This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
Modernize your cloud. Maximize business impact.
Consider a growing SaaS company deploying a new feature using AWS Lambda to streamline part of its user workflow. But soon after launch, unexpected behavior surfaced in production. The codebase wasn’t changed, but the function didn’t execute as expected. After a deep dive, the issue is traced back to a simple but critical oversight: a misconfigured environment variable.
For many small and mid-sized businesses (SMBs) adopting serverless on AWS, environment variables in Lambda often fly under the radar—until they don’t. They control how functions connect to services, manage API keys, and handle environment-specific logic. When managed well, they reduce code duplication and speed up deployments. When overlooked, they can introduce bugs that are hard to trace.
This guide provides SMB teams with a practical understanding of AWS Lambda environment variables. From secrets management to debugging strategies, it offers best practices to help teams avoid common missteps and build more reliable serverless applications from the start.
Key takeaways
- Environment variables enable dynamic configuration: Lambda environment variables let businesses change runtime behavior, like API endpoints, feature flags, or logging levels.
- Security starts with proper encryption and access control: AWS automatically encrypts variables using KMS, but using customer-managed keys and IAM least-privilege policies provides stronger protection for sensitive data.
- Tools like AWS Secrets Manager and Parameter Store are better for secrets: Storing credentials directly in environment variables can be risky. Use AWS-native secret managers for secure storage, audit trails, and automatic rotation.
- The Serverless Framework simplifies multi-environment deployments: With stage-specific overrides, secret references, and version-controlled configs, teams can manage complex setups cleanly across dev, staging, and production.
- Following naming conventions and validation improves stability
Clear variable naming, environment-specific separation, and startup validation reduce misconfigurations and deployment issues, especially in growing teams.
What are AWS Lambda environment variables?
AWS Lambda environment variables are key-value pairs used to store configuration data outside of the function code. These variables live within the Lambda execution environment and are accessible via standard access methods (like process.env in Node.js or os.environ in Python), depending on the runtime.
By keeping configuration separate from code, environment variables allow teams to modify runtime behavior without redeploying the function. This is a major advantage for SMBs looking to reduce operational overhead and deployment risk.
Why environment variables matter: Hardcoding configuration values like API keys, database credentials, or feature flags into function code can lead to:
- Increased redeployment cycles for minor changes
- Higher risk of leaking sensitive values through version control
- Reduced ability to reuse code across dev, test, and production environments
Using environment variables helps avoid these issues by enabling:
- Dynamic runtime configuration
- Cleaner separation of code and environment
- Secure, encrypted storage of sensitive values via AWS Key Management Service (KMS)
Here’s how AWS Lambda handles them:
- Immutable at runtime: Environment variables are loaded once per container lifecycle, during the initialization phase. They remain constant throughout the life of that execution environment.
- Encrypted at rest: AWS encrypts environment variables using AWS KMS, ensuring that sensitive data is protected even if access is misconfigured.
- Scoped per version or alias: Businesses can assign different environment variables to each version or alias of their Lambda function, helpful for environment-specific deployments.
Using Lambda environment variables effectively allows SMBs to improve deployment agility, security posture, and operational consistency, especially as serverless architectures scale across teams or environments.

How does AWS Lambda store and load environment variables?
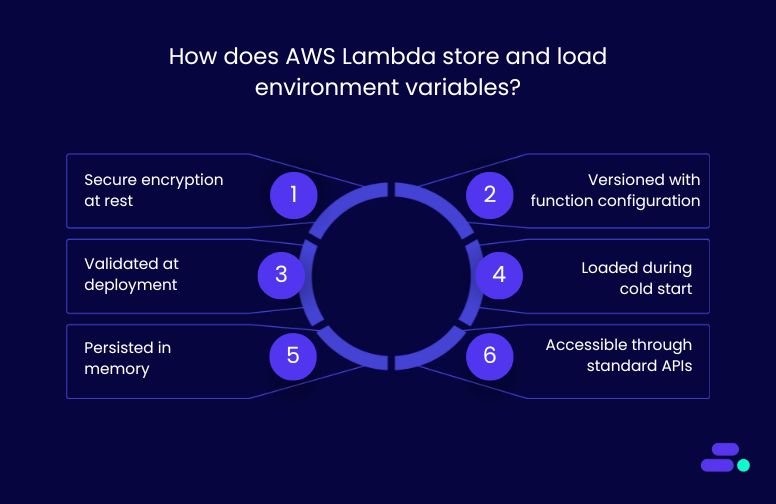
AWS Lambda uses a secure and efficient process to store and load environment variables, enabling functions to behave differently across environments without modifying code. This approach ensures both security and performance throughout the function lifecycle.
