This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
Modernize your cloud. Maximize business impact.
Cyberattacks are getting more frequent and more expensive. IBM’s most recent cloud security study reports that the average cost of a data breach has reached USD 4.35 million. In response, over half of global organizations are planning to boost investments in threat detection, incident response, and cloud security tools throughout 2025.
For small and mid-sized businesses (SMBs) in sectors like healthcare and fintech, the stakes are even higher. All it takes is one misconfigured access policy or exposed resource to trigger a costly security incident or regulatory fallout.
The good news is that AWS provides a flexible foundation for implementing strong, scalable defenses if the right controls are in place. That’s why more growth-focused SMBs are working with AWS partners like Cloudtech to build secure, compliant environments from the ground up.
This article walks through the most important AWS cloud security practices for 2025, and how to implement them in a way that aligns with the risk profile, industry standards, and long-term goals.
Key takeaways:
- Security is not a one-time setup; it’s a continuous discipline: AWS provides the tools, but SMBs must define clear strategies and enforce controls as environments evolve.
- Misconfigurations are the biggest threat, and the easiest to prevent: With IAM policies, automated monitoring, and least privilege access, most breaches can be avoided before they happen.
- Smart automation is force multiplication for small teams: Tools like AWS Config, Amazon GuardDuty, and AWS Systems Manager help SMBs scale security efforts without scaling headcount.
- Cloud-native security doesn’t mean complexity; it means control: When implemented correctly, AWS makes it easier for SMBs to enforce governance, meet compliance, and respond quickly to threats.
Why do SMBs need a security-first AWS strategy?
AWS operates on a shared responsibility model, meaning Amazon secures the infrastructure, while customers are accountable for securing their data, configurations, and access policies.
Without a clear, well-documented strategy, SMBs often face preventable risks like open Amazon S3 buckets, over-permissive IAM roles, or outdated security groups. These gaps aren’t just technical oversights. They’re business liabilities that can lead to data breaches, compliance violations, and lost customer trust.
For industries like healthcare and fintech, the pressure is even greater. Regulations such as HIPAA and PCI-DSS require strict controls over data access, encryption, and audit trails. Falling short, even unintentionally, can result in heavy fines and reputational damage.
Establishing cloud security best practices from the start helps SMBs:
- Stay compliant with evolving industry regulations
- Reduce the risk of misconfiguration and unauthorized access
- Gain visibility into their cloud environment through monitoring and alerting
- Build a strong foundation that scales with business growth
For SMBs having limited IT teams or expertise, AWS partners like Cloudtech can help them implement the necessary AWS cybersecurity strategies in a way that fits their team size, risk profile, and industry requirements.
How can SMBs implement a security-first AWS strategy?
Unlike large enterprises, most SMBs don’t have the luxury of dedicated security teams or redundant systems. They move fast, manage lean teams, and prioritize innovation, especially in sectors like healthcare and fintech where demand is high and competition is fierce. Cloud platforms like AWS help level the playing field, but only if security keeps pace with growth.
In the early stages, it’s natural to focus on performance and delivery. But as environments expand with new workloads, more users, and tighter compliance expectations, security gaps can quietly emerge. Maybe a former contractor still has admin access. Maybe a key data store isn’t encrypted. They’re common side effects of scaling without a structured security plan. And when audits or incidents do arise, they tend to hit smaller businesses harder.
A security-first strategy helps SMBs get ahead of these risks. It brings clarity to what needs protecting, who needs access, and how to automate guardrails that support rather than slow down the business.
