This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
Modernize your cloud. Maximize business impact.
Backing up Amazon S3 data is no longer a manual or fragmented task for small and medium-sized businesses (SMBs). With AWS Backup, they can have access to a centralized, fully managed service that automates the creation, storage, and restoration of Amazon S3 backups across the environment.
Businesses can define a single backup policy and apply it across all Amazon S3 buckets. AWS Backup then automatically handles backup creation and securely stores the data in encrypted backup vaults. Whether the need is for continuous backups to enable point-in-time recovery or periodic backups for long-term retention, the setup is both flexible and scalable.
This guide outlines how SMBs can configure and manage Amazon S3 backups using AWS Backup. It also covers how to schedule backups, apply retention rules, and restore data efficiently.
Key takeaways:
- Centralized and automated: AWS Backup centralizes S3 backup management with automated policies, reducing manual effort and ensuring consistent protection.
- Flexible recovery: Supports point-in-time restores and cross-bucket recovery, ideal for operational resilience and regulatory needs.
- Built-in security and compliance: Encrypted vaults, IAM controls, and audit tracking help SMBs meet HIPAA, PCI, and other standards.
- Optimized for cost and scale: Lifecycle policies and cold storage options align backup strategies with retention goals and budget constraints.
- Cloudtech makes it turnkey: As an AWS partner, Cloudtech helps SMBs deploy secure, scalable S3 backups quickly, with governance, automation, and recovery built in.
Getting started with AWS S3 backup
AWS Backup provides native integration with Amazon S3, allowing SMBs to manage backup and restore operations across their cloud workloads centrally. This integration extends beyond S3 to include other AWS services like Amazon EC2, Amazon RDS, Amazon DynamoDB, and Amazon EFS. This allows consistent, policy-driven protection from a single control plane.
Using AWS Backup, teams can define backup plans that include Amazon S3 buckets, automate backup scheduling, enforce retention policies, and ensure encryption at rest. All backups are stored in AWS Backup Vaults. They are dedicated, encrypted storage locations that isolate backup data from primary environments.
Key capabilities of AWS Backup for S3:
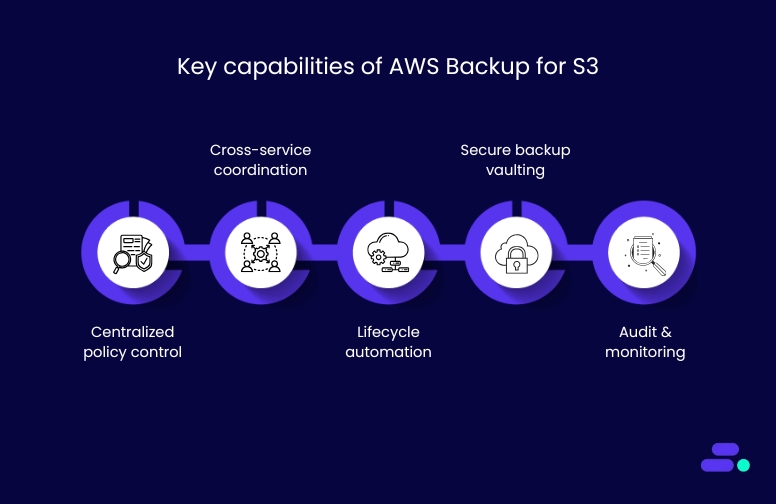
- Centralized policy control: Define backup rules once and apply them across multiple services and Amazon S3 buckets.
- Cross-service coordination: Align Amazon S3 backup schedules with other workloads like Amazon EC2 or databases to streamline protection.
- Lifecycle automation: Automate backup creation, retention, and deletion to meet compliance requirements without manual intervention.
- Secure backup vaulting: Use AWS Key Management Service (KMS) and IAM policies to restrict access and protect backup data.
- Audit and monitoring: Track backup compliance and operational events using AWS Backup Audit Manager.
This centralized architecture simplifies operations for SMBs that may not have dedicated infrastructure teams. It ensures data is consistently protected, retained, and auditable across the AWS environment.
How to plan and configure AWS S3 backup?