1. Secure encryption at rest: Lambda stores all environment variables as part of the function’s configuration and encrypts them using AWS Key Management Service (KMS). This can be either an AWS-managed key or a customer-managed KMS key. These encrypted values are stored with other function settings such as runtime, memory allocation, and timeout duration.
2. Versioned with function configuration: Each time a function is published as a new version, the environment variables are included as part of that version’s configuration. This allows teams to roll back safely or run multiple versions of the same function with different configurations (e.g., dev vs. prod), without affecting stability.
3. Validated at deployment: Lambda automatically validates environment variable syntax and enforces a maximum total size of 4KB per function. This includes all key-value pairs and formatting. If the limit is exceeded or formatting is invalid, the deployment is rejected before it reaches production.
4. Loaded during cold start: When a new execution environment is initialized (a cold start), Lambda decrypts the environment variables using KMS and injects them into the container. This process happens once, before any code is executed, ensuring variables are available from the start.
5. Persisted in memory: After a cold start, environment variables are cached in memory for the duration of the container’s lifecycle. During warm invocations, Lambda does not need to re-decrypt or reload them, improving performance without compromising security.
6. Accessible through standard APIs: Environment variables are made available through standard language-specific APIs:
- process.env in Node.js
- os.environ in Python
- Environment.GetEnvironmentVariable() in .NET
This method allows developers to configure functions dynamically without changing code, reducing deployment cycles and supporting consistent behavior across multiple environments.
How to set environment variables in AWS Lambda?
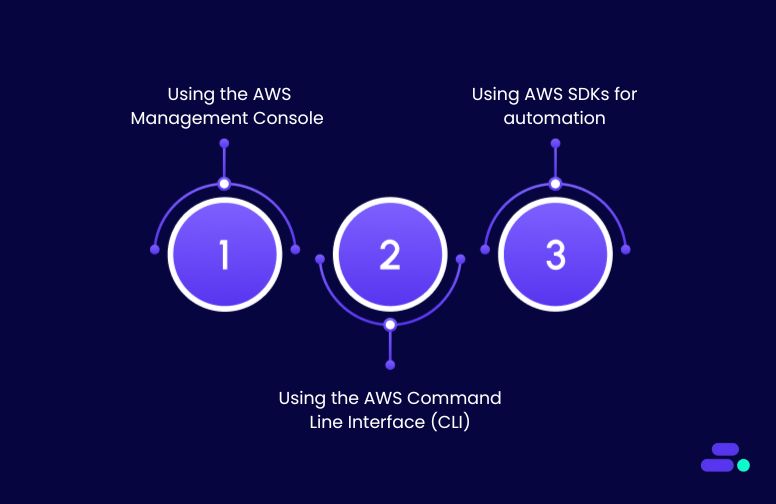
Environment variables in AWS Lambda can be configured using three main methods, via the AWS Console, CLI, or SDKs, depending on a team’s technical workflow and scale. Each method allows developers to separate runtime configuration from code, streamlining updates without redeploying functions.
1. Using the AWS Management Console
The Console is ideal for smaller teams or quick configuration changes. It provides a user-friendly interface to define up to 50 key-value pairs per function.
- The UI enforces naming rules (alphanumeric characters, underscores, and hyphens).
- A visual indicator tracks usage against the 4KB environment variable size limit.
- Developers can use built-in options to encrypt variables with AWS KMS, selecting region-specific keys.
- JSON import/export makes it easy to reuse environment configurations across multiple functions.
Use case: A healthcare provider running a patient appointment scheduling system on AWS Lambda needs to switch between staging and production API endpoints (e.g., for an EHR system or SMS notification service). Instead of modifying and redeploying the function code, the developer updates the API_URL and FEATURE_TOGGLE_SMS environment variables directly in the AWS Console. This allows the team to change behavior instantly, such as enabling SMS reminders for patients, without code changes or downtime, ensuring faster iteration and reduced operational risk.
2. Using the AWS Command Line Interface (CLI)
The CLI suits engineering teams who manage infrastructure through scripts or version-controlled deployments.
- Environment variables are updated using the update-function-configuration command.