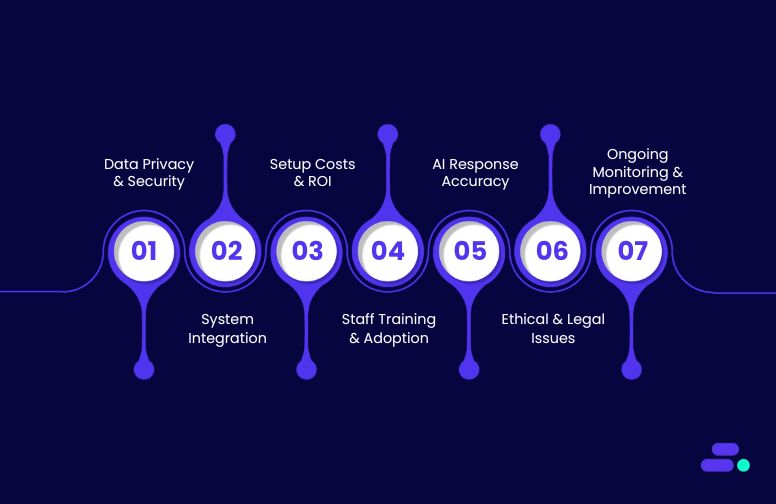
The following step-by-step strategy outlines how SMBs can achieve this using AWS-native tools, without overextending their teams or budgets.
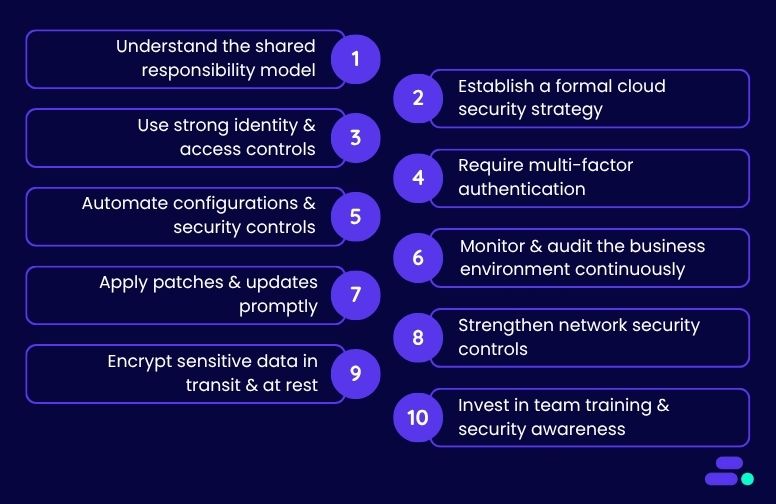
1. Understand the shared responsibility model
Security in the cloud is a shared model. AWS secures the infrastructure of the cloud, while businesses are responsible for what they put in it. That includes user access, data classification, encryption settings, compliance configurations, and software-level protections. For SMBs in fintech and healthcare, this model directly impacts how they approach risk management, incident response, and audit readiness.
Real-world scenario: A healthcare startup launches a patient portal on Amazon EC2, assuming AWS manages encryption and access controls by default. However, without explicitly configuring IAM policies, enabling encryption at rest for EBS volumes, or setting up Amazon CloudTrail for audit logs, the environment remains exposed. This violates HIPAA and risks reputational damage in the event of a breach.
To operationalize the shared responsibility model:
- Map responsibilities by service: Use the AWS Shared Responsibility Model and align it with business architecture. For example, AWS manages Amazon RDS’s physical infrastructure. The SMB must enable encryption, rotate keys, and configure IAM policies for database access.
- Assign internal ownership: Create a responsibility matrix that maps each AWS service (e.g., Amazon S3, Amazon EC2, Amazon RDS, AWS Lambda) to a specific team or role, such as DevOps, compliance, or security engineering. This prevents accountability gaps.
- Standardize configuration baselines: Use AWS Config rules and AWS CloudFormation templates to enforce consistent security controls across environments (e.g., block public Amazon S3 buckets, enforce MFA for IAM users).
- Review regularly: As the stack evolves, review ownership and configuration at least quarterly to ensure no drift has occurred, especially after team changes, rapid scaling, or vendor integrations.
Understanding this model ensures that no one assumes AWS “has it covered” when, in reality, critical responsibilities like encryption, access control, and compliance reporting rest squarely on the business side of the fence.
2. Establish a formal cloud security strategy
Once the lines of responsibility are clear, the next priority is developing a formal cloud security strategy. Many SMBs, especially in regulated sectors like healthcare and fintech, spin up AWS environments quickly to meet demand, but without a guiding framework, risk and compliance gaps grow unnoticed.