AWS Backup offers a centralized, policy-based approach to managing S3 backups. For SMBs, this means eliminating ad-hoc scripts and enabling consistent protection across environments.
Backup plans are created using AWS Backup’s console or API, defining:
- Backup frequency: hourly, daily, or weekly schedules
- Lifecycle rules: define when to transition to cold storage or delete
- Resource targeting: apply plans to tagged Amazon S3 buckets across accounts
- Backup vault selection: route backups to encrypted, access-controlled vaults
Each plan is reusable and version-controlled, allowing consistent enforcement of retention and compliance policies.
Continuous vs. Periodic Backups for Amazon S3:
Important notes during setup:
- Amazon S3 Versioning must be enabled on all buckets assigned to backup plans. Without it, AWS Backup cannot perform recovery operations.
- Unassigned buckets are excluded from protection. Each bucket must be explicitly added to a policy or assigned via AWS Resource Tags.
- Backup plans are independent of lifecycle policies in Amazon S3. Backup retention settings apply only to backup copies, not live bucket data.
Pro tip: While AWS services provide the building blocks, an AWS partner like Cloudtech can help businesses implement backup strategies that fit business and compliance requirements.
Automation and orchestration for Amazon S3 data backups
Managing backups at scale is critical for SMBs aiming to maintain data resilience, meet compliance needs, and reduce operational overhead. AWS Backup offers a structured, centralized way to automate backup processes for Amazon S3 data through policy-driven orchestration, aligned with AWS Organizations and tagging standards.
Automating backup scheduling and retention:
Manual scheduling across individual buckets is prone to misconfigurations. A consistent backup cadence across environments ensures regulatory alignment and simplifies data lifecycle management.
Here’s how to set it up:
- In the AWS Backup console, create a backup plan that includes backup rules defining frequency, backup window, lifecycle transitions, and retention.
- Assign Amazon S3 buckets to the plan manually or dynamically via resource tags.
Recovery points are automatically generated, retained, and expired based on the defined policies. This automation ensures that all eligible Amazon S3 data is protected on a predictable schedule without human intervention.
Centralized configuration across accounts:
SMBs often use multiple AWS accounts for development, production, or business units. Without centralized control, backup management becomes fragmented.
To implement centralized configuration across accounts, these steps can be followed:
- Set up AWS Organizations and designate a management account to handle backup policy enforcement.
- Enable cross-account backup management through delegated administrator roles in AWS Backup.
- Apply organization-wide backup policies from the management account to all member accounts or a selected subset. This avoids inconsistent retention policies across business units.
- Use AWS Backup Audit Manager for consolidated visibility across accounts, tracking whether defined policies are being enforced consistently.
This structure enables IT teams to implement guardrails without micromanaging each account, improving governance and oversight.
Policy enforcement using tagging:
Along with centralized management through AWS organizations, tags can be used to automate backup inclusion dynamically. As new resources are created, correctly tagged Amazon S3 buckets are auto-assigned to backup plans.
Some key strategies can help SMBs improve the effectiveness of tags:
- Standardize tagging across the organization using AWS tag policies (e.g., Backup=true, DataType=Critical, Environment=Prod).
- When creating or updating a backup plan, specify tag-based resource selection criteria.
As a result, AWS Backup continuously scans for Amazon S3 buckets that match the specified tags and automatically includes them in the plan. This ensures no bucket is unintentionally left out of compliance.
Tags also allow for fine-grained policy targeting, such as applying different backup rules for dev vs. production environments or financial vs. marketing data.

For small and mid-sized businesses, setting up automation and orchestration early eliminates operational drift, simplifies audits, and reduces dependency on manual oversight.
Restoring Amazon S3 data: options, architecture, and planning
For SMBs, data recovery is not just about restoring files. It’s about minimizing downtime, preserving trust, and meeting regulatory requirements. AWS Backup offers flexible restore capabilities for Amazon S3 data, allowing teams to respond quickly to incidents like accidental deletions, corruption, or misconfigurations.
For example, suppose a healthcare provider’s admin team accidentally deletes patient billing records stored in an Amazon S3 bucket. In that case, AWS Backup allows recovery to a previous point-in-time, such as the snapshot from the previous day. The data can be restored into a separate, access-controlled staging bucket where compliance teams can review and validate the records before moving them back into the production environment.
