:
- Backup vault and plan design: Cloudtech configures vaults, lifecycle policies, and schedules that balance cost control with data retention and recovery needs.
- Role-based access and compliance: Using AWS IAM and CloudTrail, Cloudtech sets least-privilege access and audit trails, ensuring backups are secure and industry regulations are met.
- Automated monitoring and reporting: With AWS Backup Audit Manager and CloudWatch alerts, Cloudtech ensures issues are detected early and compliance reports are always audit-ready.
- Recovery testing and validation: Regular restore drills are carried out to verify backup integrity, train teams, and strengthen business continuity.
- Cost optimization: Cloudtech helps SMBs minimize storage costs by applying lifecycle policies, using cold storage for long-term data, and using AWS Cost Explorer for ongoing savings insights.
Through these services, SMBs gain not just data backups, but a resilient and compliant backup strategy that scales with their business, reduces risk, and ensures they can recover quickly when it matters most.
See how other SMBs have modernized, scaled, and thrived with Cloudtech’s support →

Wrapping up
Partnering with an AWS expert like Cloudtech ensures this isn’t just a basic backup setup, but a fully managed, compliant, and cost-optimized strategy. Cloudtech designs backup environments tailored to SMB needs, automates policies, validates recovery, and provides continuous oversight so data is always protected and always recoverable.
With Cloudtech, SMBs can move beyond fragile, expensive backup systems and embrace a cloud foundation that strengthens resilience, ensures compliance, and frees teams to focus on growth.
Connect with Cloudtech today to build a backup strategy that’s as dynamic as your business.
FAQs
1. Can AWS Backup support both cloud-native and hybrid workloads?
Yes. AWS Backup natively protects AWS resources, but it can also extend to on-premises workloads through AWS Storage Gateway, giving SMBs a unified backup strategy across hybrid environments.
2. How does AWS Backup handle data encryption?
All backups are encrypted at rest using AWS Key Management Service (KMS). This ensures that sensitive business data remains secure and compliant with industry standards.
3. What’s the difference between AWS Backup and manual snapshotting?
Snapshots require manual setup and tracking, while AWS Backup automates scheduling, retention, and lifecycle policies. This reduces human error, improves consistency, and saves operational time.
4. How can SMBs avoid paying for unnecessary backup storage?
By setting lifecycle policies, older backups can automatically transition to lower-cost storage tiers like Amazon S3 Glacier or Glacier Deep Archive, optimizing spend without sacrificing compliance.
5. What kind of monitoring and reporting does AWS Backup provide?
Through AWS Backup Audit Manager, businesses get compliance dashboards, audit-ready reports, and detailed logs to demonstrate adherence to regulations and internal policies.

Get started on your cloud modernization journey today!
Let Cloudtech build a modern AWS infrastructure that’s right for your business.