A security strategy ensures consistency and accountability across teams, especially as infrastructure scales or regulatory pressure increases.
2. Establish a formal cloud security strategy
- Risk tolerance: Clarify how much risk the business can accept when choosing between speed, cost, and control. This informs architecture and vendor decisions.
- Compliance alignment: Map applicable standards like HIPAA, PCI-DSS, or SOC 2 to AWS configurations. For example, enable Amazon S3 encryption, enforce logging, and use private subnets for sensitive workloads.
- Team roles and ownership: Assign responsibility for identity, monitoring, key management, and remediation to avoid gaps during day-to-day ops or audits.
- Incident response workflows: Document how the team will detect and respond to threats, using AWS-native tools like Amazon GuardDuty, AWS CloudTrail, and AWS Systems Manager.
This document doesn’t need to be perfect from day one, but it does need to exist and evolve over time. Treat it as the team’s north star for scaling securely and making decisions that stand up to audits, not just deadlines.
3. Use strong identity and access controls
With a strategy in place, the next layer is precise access control. Identity and access missteps, especially overly broad permissions, are among the top causes of cloud breaches in SMB environments.
Using AWS Identity and Access Management (IAM), teams can enforce least-privilege access by:
- Defining role-based policies that grant only what’s needed per function. For example, a billing user shouldn’t have access to EC2 instances, and dev teams shouldn’t see production secrets.
- Disabling root account use for anything beyond initial setup. Instead, use federated identities or IAM roles with MFA.
- Eliminating long-lived credentials by rotating access keys. Use AWS IAM Identity Center (formerly AWS SSO) for session-based logins tied to the identity provider (e.g., Okta, Azure AD).
A healthcare SMB using shared admin credentials across AWS services may be compliant on paper but vulnerable in practice. Granular IAM policies, tied to monitored roles, help contain blast radius and support incident forensics if something goes wrong.
4. Require multi-factor authentication (MFA)
Even with tight IAM controls, stolen or reused credentials remain a top threat, especially in environments where small teams juggle multiple roles. That’s where multi-factor authentication (MFA) becomes critical.
MFA ensures that access requires something more than just a password. It should be non-negotiable for:
- Root users
- Admin and DevOps roles
- Any user interacting with production data or infrastructure
AWS makes implementation straightforward through virtual MFA apps (like Google Authenticator or Authy), hardware tokens, or integration with SSO platforms that support MFA enforcement.
For an SMB handling patient records or financial data, a single compromised credential without MFA could expose the entire AWS account. Enforcing MFA minimizes this risk and adds resilience against phishing, social engineering, or credential stuffing attempts.

5. Automate configurations and security controls
Once identity and access layers are secured, the next priority is eliminating manual configuration drift.
For SMBs, especially those with lean IT teams, automation isn’t just a time-saver. It’s a security multiplier. By using AWS-native tools, teams can standardize deployments, enforce guardrails, and respond to threats without delay.
Key tools and approaches include:
- AWS Config for real-time compliance checks against custom or managed security baselines, flagging issues like open ports or unencrypted volumes as they happen.
- AWS CloudFormation or Terraform to provision infrastructure in a secure, repeatable way, so dev teams don’t accidentally deploy with misconfigured security groups or public access.
- AWS Systems Manager and Lambda to automate patching, log reviews, and even auto-remediation for policy violations or failed audits.
In healthcare, for example, automation can help enforce HIPAA-aligned encryption and retention policies across resources. For fintech, it supports audit-readiness and reduces reliance on ad hoc scripts or manual checklists.
6. Monitor and audit the business environment continuously
Even well-automated environments need constant visibility. Threats evolve, workloads shift, and misconfigurations can creep in. For SMBs in sectors like healthcare and fintech, where downtime or data exposure can have legal and reputational consequences, real-time monitoring and auditing aren’t optional.
Fortunately, AWS offers integrated tools that make continuous oversight both achievable and scalable:
- Amazon GuardDuty delivers intelligent threat detection using machine learning to identify unusual patterns like port scanning, credential compromise, or data exfiltration attempts.
- AWS CloudTrail provides a detailed audit log of every API call, giving the team traceability for changes, critical for root cause analysis or compliance investigations.