Restore options for Amazon S3:
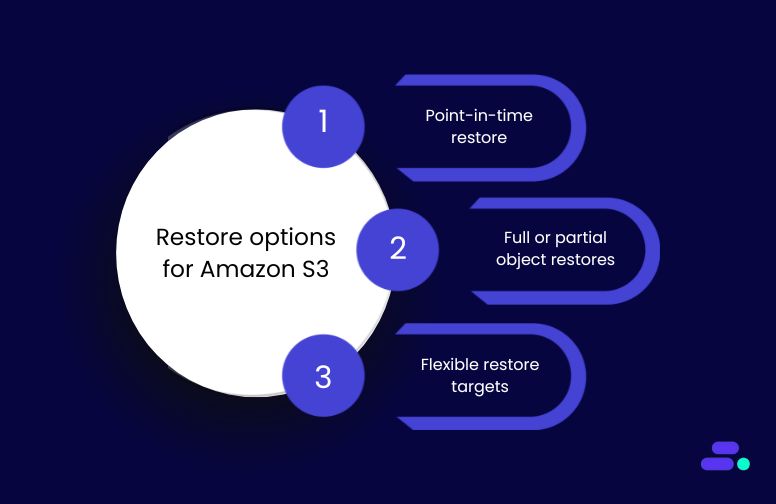
- Point-in-time restore (using continuous backups): Enables recovery to any second within the past 35 days. Useful for rollbacks after accidental overwrites or ransomware events.
- Full or partial object restores: Restore entire buckets or select specific objects. This helps recover a single corrupted report or database export without needing to recover the entire dataset.
- Flexible restore targets: Choose to restore to the original S3 bucket or a new one. Restoring to a new bucket is ideal for testing or when isolating recovered data for audit purposes.
Cross-account and cross-region restores:
Many SMBs operate in environments with separate AWS accounts for development, staging, and production. Others may require disaster recovery in a different AWS Region to meet compliance or resiliency goals.
- Cross-account restores: Restore data from a staging account to a production account after verification has been completed. Requires IAM role trust relationships and policy permissions.
- Cross-region restores: A healthcare company with compliance needs in the EU can restore US-hosted S3 data into the Frankfurt Region using backup copies. This supports data residency and disaster recovery objectives.
Note: To perform cross-region restores, ensure the backup vault supports multi-region use and that the destination Region is selected when configuring backup plans.
Architectural considerations:
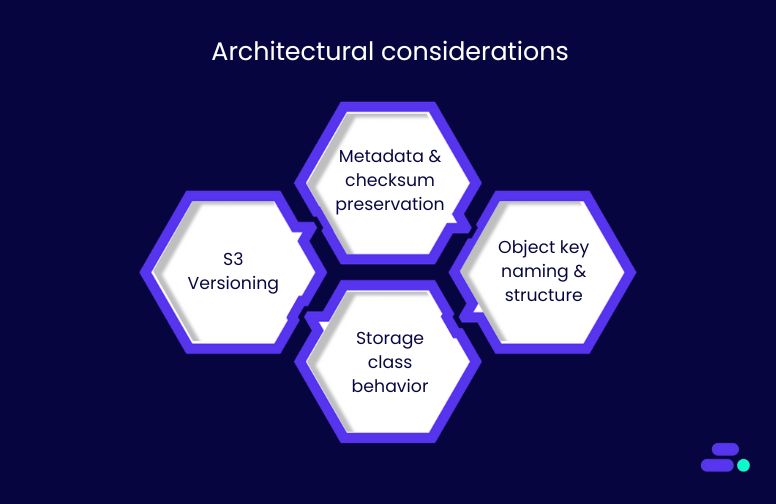
Successful restores require a well-configured environment. Key factors include:
- Amazon S3 Versioning: Must be enabled to support continuous backups and point-in-time recovery. Without it, AWS Backup cannot track or restore object-level changes.
- Metadata and checksum preservation: Some metadata (e.g., custom headers) and checksums may not persist through restore operations. SMBs should validate data integrity post-restore.