- Only full replacements are allowed. Existing variables are overwritten, not merged.
- Supports configuration via inline input or external JSON files using file://, which helps standardize deployments across stages (e.g., dev, test, prod).
Example:
aws lambda update-function-configuration \
--function-name myFunction \
--environment Variables="{KEY1=value1,KEY2=value2}"
Use case: An SMB operating across development, staging, and production environments, each in separate AWS accounts, needs consistent Lambda configuration for settings like LOG_LEVEL, API_KEY, and REGION_ID. Instead of manually entering these values in each account, the team uses pre-approved JSON files containing environment variable definitions. These files are applied via the AWS CLI or deployment scripts during CI/CD runs, ensuring all environments are configured identically. This approach minimizes human error, speeds up deployments, and maintains compliance with internal governance policies.
3. Using AWS SDKs for automation
For advanced use cases and CI/CD pipelines, the AWS SDKs (e.g., Boto3 for Python, AWS SDK for JavaScript) allow full programmatic control over Lambda environment variables.
- The UpdateFunctionConfiguration API is used to update variables as part of deployment automation.
- SDKs manage authentication, retries, and error handling, reducing the need for custom error logic.
- Teams can build templated variable sets based on client, region, or environment.
Example (Python):
import boto3
lambda_client = boto3.client('lambda')
lambda_client.update_function_configuration(
FunctionName='myFunction',
Environment={'Variables': {'STAGE': 'prod'}}
)
Use case: An SMB software vendor deploying a multi-tenant SaaS solution can use Lambda environment variables to inject client-specific configurations, such as API credentials, feature flags, or tenant identifiers, at deploy time. During CI/CD, the deployment pipeline programmatically updates the Lambda function’s environment based on each customer’s config.
This enables the same Lambda codebase to serve multiple clients securely and efficiently, without hardcoding or redeploying for each tenant. It simplifies onboarding, reduces maintenance, and ensures isolation between customer environments.
These approaches allow SMBs to manage Lambda configurations dynamically, reduce redeployments, and scale operations without introducing complexity. Whether the team prefers a UI-driven approach or automated pipelines, AWS provides flexible tools to meet different operational needs.

Managing AWS Lambda environment variables with the Serverless Framework
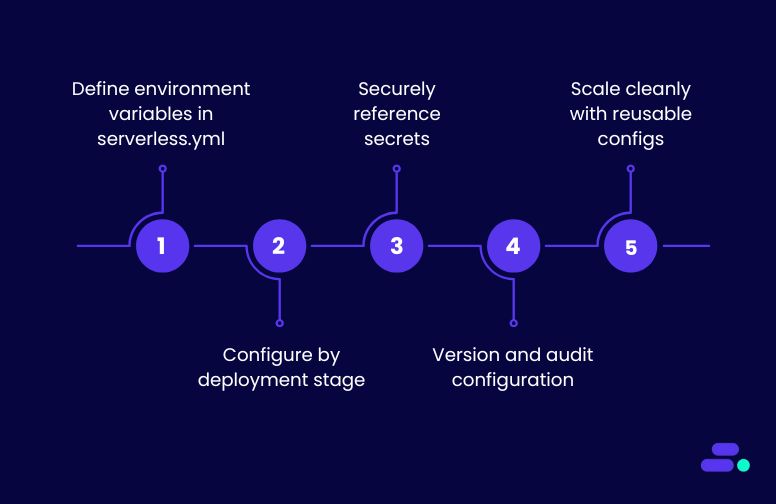
The Serverless Framework enables structured, stage-aware, and secure management of AWS Lambda environment variables using Infrastructure as Code. It allows teams to define, version, and deploy configurations cleanly across environments without embedding secrets in code or relying on manual edits.
Here’s how it works:
1. Define environment variables in serverless.yml
Environment variables can be scoped globally (for all functions) or per function. Variables can be hardcoded, pulled from local .env files, or injected via CI/CD.
provider:
name: aws
environment:
DB_HOST: ${env:DB_HOST}
functions:
myFunction:
environment:
LOG_LEVEL: debug
${env:DB_HOST} pulls values from the machine’s environment or deployment pipeline.
2. Configure by deployment stage
Use the --stage flag to inject different values per environment (e.g., dev, staging, prod). Stage-specific configurations are managed using file overrides or conditional logic.
serverless deploy --stage prod
Businesses can maintain per-stage variable files (env.prod.yml, env.dev.yml) and reference them using the file() directive in serverless.yml.