- AWS Security Hub aggregates findings across AWS services, offering a unified dashboard to check alignment with frameworks like CIS Benchmarks, HIPAA, or PCI-DSS.
To stay effective, alerts must go beyond dashboards. Set up automated notifications for critical anomalies and establish ownership for reviewing, escalating, and responding to alerts. Small teams can also use third-party SIEM integrations or managed detection and response (MDR) services to extend coverage.
7. Apply patches and updates promptly
Security monitoring is only useful if it’s followed by action, and patching is one of the most critical. Unpatched systems remain one of the top causes of cloud breaches, especially when vulnerabilities are publicly known and easily exploitable.
For SMBs, falling behind on updates is often a bandwidth issue. But AWS provides tools to automate and streamline the process without disrupting operations:
- AWS Systems Manager Patch Manager allows teams to automate patching schedules for Amazon EC2 instances and on-premises hybrid environments.
- Compliance dashboards on AWS Systems Manager help track which systems are up to date and which require immediate attention.
- Maintenance windows on AWS Systems Manager can help apply patches during off-peak hours, minimizing service interruptions.
Make patching a priority for public-facing services, applications handling sensitive data, and any system tied to regulatory compliance. In healthcare and fintech, a missed patch could trigger an audit failure or data breach liability.
8. Strengthen network security controls
Once the workloads are patched and up to date, the next layer of defense is the network itself. Poorly configured network settings, like open ports or flat VPC architectures, can expose sensitive data to the internet or allow lateral movement if compromised.
To reduce the attack surface and enforce segmentation:
- Use Security Groups and Network ACLs to control inbound/outbound traffic at both the instance and subnet levels
- Replace public IPs with VPC endpoints to keep service traffic inside the AWS environment
- Deploy AWS WAF (Web Application Firewall) to block injection attacks, cross-site scripting (XSS), and other Layer 7 exploits
- Avoid open ports like 0.0.0.0/0 for SSH or RDP and use bastion hosts or Session Manager instead
For SMBs in healthcare or fintech, these network controls aren’t just good practice. They’re often required for regulatory compliance. Proactively auditing firewall rules, restricting access by IP or geography, and isolating workloads by function can significantly reduce the blast radius of any incident.
9. Encrypt sensitive data in transit and at rest
Encryption is a baseline requirement, not a bonus, especially for SMBs in healthcare or fintech where data privacy laws like HIPAA, PCI-DSS, or GLBA are non-negotiable. AWS makes encryption accessible, but it’s up to the team to configure and manage it correctly.
For data at rest, enable:
- SSE-S3 for server-side encryption in Amazon S3
- EBS encryption for volumes attached to EC2 instances
- RDS encryption for managed databases, ideally using Customer-Managed Keys (CMKs) via AWS Key Management Service (KMS)
For data in transit, always:
- Use TLS 1.2 or higher
- Manage certificates through AWS Certificate Manager (ACM) for secure HTTPS connections
- Avoid sending sensitive data over unencrypted channels, even between internal systems
Don’t stop at enabling encryption, also:
- Define key rotation schedules
- Enforce least-privilege policies for key access
- Monitor access logs for unusual activity around encryption resources
For SMBs, this ensures that even if other defenses fail, the most sensitive data remains unreadable and auditable, helping businesses stay compliant and protected at scale.

10. Invest in team training and security awareness
Technology alone doesn’t secure the cloud; people do. For SMBs, especially in high-stakes industries like healthcare and fintech, the weakest link is often user behavior, not tooling. A well-configured AWS environment can still be compromised if employees fall for phishing attempts or misconfigure permissions.
To build a security-first culture:
- Train every team member, from IT admins to frontline staff, on AWS security basics, password hygiene, MFA usage, and phishing recognition
- Utilize AWS Skill Builder learning paths or bring in certified AWS training partners like Cloudtech for hands-on workshops
- Run regular tabletop exercises and simulated incidents to test the team’s response readiness
Security awareness should be part of onboarding, reinforced during team meetings, and revisited as the environment evolves. Organizations that embed security into their day-to-day culture are not only better prepared to defend against attacks, but they also recover faster and maintain customer trust when incidents occur.