- Object key naming and structure: Buckets with millions of similarly prefixed object keys (e.g., /user/data/…) can experience slower restore times due to prefix-based performance limits.
- Storage class behavior: Standard and intelligent tiering grants immediate access post-restore, whereas Amazon S3 Glacier Deep Archive restores can take minutes to hours and may incur retrieval charges.
Pro tip: If a hospital archives monthly patient admission records in Amazon S3 Glacier Deep Archive, restoring that data for an audit or regulatory review can take up to 12 hours using standard retrieval methods. To avoid delays, healthcare providers should plan for compliance deadlines or consider faster options, such as expedited retrieval, when immediate access is required.
Visibility and monitoring:
All restore activity is tracked automatically:
- AWS CloudTrail logs every restore operation, including user, time, and resource details.
- AWS Backup Audit Manager can be configured to alert teams if restores are initiated outside approved windows or roles.
- Amazon CloudWatch can monitor restore performance, duration, and errors.
This visibility supports compliance audits, incident response investigations, and internal governance.
Security and compliance controls for Amazon S3 data backup
Amazon S3 backups managed through AWS Backup benefit from an enterprise-grade security architecture, without requiring SMBs to build these controls from scratch. Backups are encrypted by default, stored in isolated backup vaults, and governed by AWS Identity and Access Management (IAM) policies.
To enable secure backup and restore operations for Amazon S3, the following configurations are essential:
- Apply least-privilege IAM policies to restrict who can initiate, manage, or delete backups.
- Audit all role assumptions and changes using AWS CloudTrail for traceability.
- Service roles must include AWSBackupServiceRolePolicyForS3Backup and AWSBackupServiceRolePolicyForS3Restore.
If these permissions are missing, administrators must attach them to the relevant roles in the AWS Identity and Access Management (IAM) console. Without proper permissions, AWS Backup cannot access or manage S3 backup operations.
For example, a healthcare SMB can limit restore permissions to specific compliance officers while restricting developers from accessing backup vaults.
Compliance alignment:
AWS Backup integrates with multiple AWS services to support regulatory compliance:
- AWS Backup Audit Manager tracks backup activity and compares it against defined policies (e.g., retention duration, frequency).
- Tag policies, enforced via AWS Organizations, ensure every bucket requiring backup is appropriately labeled and included in backup plans.
- AWS CloudTrail records all actions related to backup creation, modification, or restore.
This is especially critical for regulated sectors, such as healthcare, where HIPAA compliance requires demonstrable evidence of data retention and access controls.
Long-term backup planning and cost control for Amazon S3 data backup
For SMBs operating in cost-sensitive and regulated industries like healthcare, optimizing Amazon S3 backup configurations goes beyond basic data protection. AWS Backup enables teams to align storage, retention, and recovery strategies with long-term operational and financial goals.
Cost control strategies:
A well-defined backup lifecycle reduces unnecessary spend and simplifies audit-readiness:
- Storage tier transitions: Configure AWS Backup lifecycle policies to automatically shift older backups to lower-cost storage classes such as Amazon S3 Deep Archive. For example, archived patient imaging data not accessed in 12 months or more can be moved to Amazon S3 Deep Archive to reduce storage costs.
- Retention policy tuning: Fine-tune recovery point retention to align with regulatory requirements. Avoid over-retention of daily snapshots that inflate costs without increasing recovery value.
- Tag-based billing insights: Apply tags (e.g., Department=Finance, Retention=30d) across backup plans to track and attribute storage usage. This helps identify high-cost data categories and prioritize optimization.
Long-term strategy alignment:
Backup configurations should map to business continuity targets and evolving IT strategy:
- Match to RPO/RTO requirements: Critical systems (e.g., electronic health records, financial data) may require daily or real-time recovery points, while less critical workloads (e.g., development logs) may tolerate longer recovery windows.
- Integrate with DR planning: Amazon S3 data backups should be part of a broader disaster recovery plan that includes cross-region replication and test restores during scheduled DR simulations.
- Monitor and audit at scale: Utilize Amazon CloudWatch or AWS Backup Audit Manager to track backup status, identify anomalies, and verify policy enforcement over time.