3. Securely reference secrets
Instead of hardcoding sensitive values, reference AWS Secrets Manager or SSM Parameter Store:
environment:
DB_PASSWORD: ${ssm:/prod/db/password~true}
The ~true flag ensures the value is decrypted. Secrets remain outside version control and are encrypted at rest.
4. Version and audit configuration
Since serverless.yml is part of source control, teams get full version history and rollback capability. This promotes consistent deployments and improves collaboration between dev and ops teams.
5. Scale cleanly with reusable configs
For large projects, use separate serverless.yml files per stage or modularize config using serverless.ts or YAML imports:
custom: ${file(./config.${opt:stage, 'dev'}.yml)}
This keeps configuration DRY while supporting stage-specific overrides.
By using the Serverless Framework, SMBs can manage Lambda environment variables securely, scalably, and with full automation, minimizing misconfigurations and accelerating deployment workflows.
How to secure AWS Lambda environment variables?
When Lambda functions handle sensitive values like database passwords or API tokens, securing environment variables is essential. Misconfiguration can lead to data exposure or compliance violations. AWS offers several tools to help, if used correctly.
1. Encryption with AWS KMS: All Lambda environment variables are encrypted at rest using AWS Key Management Service (KMS). By default, AWS uses its managed keys, but for sensitive workloads, SMBs should use customer-managed keys for better control. This allows teams to define key-specific IAM policies, track usage with CloudTrail, and enforce rotation policies. The KMSKeyArn field in the Lambda configuration lets the teams specify the custom key. No application code changes are required, as decryption is handled during function startup.
2. Storing secrets securely: Avoid embedding sensitive data directly in environment variables. Instead, store secrets in AWS Secrets Manager or Systems Manager Parameter Store. These services support fine-grained access control, logging, and automatic rotation (especially for RDS). Lambda functions can reference these secrets via ARNs in environment variables and retrieve them at runtime using the AWS SDK.
Example:
DATABASE_PASSWORD_SECRET_ARN: arn:aws:secretsmanager:us-east-1:...
3. IAM-based access control: Limit who and what can access secrets or decrypt environment variables. Use least-privilege IAM roles that restrict access to specific secrets or KMS keys. This helps isolate workloads and reduces blast radius in case of compromise. Use tools like IAM Access Analyzer to audit permissions regularly.
Combining encryption, secret management, and tight access control allows SMBs to ensure that Lambda-based applications handle sensitive configuration securely without sacrificing agility.
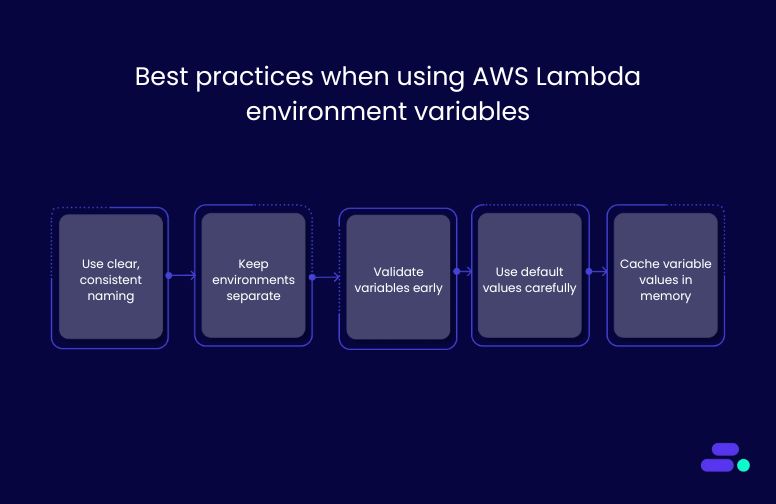
Best practices when using AWS Lambda environment variables
Environment variables in AWS Lambda provide a simple but powerful way to manage configuration without modifying code. By storing key values like database URLs, API keys, feature flags, or timeout settings outside the application logic, teams can run the same code across different environments with varying configurations.
For SMBs running lean teams or managing multiple client deployments, this separation of config from code offers speed and flexibility. There is no need to redeploy just to update a setting. Lambda environment variables are injected during the container’s cold start, made available as part of the runtime’s native environment (e.g., process.env in Node.js or os.environ in Python), and cached throughout the function's lifecycle for consistent performance.