By following these practices, SMBs can build a compliant and scalable AWS environment.
How does Cloudtech help SMBs secure their cloud?
For small and mid-sized businesses, especially those in regulated sectors like healthcare and fintech, moving to AWS is just the first step. Security, uptime, and compliance must be intentionally designed. Cloudtech, an AWS Advanced Tier Services Partner, helps SMBs modernize their AWS environments with resilient, secure architectures that support long-term scalability without adding operational burden.
1. Building a secure and resilient cloud foundation
Cloudtech designs AWS-native environments that are fault-tolerant, cost-optimized, and compliance-ready. From AWS Control Tower governance and multi-AZ architectures to serverless infrastructure and automated monitoring with AWS CloudWatch, every layer is tailored to reduce risk and scale with the business.
2. Reducing downtime and strengthening disaster readiness
Using best practices in backup, disaster recovery, and chaos engineering, Cloudtech enables SMBs to maintain uptime even during outages or attacks. Solutions like active-active replication and automated failover ensure that systems stay online, while workshops and stress testing uncover vulnerabilities before they cause disruption.
3. Migrating intelligently and modernizing securely
Cloudtech handles end-to-end workload migration with minimal disruption, while ensuring each workload is re-architected for security, cost efficiency, and future growth. Post-migration, the environments are optimized for AI-readiness and regulatory compliance, positioning SMBs to use advanced AWS capabilities without added complexity.
Each engagement follows a structured five-phase approach—Engage, Discover, Align, Deliver, and Enable—ensuring every step aligns with the SMB’s goals, compliance needs, and internal capabilities.
Modernize with confidence, backed by AWS expertise
Migrating to AWS gives SMBs the tools to improve resilience, optimize costs, and scale faster. But true cloud success isn’t just about moving workloads. It’s about transforming how teams operate, innovate, and engage customers.
Cloudtech helps SMBs move beyond lift-and-shift with an AWS-native strategy designed around business outcomes. From automating operations and unlocking real-time insights to enabling AI-driven workflows, Cloudtech aligns cloud capabilities with goals, securely and efficiently.
For SMBs ready to break free from legacy limitations, Cloudtech delivers a proven path to modernization with deep AWS expertise, practical strategy, and long-term support.
Connect with Cloudtech to start the conversation.
FAQs
1. How can SMBs determine if their AWS environment is adequately secured?
Security maturity evolves with the business. Cloudtech helps SMBs assess their environment using AWS Security Hub benchmarks and custom KPIs such as identity sprawl, encryption coverage, and patch compliance. This allows organizations to continuously measure posture and prioritize remediation based on actual risk exposure.
2. What are the next steps after implementing MFA and IAM best practices?
Once foundational access controls are in place, the focus should shift to proactive threat detection and automated response. Cloudtech enables SMBs to deploy services like GuardDuty and Systems Manager Automation to detect anomalies and respond in real time, helping teams move from reactive to proactive security operations.
3. How can SMBs prevent security configurations from drifting over time?
Configuration drift often occurs as environments grow and change. Cloudtech mitigates this by implementing AWS Config and conformance packs that enforce predefined policies. Combined with Infrastructure as Code tools like CloudFormation, this ensures environments remain consistent, auditable, and secure at scale.
4. What should an SMB do immediately following a security incident in AWS?
The first priority is containment, isolating affected resources using IAM and VPC controls. Cloudtech helps SMBs build incident response playbooks that include forensic analysis with CloudTrail, root cause tracing, and automated remediation via Lambda. This shortens recovery time and helps teams close security gaps quickly.
5. Is advanced cloud security necessary if an SMB isn’t in a regulated industry?
Absolutely. Even without HIPAA or PCI obligations, SMBs are frequent targets due to limited defenses. Cloudtech aligns security controls to business value, not just compliance. This ensures customer data, core applications, and uptime are protected without overwhelming internal teams or over-investing in tools that don’t fit their scale.

Get started on your cloud modernization journey today!
Let Cloudtech build a modern AWS infrastructure that’s right for your business.