AWS Advanced Partners, such as Cloudtech, can help SMBs implement right-sized, cost-effective backup strategies from day one. For SMBs with lean teams, this eliminates guesswork, ensuring both financial efficiency and operational reliability in the long term.
How does Cloudtech support secure, scalable Amazon S3 data backup for SMBs?
As an AWS Advanced Tier Partner, Cloudtech helps SMBs implement secure, compliant, and automated Amazon S3 backups using AWS Backup. The approach is outcome-driven, audit-ready, and tailored to SMB constraints.
- Tailored setup and configuration: Cloudtech begins by validating prerequisites, including S3 Versioning, IAM roles, and encryption keys. It then configures automated backup plans with clear schedules, retention rules, and vault settings.
- Resilient recovery strategies: For SMBs in regulated sectors like healthcare, Cloudtech sets up point-in-time recovery and cross-account restores. Backup workflows are tested to support fast recovery from ransomware, data corruption, or accidental deletion.
- Continuous compliance and visibility: Utilizing tools such as AWS Backup Audit Manager, Amazon CloudWatch, and AWS CloudTrail, Cloudtech provides SMBs with real-time visibility into backup operations and policy enforcement. This ensures readiness for HIPAA, PCI, and other audits without manual tracking.
- Faster time-to-value with packaged offerings: Cloudtech offers structured backup enablement packages with defined timelines and assumptions. These accelerate implementation while maintaining governance, cost efficiency, and scale-readiness.
The effectiveness of these offerings has helped many SMBs set up their Amazon S3 data. In one instance, a mid-sized healthcare diagnostics company needed to meet HIPAA data retention standards while preparing for a regional expansion. Cloudtech implemented AWS Backup for Amazon S3 with point-in-time recovery, periodic archiving to Amazon S3 Glacier Deep Archive, and detailed policy enforcement across accounts.
The result: The organization now runs automated backups with complete audit visibility, cross-region protection, and recovery workflows tested quarterly, all without expanding their internal IT headcount.
Wrapping Up
For small and mid-sized businesses, protecting Amazon S3 data isn’t just about compliance. It’s about maintaining operational continuity, ensuring security, and fostering long-term resilience. AWS Backup provides centralized control, automation, and policy enforcement for what was previously a manual and fragmented process.
With the proper implementation, SMBs can ensure point-in-time recovery, streamline audit readiness, and scale backups without increasing overhead. Cloudtech streamlines this process by helping businesses configure, test, and optimize Amazon S3 data backups using proven AWS tools, making it faster and easier.
Whether you're just starting out or looking to upgrade your legacy backup workflows, Cloudtech provides a secure, compliant, and future-ready foundation for your cloud data. Get started now!
FAQs
1. Why should SMBs use AWS Backup instead of manual S3 backup methods?
Manual backups often lack consistency, automation, and compliance alignment. AWS Backup offers centralized policy management, encryption, lifecycle control, and point-in-time recovery, all critical for reducing risk and meeting regulatory standards.
2. What setup steps are required before enabling S3 backups?
Amazon S3 Versioning must be enabled. You’ll also need the appropriate IAM roles with AWS-managed policies (AWSBackupServiceRolePolicyForS3Backup and ...ForS3Restore). Cloudtech helps validate and automate this setup to avoid misconfiguration.
3. Can backups be scheduled across accounts and regions?
Yes. AWS Backup supports cross-account and cross-region backup and restore, but they require specific role permissions. Cloudtech helps SMBs configure secure, compliant multi-account strategies using AWS Organizations.
4. How can Cloudtech help with audit and compliance?
Cloudtech configures tools like AWS Backup Audit Manager, Amazon CloudWatch, and AWS CloudTrail to track backup activity, flag deviations, and maintain audit logs. This reduces manual overhead and simplifies regulatory reporting (e.g., HIPAA, PCI).
5. What happens if backup storage costs increase over time?
Cloudtech sets up lifecycle transitions to move backups to lower-cost tiers like Amazon Glacier Deep Archive. They also implement tagging and reporting to monitor storage spend and right-size backup strategies as your business grows.

Get started on your cloud modernization journey today!
Let Cloudtech build a modern AWS infrastructure that’s right for your business.