However, poor environment variable practices can lead to runtime errors, security gaps, or debugging headaches. That’s why teams must structure, validate, and scope environment variables thoughtfully. The following best practices ensure the Lambda functions stay secure, scalable, and maintainable as the business and workloads grow.
1. Use clear, consistent naming: Stick to uppercase, underscore-separated names like PAYMENTS_API_KEY or ORDERS_DB_URL. Prefix variables with the service or app name (e.g., ORDERS_DB_URL) to avoid confusion or conflicts in shared environments.
2. Keep environments separate: Don’t mix dev, staging, and prod variables. Use environment-specific names like DB_URL_PROD vs. DB_URL_DEV. This prevents accidental access to production data during testing.
3. Validate variables early: Add startup checks to confirm that all required environment variables are present and correctly formatted. Catching misconfigurations upfront avoids runtime failures and debugging delays.
4. Use default values carefully: Set safe defaults only for non-sensitive settings, like timeouts or feature flags. Never default values like passwords or API keys; always set those explicitly.
5. Cache variable values in memory: Instead of re-reading or re-parsing environment variables on every function call, load them once during initialization. This improves performance and reduces compute costs, especially for high-frequency invocations.
These practices help SMBs build secure, reliable Lambda functions that are easier to scale and maintain.

How Cloudtech helps SMBs implement secure AWS Lambda configuration
Misconfigured environment variables can lead to broken deployments, leaked secrets, and unstable behavior across environments. Cloudtech helps small and mid-sized businesses solve these problems by designing serverless systems that prioritize secure, stage-aware configuration from the start.
Each of Cloudtech’s core services supports this goal:
- Application modernization: Cloudtech transforms monolithic or legacy applications into AWS-native systems where environment variables are managed dynamically. This ensures clean separation between code and configuration, enabling safer deployments and easier multi-environment support without manual rewrites.
- Infrastructure resiliency: Cloudtech’s infrastructure solutions embed best practices for runtime configuration, including encrypted environment variables, stage-specific resource isolation, and consistent IAM scoping. Teams gain better control over what their functions access.
- Data modernization: Cloudtech replaces fragile in-code credentials with centralized secret management using AWS Secrets Manager and Parameter Store. This reduces the risk of exposure, supports key rotation, and integrates cleanly with Lambda environment variable references.
- Generative AI: For teams building AI-powered features on Lambda, Cloudtech helps structure workloads with environment-specific tuning, model versioning, and secure access to APIs or feature flags, all configured safely outside the codebase.

Conclusion
Effective Lambda environment variable management depends on clear naming, strict environment separation, and secure configuration handling. When supported by automation and secret management, these practices reduce errors, improve consistency, and make serverless deployments easier to scale and manage.
For SMBs building on AWS, getting this right is key to long-term stability and efficiency. Cloudtech helps teams implement these best practices through application modernization, infrastructure design, secure data handling, and automation support. Contact us to build safer, more manageable serverless systems.
FAQ’s
1. How do businesses deploy environment variables in Lambda?
Environment variables in AWS Lambda can be deployed using the AWS Management Console, AWS CLI, SDKs, or Infrastructure-as-Code tools. Values are stored as key-value pairs and attached to the function’s configuration during deployment or update processes.
2. Does AWS Lambda encrypt environment variables?
Yes, AWS Lambda encrypts all environment variables at rest using AWS Key Management Service (KMS). Developers can use either AWS-managed keys or customer-managed keys to control access, enable auditing, and support encryption policies required for compliance and data security.
3. How to get environment variables in Lambda Java?
Lambda functions written in Java can access environment variables using System.getenv("VARIABLE_NAME"). These values are available during function initialization and remain accessible throughout the execution lifecycle, allowing developers to configure runtime behavior without modifying or redeploying function code.
4. How do I set environment variables in AWS?
Environment variables can be set in AWS Lambda through the Management Console, AWS CLI, or SDKs. Each method requires defining key-value pairs that meet naming constraints and fit within the total 4KB size limit for all environment variables combined.
5. What is a Lambda execution environment?
The Lambda execution environment is a managed runtime that hosts function code in an isolated container. It includes system libraries, runtime binaries, and environment variables, and it handles code initialization, invocation processing, and resource lifecycle management across cold and warm starts.

Get started on your cloud modernization journey today!
Let Cloudtech build a modern AWS infrastructure that’s right for your business.